North Korean threat actors are using new malware called OtterCookie in the Contagious Interview campaign that is targeting software developers.Contagious Interview has been active since at least December 2022, according to researchers at cybersecurity company Palo Alto Networks. The campaign targets software developers with fake job offers to deliver malware such as BeaverTail and InvisibleFerret.A report from NTT Security Japan notes that the Contagious Interview operation is now using a new piece of malware called OtterCookie, which was likely introduced in September and with a new variant appearing in the wild in November.OtterCookie attack chain————————Just like in the attacks documented by Palo Alto Networks’ Unit42 researchers, OtterCookie is delivered via a loader that fetches JSON data and executes the ‘cookie’ property as JavaScript code.NTT says that, even though BeaverTail remains the most common payload, OtterCookie has been seen in some cases either deployed alongside BeaverTail or on its own.The loader infects targets through Node.js projects or npm packages downloaded from GitHub or Bitbucket. However, files built as Qt or Electron applications were also used recently. 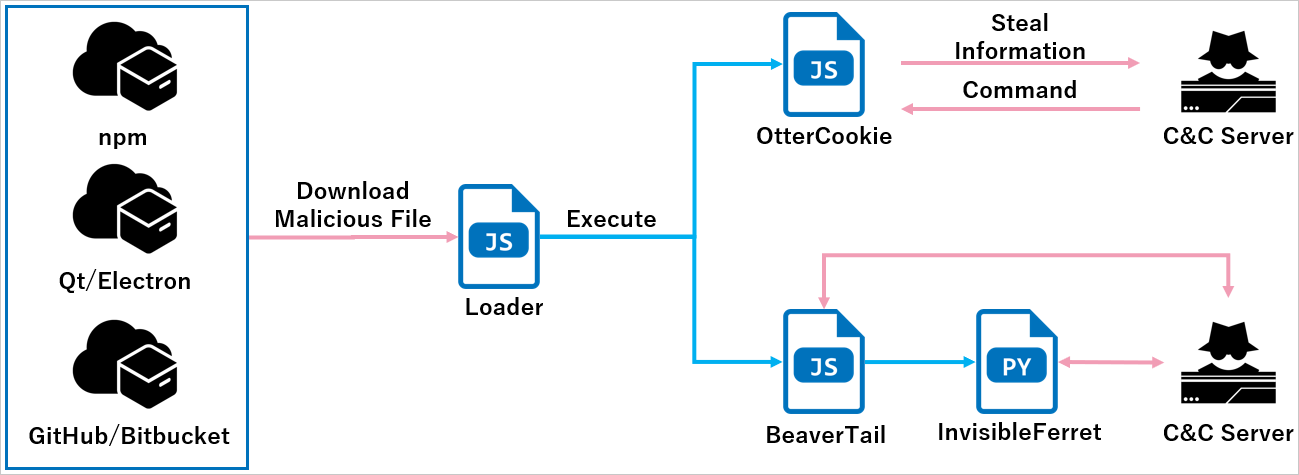 **Overview of the latest Contagious Interview attacks** *Source: NTT Japan*Once active on the target device, OtterCookie establishes secure communications with its command and control (C2) infrastructure using the Socket.IO WebSocket tool, and awaits for commands.The researchers observed shell commands that perform data theft (e.g. collecting cryptocurrency wallet keys, documents, images, and other valuable information).’The September version of OtterCookie already included a built-in functionality to steal keys related to cryptocurrency wallets,’ [NTT explains](https://jp.security.ntt/tech_blog/contagious-interview-ottercookie).’For example, the checkForSensitiveData function used regular expressions to check for Ethereum private keys,’ the researchers note, adding that this was changed with the November variant of the malware where this is achieved through remote shell commands. 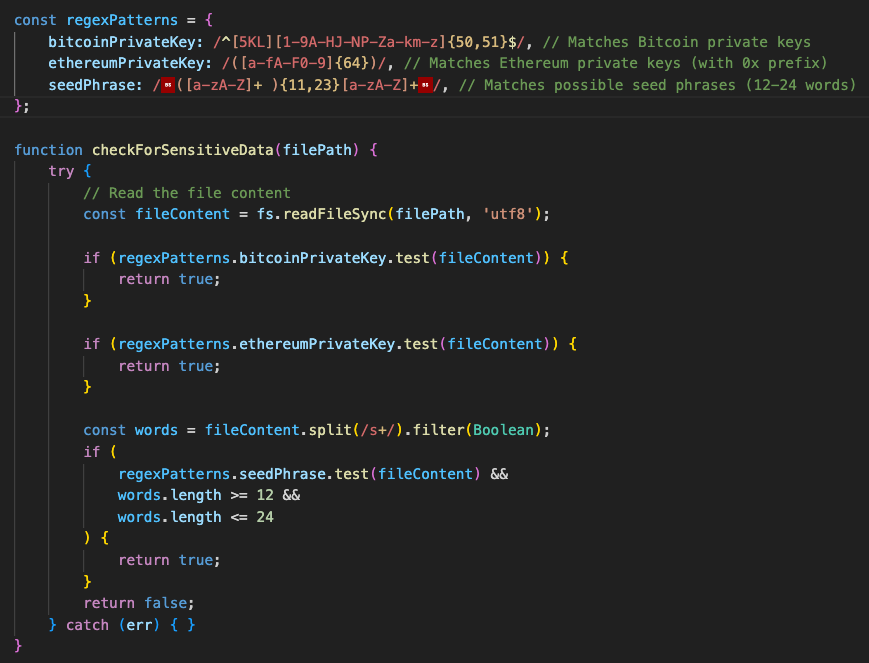 **Targeting cryptocurrency information** *Source: NTT Japan*The latest version of OtterCookie can also exfiltrate clipboard data to the threat actors, which may contain sensitive information.Commands typically used for reconnaissance, like ‘ls’ and ‘cat’, were also detected, indicating the attacker’s intention to explore the environment and stage it for deeper infiltration or lateral movement.The appearance of new malware and the diversification of the infection methods indicate that the threat actors behind the Contagious Interview campaign experiment with new tactics.Software developers should try to verify information about a potential employer and be wary of running code on personal or work computers as part of a job offer that require coding tests. ### Related Articles:[Radiant links $50 million crypto heist to North Korean hackers](https://www.bleepingcomputer.com/news/security/radiant-links-50-million-crypto-heist-to-north-korean-hackers/)[North Korean hackers use new macOS malware against crypto firms](https://www.bleepingcomputer.com/news/security/north-korean-hackers-use-new-macos-malware-against-crypto-firms/)[FBI links North Korean hackers to $308 million crypto heist](https://www.bleepingcomputer.com/news/security/fbi-links-north-korean-hackers-to-308-million-crypto-heist/)[North Korean hackers stole $1.3 billion worth of crypto this year](https://www.bleepingcomputer.com/news/security/north-korean-hackers-stole-13-billion-worth-of-crypto-this-year/)[Crypto-stealing malware posing as a meeting app targets Web3 pros](https://www.bleepingcomputer.com/news/security/crypto-stealing-malware-posing-as-a-meeting-app-targets-web3-pros/)
Related Tags:
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 52 – Finance And Insurance
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
NAICS: 922 – Justice
Public Order
Safety Activities
NAICS: 523 – Securities
Commodity Contracts
Other Financial Investments And Related Activities
NAICS: 51 – Information
TA0043 – Reconnaissance
Blog: BleepingComputer
Associated Indicators:


