OffensiveCon 2024 devised multiple methods to exploit Microsoft Exchange. One method was using the MultiValuedProperty, through which a researcher was able to exploit Exchange PowerShell. Moreover, this exploit bypasses Microsoft’s patch for one of the vulnerabilities.Two vulnerabilities (CVE-2022-41040 and [CVE-2022-41082](https://cybersecuritynews.com/microsoft-security-update-patches-6-actively-exploited-zero-days/)) were previously identified on Exchange, and combining them allowed any authenticated Exchange user to execute remote code.The chaining of the two vulnerabilities was termed ‘ProxyNotShell.’ Further, ProxyNotShell was exploited by hackers in the wild before the patch was released.However, the new bypass includes two RCE vulnerabilities, [CVE-2023-21529](https://cybersecuritynews.com/cyber-security-news-weekly-round-up-3/) and CVE-2024-32031. CVE-2023-21529 was associated with the abuse of the MultiValuedProperty class, and CVE-2023-32031 was related to the bypass for CVE-2023-21529, the abuse of the not blocked Command class.Decoding Compliance: What CISOs Need to Know — **[Join Free Webinar](https://webinars.indusface.com/decoding-compliance-what-cisos-need-to-know/register?utm_source=blog-cta&utm_medium=referral&utm_campaign=2024-september-decoding-compliance-what-cisos-need-to-know)****Exploitation of Exchange PowerShell**—————————————According to the ZDI article, Microsoft introduced Microsoft.Exchange.Diagnostics.UnitySerializationHolderSurrogateSelector to fix the RCE part of the ProxyNotShell chain.This function validates the types retrieved during the deserialization of UnitySerializationHolder using an allow list.A demonstration video was also published, which provides detailed information about the exploitation.**CVE-2023-21529: Allowed MultiValuedProperty Leading to Remote Code Execution**——————————————————————————–The allow list had two main parts: a list of allowed regular types and a list of allowed generic types. Generic types allow the inclusion of arbitrary, internal types that can also be retrieved through a deserialization of *UnitySerializationHolder*.The first part of the generic types list contains custom Exchange types. However, *Microsoft.Exchange.Data.MultiValuedProperty-* or *Microsoft.Exchange.Data.DagNetMultiValuedProperty-* generic classes that use deserialization can be used to execute remote code.This is due to the fact that ‘*PowerShell Remoting deserialization allows one to call a single-argument constructor of any allowed type*’.Further, the *MultiValuedProperty* accepts arguments of type object. Thus, an attacker can provide any allowed PowerShell Remoting Deserializable class to invoke a different constructor that accepts a larger number of arguments.One such example is the *ValueConvertor.TryParseConversion* that calls the *TryConstructorConversion*.The parsing can be supplied with specific arguments such as *originalValue* , *originalType* , *resultType* and *MultiValuedProperty-* type.Here *MultiValuedProperty-* can be abused by providing any XAML deserialization gadget to achieve remote code execution.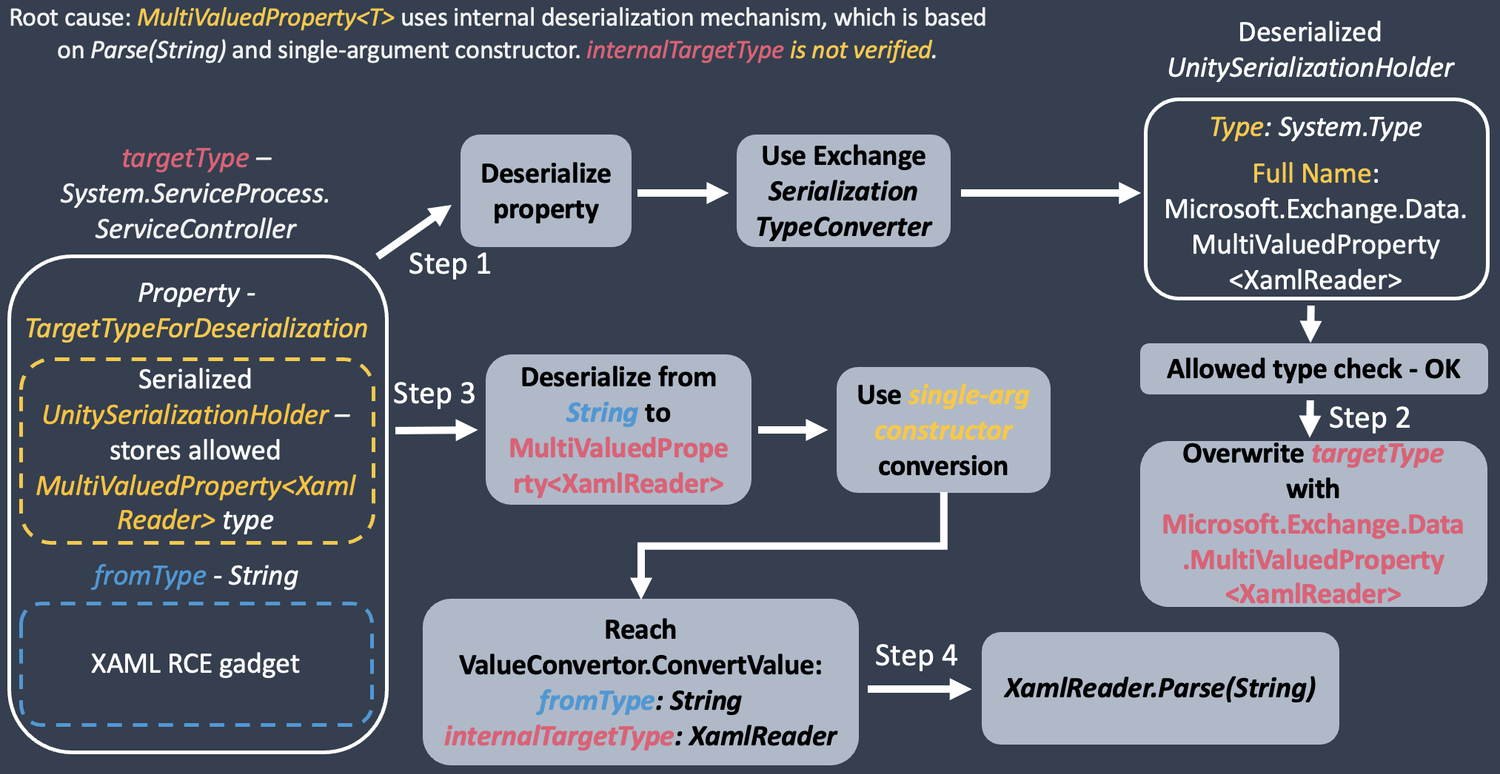 Attack scheme (Source: ZDI)**CVE-2023-32031 — Bypassing the Internal Deny List with the Command Class**—————————————————————————–This is the bypass for the patch provided by Microsoft for CVE-2023-21529. Microsoft removed the *MultiValuedProperty-* from the allow list and implemented additional type control in the internal deserialization mechanism within *MultiValuedProperty* , reads the [report](https://www.zerodayinitiative.com/blog/2024/9/4/exploiting-exchange-powershell-after-proxynotshell-part-1-multivaluedproperty). public static object ConvertValue(object originalValue, Type resultType, IFormatProvider formatProvider) { ChainedSerializationBinder.ValidateResultType(resultType); // [1] if (null == resultType) { throw new ArgumentNullException(‘resultType’); } …However, after analyzing, it was discovered that the *ChainedSerializationBinder.ValidateResultType* method was introduced to limit the types that the attacker can specify.If an attacker can provide the type *MultiValuedProperty-* , an exception is being thrown, because type *XamlReader* fails the new validation.Further, the type validation was based on a deny list which cannot contain any internal Exchange classes. On checking, the *Microsoft.Diagnostics.Runtime.Utilities.Command* class was found that calls the Command(String, CommandOptions) constructor.In addition to this, it also starts a new ProcessStartInfo, which retrieves the process name and arguments from the attacker-controlled input.As this class was not included in the deny list, the researcher used these calls to execute *cmd.exe /c calc.exe* as part of remote code execution.**Download Free Incident Response Plan Template for Your Security Team — [Free Download](https://go.cynet.com/ir-plan-template?utm_source=cyber_security_news&utm_medium=sponsored_article&utm_campaign=Q3-sponsored-content&utm_content=gamechanger)**The post [Researcher Details Exploitation of Exchange PowerShell via MultiValuedProperty](https://cybersecuritynews.com/exploitation-of-exchange-powershell/) appeared first on [Cyber Security News](https://cybersecuritynews.com).
Related Tags:
NAICS: 71 – Arts
Entertainment
Recreation
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 711 – Performing Arts
Spectator Sports
Related Industries
NAICS: 51 – Information
CVE-2022-41040
CVE-2023-21529
CVE-2022-41082
CVE-2023-32031
cmd.exe
Associated Indicators:


