[Encryption -& Key Management](https://www.govinfosecurity.com/encryption-key-management-c-209) , [Security Operations](https://www.govinfosecurity.com/security-operations-c-444)Patched BitLocker Flaw Still Susceptible to Hack================================================Researcher Demonstrates Bitpixie Attack Tactics to Extract Encryption Key [Akshaya Asokan](https://www.govinfosecurity.com/authors/akshaya-asokan-i-2924) ([asokan_akshaya](https://www.twitter.com/asokan_akshaya)) • December 31, 2024 [](https://www.bankinfosecurity.com/patched-bitlocker-flaw-still-susceptible-to-hack-a-27195#disqus_thread) * * * * * [Credit Eligible](/premium/pricing ‘As a BankInfoSecurity.com annual member, this content can be used toward your membership credits and transcript tracking.’)* [](/premium/pricing ‘As a BankInfoSecurity.com annual member, this content can be used toward your membership credits and transcript tracking.’)* Get Permission* 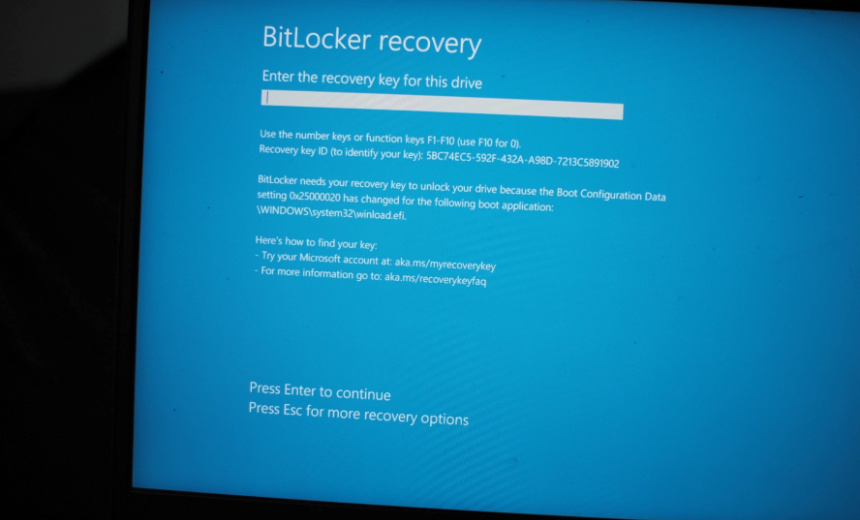 Image: ShutterstockA previously patched flaw in Windows BitLocker disk encryption feature is susceptible to attacks allowing hackers to decrypt information, new research has found.**See Also:** [Cracking the Code: Securing Machine Identities](https://www.govinfosecurity.com/cracking-code-securing-machine-identities-a-27011?rf=RAM_SeeAlso)Speaking at the recently concluded Chaos Communication Congress in Germany, security researcher Thomas Lambertz [said](https://media.ccc.de/v/38c3-windows-bitlocker-screwed-without-a-screwdriver#t=1718) a Microsoft patch for a medium severity flaw tracked as [CVE-2023-21563](https://msrc.microsoft.com/update-guide/vulnerability/CVE-2023-21563) doesn’t fully prevent attacks. Contrary to Microsoft’s analysis, the flaw can be exploited over the network, Lambertz also said.’This is all network only,’ Lambertz said about his exploit tactics. ‘All we had to do was plug a USB device and use [PXE booting]( https://techcommunity.microsoft.com/blog/itopstalkblog/how-does-the-pxe-boot-process-work/888557) to exploit the flaw.’Lambertz demonstrated the attack on a fully updated Windows 11 device using a tactic called ‘bitpixie’ that exploits weaknesses arising from how Windows devices handle memory or encryption during booting and recovery processes.By rebooting the device in recovery mode and running it in a downgraded version using a Windows bootloader, the researcher prompted the device to forget the encryption key.Due to adequate mechanisms in place to revoke certification for older bootloader versions Lambertz said he obtained access to the system memory. He extracted data from the system memory including the master key to decrypt the data.’The only thing that you can do to prevent this attack is to disable the full network stack in the BIOS. This way PXE booting is not possible no matter what you plug in,’ Lambertz said.Lambertz said Microsoft is aware of the issue and is struggling to strike a balance between adequate patching and ensuring security updates do not crash legacy devices.’Microsoft is in this awkward position where every firmware update that they don’t predict correctly could break BitLocker. So they don’t do it,’ Lambertz said.While Microsoft is considering non-renewal of its current boot certification after its expiration in 2026, Lambertz added the proposed move could cause ‘chaos’ as it would mean allowing the use of old, unsecured certificates. Microsoft did not immediately respond to a request for comment.  #### [Akshaya Asokan](https://www.govinfosecurity.com/authors/akshaya-asokan-i-2924)*Senior Correspondent, ISMG* Asokan is a U.K.-based senior correspondent for Information Security Media Group’s global news desk. She previously worked with IDG and other publications, reporting on developments in technology, minority rights and education.[](https://twitter.com/asokan_akshaya) [](mailto:aasokan@ismg.io)  ##### [OnDemand -| Identity Crisis: How to Combat Session Hijacking and Credential Theft with MDR](https://www.govinfosecurity.com/webinars/ondemand-identity-crisis-how-to-combat-session-hijacking-credential-w-5884?rf=RAM_Resources) ##### [OnDemand -| Extended Access Management: Securing Access for All Identities, Devices and Applications](https://www.govinfosecurity.com/webinars/ondemand-extended-access-management-securing-access-for-all-identities-w-5609?rf=RAM_Resources) ##### [OnDemand -| The Evolving Cryptography Cybersecurity Threat in Energy Critical Infrastructure Protection (CIP) Environments](https://www.govinfosecurity.com/webinars/ondemand-evolving-cryptography-cybersecurity-threat-in-energy-critical-w-5359?rf=RAM_Resources) [whitepaper](https://www.govinfosecurity.com/whitepapers/its-time-to-get-serious-about-enterprise-password-management-w-12741?rf=RAM_Resources)##### [It’s Time to Get Serious About Enterprise Password Management](https://www.govinfosecurity.com/whitepapers/its-time-to-get-serious-about-enterprise-password-management-w-12741?rf=RAM_Resources) [whitepaper](https://www.govinfosecurity.com/whitepapers/securing-your-business-begins-password-security-w-12739?rf=RAM_Resources)##### [Securing Your Business Begins with Password Security](https://www.govinfosecurity.com/whitepapers/securing-your-business-begins-password-security-w-12739?rf=RAM_Resources) [Training -& Security Leadership](https://www.govinfosecurity.com/training-security-leadership-c-488)##### [CyberEdBoard Profiles in Leadership: Kevin Li](https://www.govinfosecurity.com/cyberedboard-profiles-in-leadership-kevin-li-a-26936) [Encryption -& Key Management](https://www.govinfosecurity.com/encryption-key-management-c-209)##### [Patched BitLocker Flaw Still Susceptible to Hack](https://www.govinfosecurity.com/patched-bitlocker-flaw-still-susceptible-to-hack-a-27195) [Cloud Security](https://www.govinfosecurity.com/cloud-security-c-445)##### [Arrest of US Army Soldier Tied to AT-&T and Verizon Extortion](https://www.govinfosecurity.com/arrest-us-army-soldier-tied-to-att-verizon-extortion-a-27192) [Artificial Intelligence -& Machine Learning](https://www.govinfosecurity.com/artificial-intelligence-machine-learning-c-469)##### [Safety Concerns, Pushback Against OpenAI’s For-Profit Plan](https://www.govinfosecurity.com/safety-concerns-pushback-against-openais-for-profit-plan-a-27193) [Identity -& Access Management](https://www.govinfosecurity.com/identity-access-management-c-446)##### [The Evolution of Identity Defense: Saviynt’s Vision for 2025](https://www.govinfosecurity.com/evolution-identity-defense-saviynts-vision-for-2025-a-27171)[Overview](https://www.govinfosecurity.com/webinars/risk-management-framework-learn-from-nist-w-255) * Twitter* Facebook* LinkedIn* * * From heightened risks to increased regulations, senior leaders at all levels are pressured to improve their organizations’ risk management capabilities. But no one is showing them how – until now.Learn the fundamentals of developing a risk management program from the man who wrote the book on the topic: Ron Ross, computer scientist for the National Institute of Standards and Technology. In an exclusive presentation, Ross, lead author of NIST Special Publication 800-37 – the bible of risk assessment and management – will share his unique insights on how to:* Understand the current cyber threats to all public and private sector organizations;* Develop a multi-tiered risk management approach built upon governance, processes and information systems;* Implement NIST’s risk management framework, from defining risks to selecting, implementing and monitoring information security controls.Presented By———— [Presented By](/authors/ron-ross-i-558)—————————————#### [Ron Ross](/authors/ron-ross-i-558)*Sr. Computer Scientist -& Information Security Researcher, National Institute of Standards and Technology (NIST)*
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 81 – Other Services (except Public Administration)
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
NAICS: 51 – Information
NAICS: 813 – Religious
Grantmaking
Civic
Professional Services
Similar Services
NAICS: 924 – Administration Of Environmental Quality Programs
Associated Indicators:


