Oracle WebLogic Server is an application server that is primarily designed to develop, deploy, and manage enterprise applications based on Java EE and Jakarta EE standards.It serves as a critical component of Oracle’s Fusion Middleware, which provides a reliable and scalable environment.Aqua Nautilus researchers recently [discovered](https://www.aquasec.com/blog/hadooken-malware-targets-weblogic-applications/) that a new Linux malware dubbed ‘Hadooken’ is actively exploiting Oracle Weblogic servers.**Linux Malware Exploiting Weblogic Servers**———————————————The Hadooken malware targets [Oracle WebLogic servers](https://cybersecuritynews.com/oracle-weblogic-server-vulnerability/) by exploiting the weak admin credentials for initial access.**It deploys two key components, and here below, we have mentioned all of them:-*** A cryptominer (MD5: 9bea7389b633c331e706995ed4b3999c)* Tsunami malware (MD5: 8eef5aa6fa9859c71b55c1039f02d2e6)The attack utilizes shell (‘c’) and Python (‘y’) scripts to download and execute payloads by preferring non-persistent directories like /tmp.`Decoding Compliance: What CISOs Need to Know — `[Join Free Webinar](https://webinars.indusface.com/decoding-compliance-what-cisos-need-to-know/register?utm_source=blog-cta&utm_medium=referral&utm_campaign=2024-september-decoding-compliance-what-cisos-need-to-know)The cryptominer is dropped as ‘/usr/bin/crondr’, ‘/usr/bin/bprofr’, and ‘/mnt/-java’, while Tsunami uses a random filename in /tmp.Persistence is maintained through cron jobs created in /etc/cron.-/- with varying frequencies. 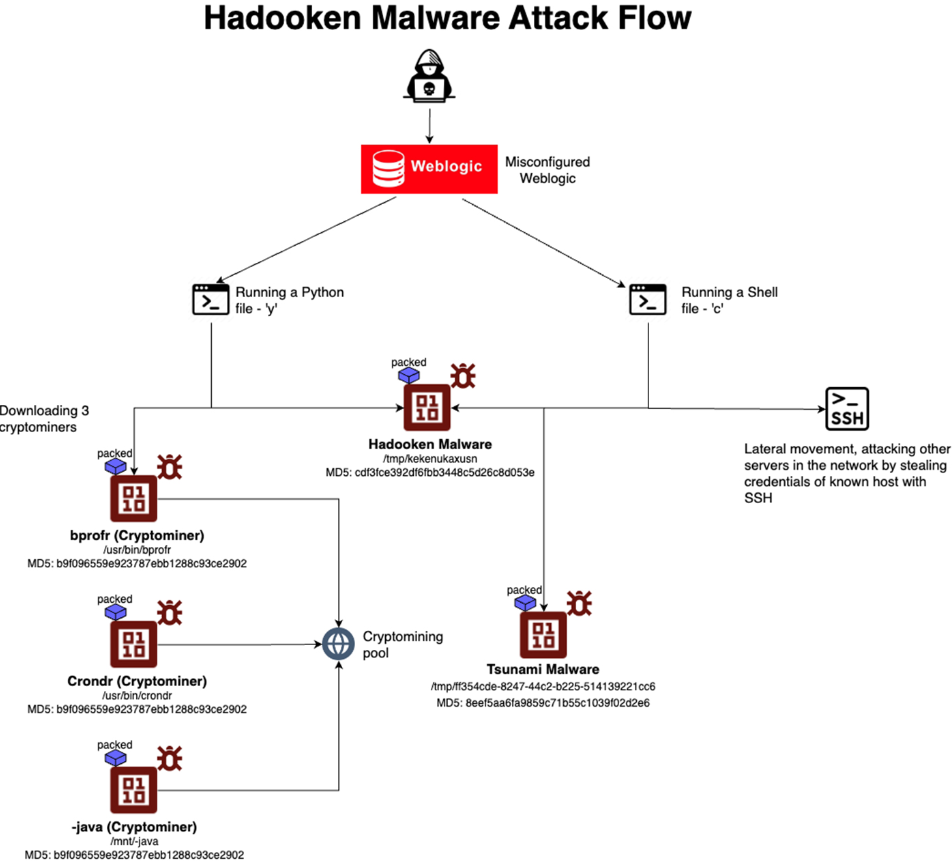 Attack flow (Source — Aquasec)For lateral movement, it searches for SSH data in various directories. The malware employs evasion techniques, including base64 encoding, log clearance, and process masquerading.Associated IP addresses 89.185.85.102 and 185.174.136.204 link to potential ransomware distribution (Mallox MD5: 4a12098c3799ce17d6d59df86ed1a5b6, RHOMBUS, NoEscape).A related PowerShell script ‘b.ps1’ (MD5: c1897ea9457343bd8e73f98a1d85a38f) distributes Mallox [ransomware](https://cybersecuritynews.com/ransomware-attack-prevention-checklist/)[,](https://cybersecuritynews.com/ransomware-attack-prevention-checklist/) indicating a multi-platform attack strategy.Besides this, Shodan reveals over 230K internet-connected WebLogic servers with several hundred exposed admin consoles vulnerable to exploitation.**Here below we have presented the MITRE ATT-&CK framework:-** 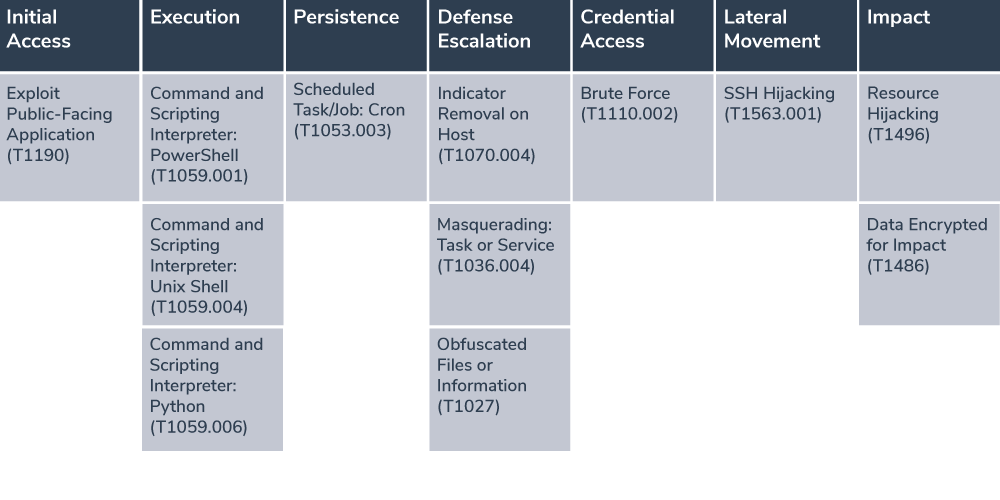 MITRE ATT-&CK framework (Source — Aquasec)**Mitigation**————–**Here below we have mentioned all the mitigations:-*** Always use IaC scanning tools to detect misconfigurations before deployment.* Make sure to use CSPM tools to scan cloud configurations for risks.* Scan [Kubernetes](https://cybersecuritynews.com/new-kubernetes-vulnerability/) clusters for misconfigurations.* Secure container images and[Docker](https://cybersecuritynews.com/hackers-targeting-open-docker-daemon-ports-using-ddos-bot/) files.* Monitor runtime environments.**IOCs**——–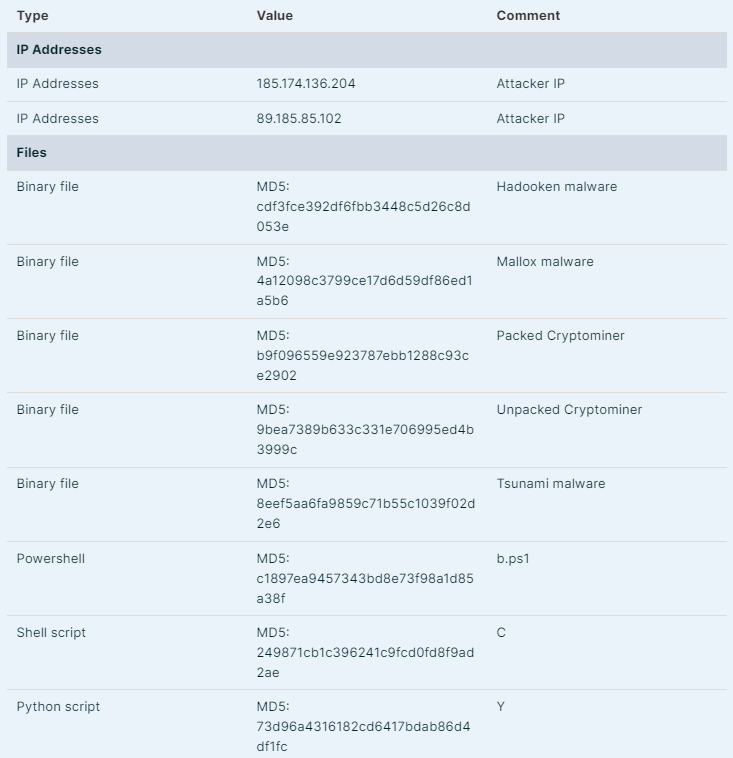 IOCs (Source — Aquasec)**`Simulating Cyberattack Scenarios With All-in-One Cybersecurity Platform — `[Watch Free Webinar](https://go.cynet.com/how-to-achieve-total-protection-webinar?utm_source=cyber_security_news&utm_medium=social&utm_campaign=Q3-sponsored-content&utm_content=all-in-one-demo-on-demand)**The post [New Linux Malware Exploiting Oracle Weblogic Servers](https://cybersecuritynews.com/hadooken-malware-oracle-weblogic/) appeared first on [Cyber Security News](https://cybersecuritynews.com).
Related Tags:
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Blog: Cybersecurity News
TA0001 – Initial Access
TA0008 – Lateral Movement
TA0003 – Persistence
Associated Indicators:
89.185.85.102
4A12098C3799CE17D6D59DF86ED1A5B6
9BEA7389B633C331E706995ED4B3999C
C1897EA9457343BD8E73F98A1D85A38F
8EEF5AA6FA9859C71B55C1039F02D2E6


