### **Explanation of the Current Alert Level of GUARDED****The alert level is the overall current threat level.**-On October 17, the Cyber Threat Alert Level was evaluated and is remaining at Blue (Guarded) due to vulnerabilities in Mozilla, Palo Alto, Oracle, and Google products. On October 10, the MS-ISAC released an advisory for a vulnerability in Mozilla Firefox that could allow for remote code execution. On October 14, the MS-ISAC released an advisory for multiple vulnerabilities in Palo Alto Network’s Expedition, the most severe of which could allow for arbitrary code execution. On October 15 the MS-ISAC released two advisories. The first advisory was for multiple vulnerabilities in Oracle products, the most severe of which could allow for remote code execution. The second advisory was for multiple vulnerabilities in Google products, the most severe of which could allow for arbitrary code execution. Organizations and users are advised to update and apply all appropriate vendor security patches to vulnerable systems and to continue to update their antivirus signatures daily. Another line of defense includes user awareness training regarding the threats posed by attachments and hypertext links contained in emails especially from un-trusted sources.- -[Read more about our approach](/cybersecurity-threats/alert-level) ### Latest AdvisoryMultiple Vulnerabilities in Microsoft Edge (Chromium-based) Could Allow for Arbitrary Code Execution 18 Oct 2024 Multiple vulnerabilities have been discovered in Microsoft Edge (Chromium-based), the most severe of which could allow for arbitrary code executi…[Read the details](/advisory/multiple-vulnerabilities-in-microsoft-edge-chromium-based-could-allow-for-arbitrary-code-execution_2024-119 ”) ##### Our MS-ISAC AdvisoriesAdvisories Released (Last 12 Months)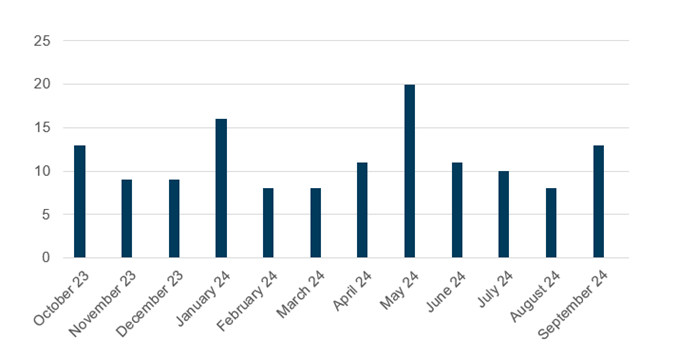  In Q1 2024, the Top 10 Malware observed at the Multi-State Information Sharing and Analysis Center® (MS-ISAC®) changed slightly from the previous quarter. The downloader SocGholish continues to lead as the Top Malware, making up 60% of the Top 10 Malware. ArechClient2, a .Net-based Remote Access Trojan (RAT), came in second, while CoinMiner, a malicious cryptocurreny miner, was the third most-prevalent malware in Q1 2024. Lumma Stealer, Jupyter, and Ratenjay all returned to the list in Q1. Please see below for more detailed malware descriptions and associated indicators of compromise. Windows operating systems.##### Top Malware Q2 20241. SocGholish2. Agent Tesla3. CoinMiner4. NanoCore5. ZPHP6. Mirai7. Magecart8. Arechclient29. DarkGate10. Lumma Stealer##### Take Control of Your Organization’s SecurityThe information on this page is maintained by our Security Operations Center, which is part of MS-ISAC and EI-ISAC.
Related Tags:
DarkGate
FakeUpdates
Blog: CIS – Center for Internet Security (Alerts)
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NanoCore
Agent Tesla
Software Discovery: Security Software Discovery
Software Discovery
Associated Indicators:


