  Menu* [Tools](https://unit42.paloaltonetworks.com/tools/)* [ATOMs](https://unit42.paloaltonetworks.com/atoms/)* [Security Consulting](https://www.paloaltonetworks.com/unit42)* [About Us](https://unit42.paloaltonetworks.com/about-unit-42/)* [**Under Attack?**](https://start.paloaltonetworks.com/contact-unit42.html) * [Threat Research Center](https://unit42.paloaltonetworks.com ‘Threat Research’)* [Threat Research](https://unit42.paloaltonetworks.com/category/threat-research/ ‘Threat Research’)* [Malware](https://unit42.paloaltonetworks.com/category/malware/ ‘Malware’) [Malware](https://unit42.paloaltonetworks.com/category/malware/)TA Phone Home: EDR Evasion Testing Reveals Extortion Actor’s Toolkit==================================================================== 14 min read Related Products Advanced DNS SecurityAdvanced URL FilteringAdvanced WildFireCloud-Delivered Security ServicesCortexCortex XDRCortex XSIAMUnit 42 Incident Response *  By: * [Navin Thomas](https://unit42.paloaltonetworks.com/author/navin-thomas/) * [Renzon Cruz](https://unit42.paloaltonetworks.com/author/renzon-cruz/) * [Cuong Dinh](https://unit42.paloaltonetworks.com/author/cuong-dinh/)*  Published:November 1, 2024*  Categories: * [Malware](https://unit42.paloaltonetworks.com/category/malware/) * [Threat Research](https://unit42.paloaltonetworks.com/category/threat-research/)*  Tags: * [BYOVD](https://unit42.paloaltonetworks.com/tag/byovd/) * [Cobalt Strike](https://unit42.paloaltonetworks.com/tag/cobalt-strike/) * [Conti ransomware](https://unit42.paloaltonetworks.com/tag/conti-ransomware/) * [Data exfiltration](https://unit42.paloaltonetworks.com/tag/data-exfiltration/) * [Extortion](https://unit42.paloaltonetworks.com/tag/extortion/) * [Mimikatz](https://unit42.paloaltonetworks.com/tag/mimikatz/) * [Security feature bypass](https://unit42.paloaltonetworks.com/tag/security-feature-bypass/)* * Share* * * * * * * Executive Summary—————–This article reviews an incident where a threat actor unsuccessfully tried bypassing Cortex XDR. By digging further into the incident, the process instead provided us with insight into the threat actor’s operations.In a recent investigation involving an extortion attempt, we discovered a threat actor had purchased access to the client network via Atera RMM from an initial access broker. We discovered the threat actor used rogue systems to install the Cortex XDR agent onto a virtual system. They did this to test a new antivirus/endpoint detection and response (AV/EDR) bypass tool leveraging the [bring your own vulnerable driver (BYOVD) technique](https://blogs.vmware.com/security/2023/04/bring-your-own-backdoor-how-vulnerable-drivers-let-hackers-in.html).Connectivity between this virtual system and the client’s network inadvertently gave Unit 42 investigators a certain level of access to the rogue systems. This provided visibility into various tools and files held by the threat actor. While the threat actor intended to find a way to bypass Cortex, in actuality this activity helped Unit 42 protect other organizations by providing unique visibility into the threat actor’s tooling, targeting and persona.In this report, we provide an overview of the attack that occurred, details about the AV/EDR bypass tool, and its sale on cybercrime forums. Most importantly, we offer a walkthrough for how Unit 42 researchers managed to unmask one of the threat actors involved. We’ll give a peek into all the discoveries related to the identification of the threat actor.Palo Alto Networks customers are better protected from the threats discussed above through the following products:* [Cortex XDR](https://docs-cortex.paloaltonetworks.com/p/XDR) and [XSIAM](https://www.paloaltonetworks.com/cortex/cortex-xsiam)* [Advanced WildFire](https://docs.paloaltonetworks.com/advanced-wildfire)* [Advanced URL Filtering](https://docs.paloaltonetworks.com/advanced-url-filtering/administration/url-filtering-basics/how-url-filtering-works) and [Advanced DNS Security](https://docs.paloaltonetworks.com/dns-security/administration/about-dns-security)If you think you might have been compromised or have an urgent matter, contact the [Unit 42 Incident Response team](https://start.paloaltonetworks.com/contact-unit42.html).**Related Unit 42 Topics** [**Extortion**](https://unit42.paloaltonetworks.com/tag/extortion/), **[Data Exfiltration](https://unit42.paloaltonetworks.com/tag/data-exfiltration)**Overview——–Unit 42 was called to assist with an extortion incident. Through the investigation process, we encountered two endpoints involved in the attack that were unknown to the client environment.As a means to test an AV/EDR bypass tool, these endpoints had older versions of Cortex XDR agents installed. Unbeknownst to the threat actor, we were able to access these rogue endpoints.We also discovered a series of toolkits and other files belonging to the threat actor on the system, which included the bypass tool. We successfully traced and identified posts related to the sale of this specific tool on cybercrime forums like XSS and Exploit.Using files obtained from the rogue endpoints and subsequent investigation, we discovered the true identity of one of the threat actors involved in the incident. We also found additional information about the individual’s personal and professional background.Figure 1 presents a high-level chain of events in the attack investigated by Unit 42.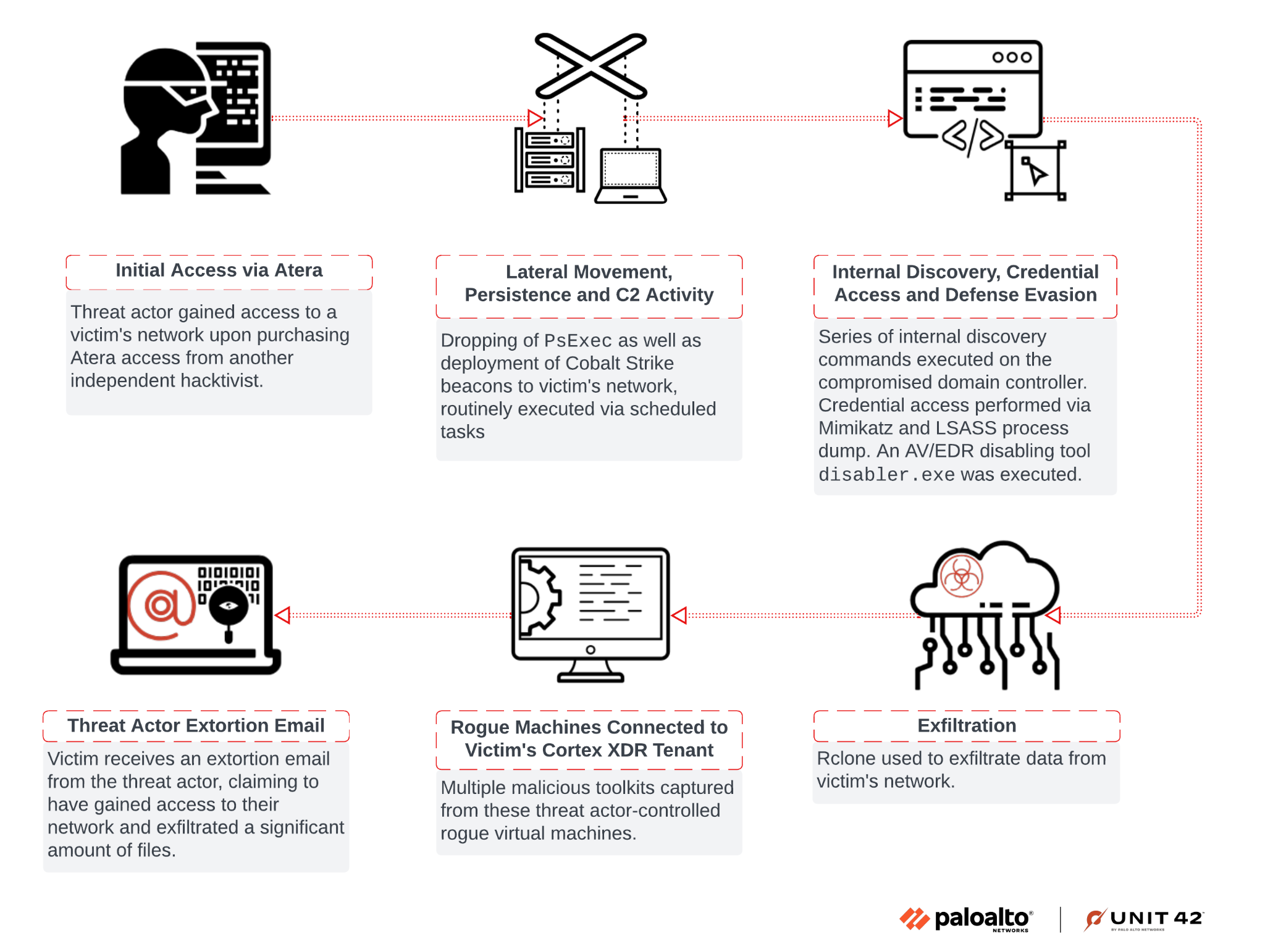 Figure 1. High-level chain of events for this attack.AV/EDR Bypass Tool——————The particular tool, named disabler.exe, appears to use the publicly available source code from [EDRSandBlast](https://github.com/wavestone-cdt/EDRSandblast) with small modifications and removal of the CLI features. This is evidenced by similarity in content in EDRSandBlast source code files shown in Figure 2 and referenced in the binary as shown in Figure 3. We have noted some of the similarities in red in both figures.The tool’s primary function is to target and remove EDR hooks in user-mode libraries and kernel-mode callbacks. It includes a companion file, wnbios.sys or WN_64.sys, which is a vulnerable driver that the tool attempts to load and gain access to.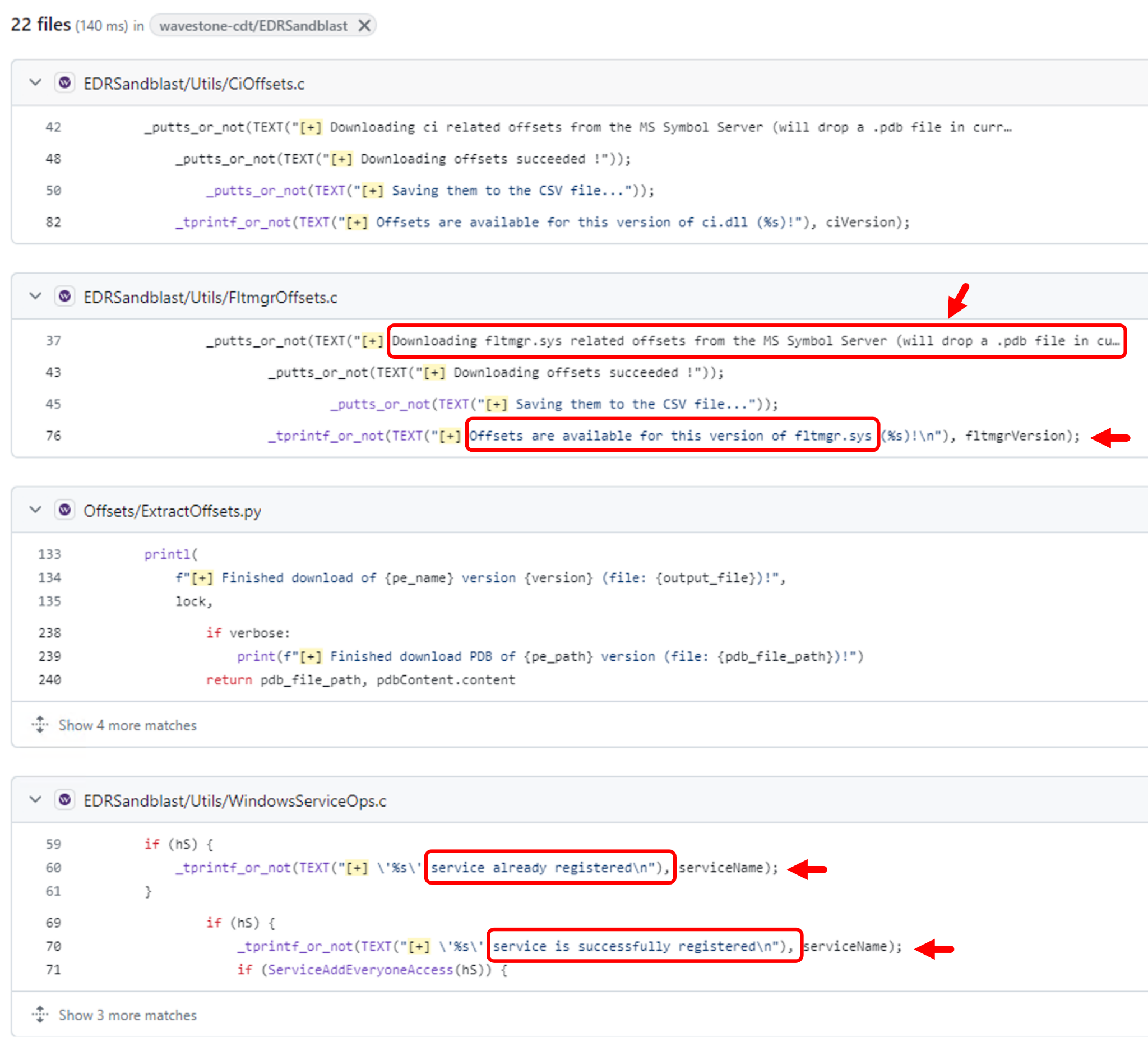 Figure 2. Snippet of some of the strings printed by EDRSandBlast.  Figure 3. Same strings seen in disabler.exe static library.Based on certain files and folders in one of the rogue endpoints, we searched cybercrime forums such as XSS and Exploit to identify the likely seller of this bypass tool.### Identifying the Seller of the Bypass ToolThe rogue system had a hostname of DESKTOP-J8AOTJS and contained several directories with interesting names under the file path Z:–freelance. This led us to the hypothesis that these were names or monikers of various other affiliates as shown below in Figure 4. Figure 4. List of folders in Z:–freelance on the rogue system.With that in mind, we searched cybercrime forums for usernames matching any of the directory names under Z:–freelance. While some of them were either too noisy or didn’t return any result at all, the rest did return some interesting hits. The matching names consistently posted either in the Russian language, or they posted in Russian-based cybercrime forums, the most common being XSS and Exploit.The username that piqued our interest the most was *Marti71*. This username posted in multiple places looking for tools to bypass AV/EDR. Figure 5 shows one such example, with the post translated to English as follows:Greetings, everyone!Does anyone have an out-of-the-box solution to kill antivirus software? I’m ready to purchase several solutions with regular support/subscription. Figure 5. Marti71 inquiring about antivirus killing software.The final post on this thread was from a user account named *KernelMode,*suggesting an AV/EDR bypass tool. Figure 6. User KernelMode suggesting an AV/EDR bypass tool.Pivoting to the link in *KernelMode* ‘s post in Figure 6, we found a thread that *KernelMode* initiated to sell subscriptions to an AV/EDR bypass tool as Figure 7 shows. However, the post contains nothing that would confirm that the person or people behind *KernelMode* are the developers of this bypass tool.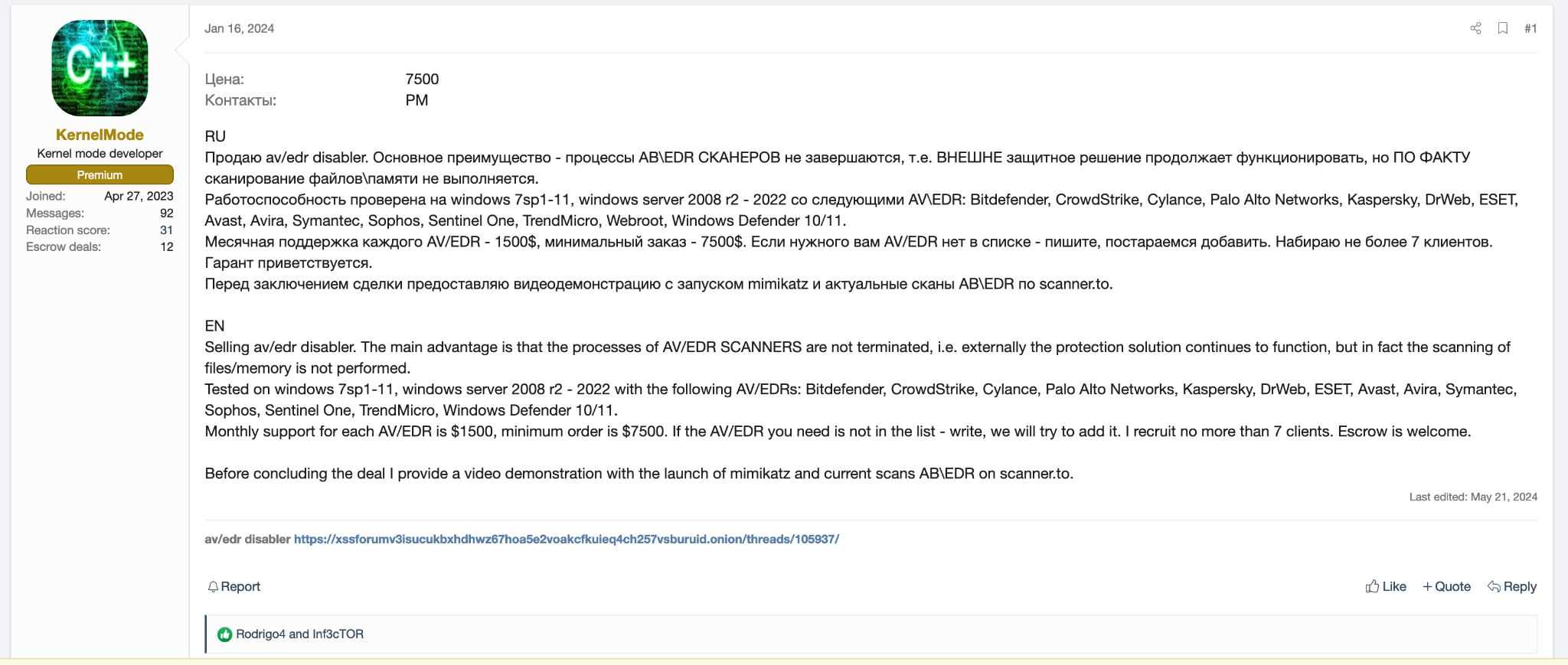 Figure 7. KernelMode posting about the sale of an AV/EDR bypass tool.*Marti71*also posted on this thread as shown in Figure 8, which seems to indicate a positive experience with the tool.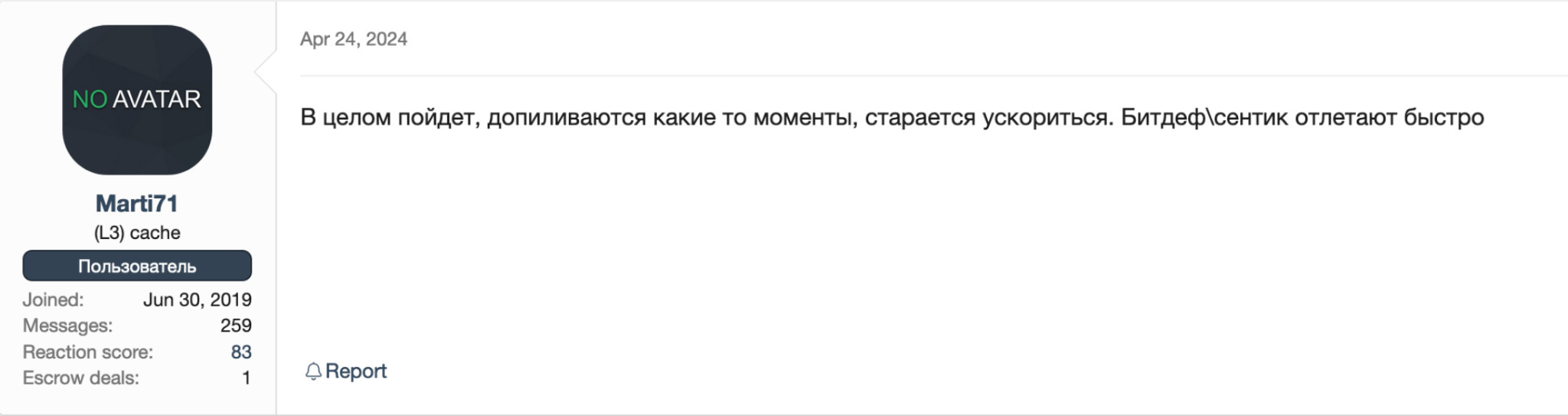
Related Tags:
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 51 – Information
TA0010 – Exfiltration
Mimikatz
Conti
Blog: Unit42
Cobalt Strike
Associated Indicators:


