* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)Japanese Spam on a Cleaned WordPress Site: The Hidden Sitemap Problem===================================================================== [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)* January 15, 2025  While investigating a compromised WordPress site, we discovered a malware infection causing Japanese spam links to appear in Google search results. Although the site had been cleaned, Google was still crawling and indexing spammy URLs, which impacted the site’s SEO and credibility.### Japanese SEO Spam: A Common ThreatJapanese SEO spam is a recurring issue that compromises websites to display spammy content in search engine results. Attackers often inject malicious URLs or sitemaps into a site’s infrastructure to manipulate its search rankings. We’ve covered similar cases in the past, including [How to Find and Fix Japanese SEO Spam](https://blog.sucuri.net/2023/09/how-to-find-fix-japanese-seo-spam.html), which outlines the broader impact of such attacks.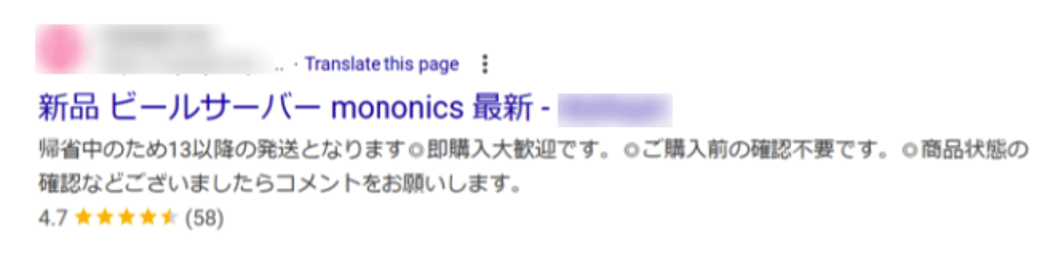### The Problem: Japanese Spam URLs PersistingThe site owner initially reported an influx of spam links showing in Google search results, even though the site displayed no visible spam content. The Google Search Console (GSC) was reporting an increasing number of spam URLs in the format:“`domainname/?m=XXXXXXXXX“`These URLs were indexed as Japanese spam results, misleading users and harming the site’s reputation. Here, **XXXXXXXXX** is a random string of numbers used to generate unique spam URLs. Attempts to access these spam URLs returned 404 errors, they were still being crawled and indexed by Google, creating an SEO issue for the site owner.### Discovery and InvestigationSince the site continued indexing spam URLs, even after cleaning Google Search Console, this indicated that either there is something cached or the malicious URLs still exist somewhere. During our investigation, we discovered a file named **spamurl.txt** in the root directory. This file was configured as a sitemap in GSC, prompting Google to crawl over 3,000 spam URLs. The number of indexed spam URLs continued to rise in GSC, signaling that the sitemap was actively enabling the spam campaign.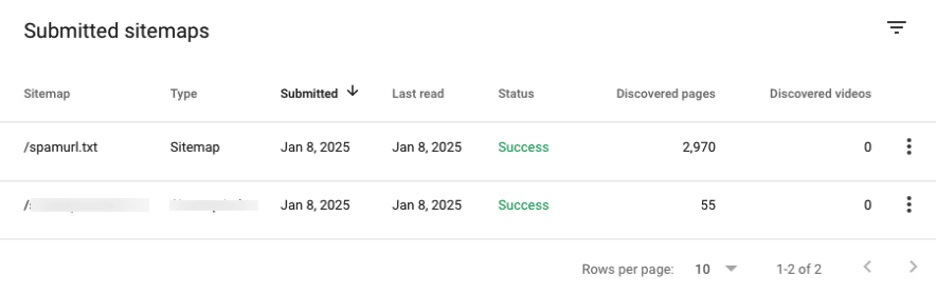The content in the **spamurl.txt** file looked like this: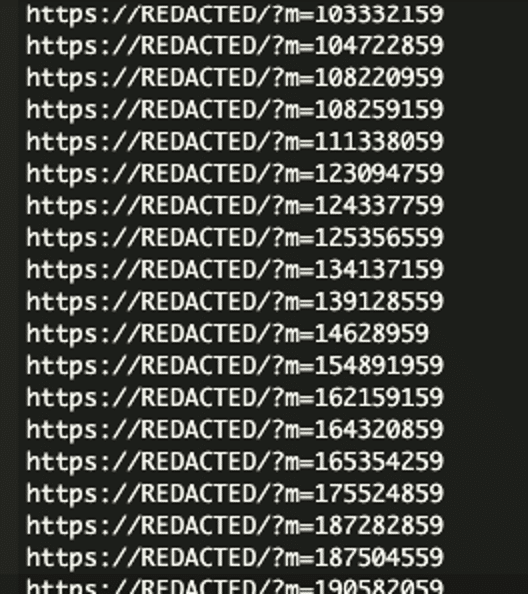### Mitigating the Spam**Removing the Spam File:** We identified and deleted the spamurl.txt file from the site’s root directory. This immediately stopped Google from crawling the malicious URLs listed in the file.**Updating Sitemap Settings:** The file was also [removed from the GSC sitemap configuration](https://support.google.com/webmasters/thread/14726089/how-to-delete-xml-sitemap-from-google-search-console?hl=en) to ensure it no longer influenced Google’s crawling behavior.**Reindexing the Site:** Using the URL Inspection Tool in GSC, we submitted the site for reindexing. This helped clear the spam URLs from Google’s search index and restored the site’s SEO standing.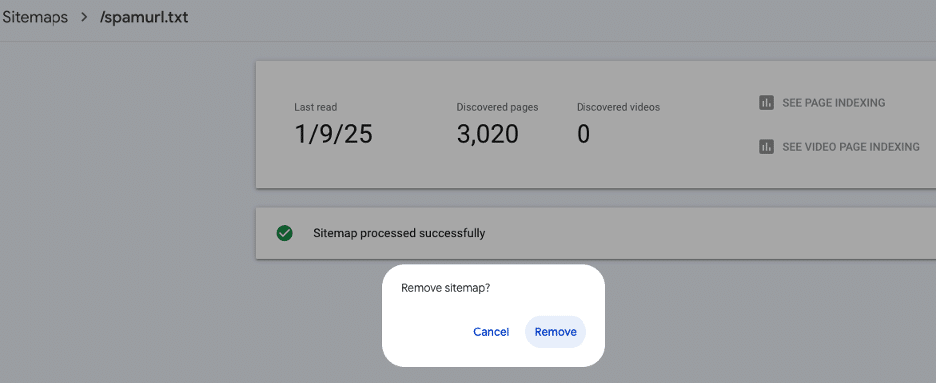### Why Did This Happen? And Key Takeaways* Compromised Sitemap Management: Attackers leveraged the sitemap submission settings in GSC to inject the malicious spamurl.txt file and have Google crawl spam URLs.* Persistent Spam URLs: Even after the visible spam was removed, the sitemap ensured spam links remained indexed.* Regularly audit your sitemap files and GSC settings to identify any unauthorized additions.* Removing malicious files is not enough; you must update GSC settings and request reindexing to clear indexed spam results.Even after cleaning a site, Japanese spam can persist if malicious artifacts like unauthorized sitemaps are overlooked. This case highlights how attackers can persistently affect a site’s SEO and reputation even after visible spam is removed.By exploiting sitemaps and the Google Search Console, they manipulated the site’s indexed content, causing long-term damage.If you suspect similar activity on your site, Sucuri’s security experts are here to help with malware removal and ongoing protection.### Prevention Tips* **Monitor Sitemaps Regularly:** Frequently review your sitemap settings in GSC to detect any unauthorized additions.* **Secure File Permissions:** Restrict write access to critical directories to prevent unauthorized files from being uploaded.* **Use a Web Application Firewall (WAF):** Deploying a WAF can block malicious traffic and prevent attackers from exploiting vulnerabilities in your site.* **Perform Routine Security Scans:** Regular scans can help identify malware and suspicious files before they cause significant harm.* **Keep Software Updated:** Ensure your WordPress core, plugins, and themes are up-to-date to reduce vulnerabilities.Additionally, ensuring Google receives 404 responses for spam URLs is critical for de-listing them, and any conflicting signals—such as a sitemap referencing these URLs—can prolong the problem.  ##### [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)Puja Srivastava is a Security Analyst with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training, cross-training and mentoring new recruits and analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.##### Related Tags* [SEO Spam](https://blog.sucuri.net/tag/seo-spam),* [WordPress Security](https://blog.sucuri.net/tag/wordpress-security)##### Related Categories* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security) * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Security Education](https://blog.sucuri.net/category/security-education)* [Web Pros](https://blog.sucuri.net/category/web-pros)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2016/06/growing-ddos-threat-website-owners.html) [The Growing DDoS Threat to Website Owners](https://blog.sucuri.net/2016/06/growing-ddos-threat-website-owners.html)——————————————————————————————————————–* Tony Perez* June 14, 2016 As website attacks continue to evolve, we see growing levels of sophistication in the way attackers are expanding the economics of their industry. The monetization… [Read the Post](https://blog.sucuri.net/2016/06/growing-ddos-threat-website-owners.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2020/01/what-is-cross-site-contamination.html) [What is Cross-Site Contamination?](https://blog.sucuri.net/2020/01/what-is-cross-site-contamination.html)———————————————————————————————————-* Juliana Lewis* January 9, 2020 How many websites do you currently have on your server? If the answer is something along the lines of, ‘One that I really care about,… [Read the Post](https://blog.sucuri.net/2020/01/what-is-cross-site-contamination.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2017/09/old-themes-abandoned-scripts-pitfalls-cleaning-serialized-data.html) [Old Themes, Abandoned Scripts and Pitfalls of Cleaning Serialized Data](https://blog.sucuri.net/2017/09/old-themes-abandoned-scripts-pitfalls-cleaning-serialized-data.html)—————————————————————————————————————————————————————————–* Denis Sinegubko* September 13, 2017 Over the summer, we’ve seen waves of WordPress database infections that use vulnerabilities in tagDiv’s Newspaper/Newsmag themes or InterconnectIT Search and Replace scripts (searchreplacedb2.php). The… [Read the Post](https://blog.sucuri.net/2017/09/old-themes-abandoned-scripts-pitfalls-cleaning-serialized-data.html)  * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/12/5-year-anniversary-of-the-soaksoak-malware-tsunami.html) [5 Year Anniversary of the SoakSoak Malware Tsunami](https://blog.sucuri.net/2019/12/5-year-anniversary-of-the-soaksoak-malware-tsunami.html)———————————————————————————————————————————————* Denis Sinegubko* December 19, 2019 This is a story about the SoakSoak malware campaign that proved that you can’t underestimate impact of security issues in popular premium software. These days,… [Read the Post](https://blog.sucuri.net/2019/12/5-year-anniversary-of-the-soaksoak-malware-tsunami.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2024/07/how-to-set-cache-control-headers.html) [How to Set Cache Control Headers](https://blog.sucuri.net/2024/07/how-to-set-cache-control-headers.html)———————————————————————————————————* Rianna MacLeod* July 11, 2024 When it comes to your website performance, every millisecond counts. Whether you’re managing a personal blog or a large-scale e-commerce site, the speed at which… [Read the Post](https://blog.sucuri.net/2024/07/how-to-set-cache-control-headers.html)  * [Security Education](https://blog.sucuri.net/category/security-education)[](https://blog.sucuri.net/2017/05/personal-security-guide-online-accounts.html) [Personal Security Guide — Online Accounts](https://blog.sucuri.net/2017/05/personal-security-guide-online-accounts.html)————————————————————————————————————————–* Caleb Lane* May 23, 2017 In our last post on browser security, we talked about how developing a broader security mindset can help keep your website safe. By taking steps… [Read the Post](https://blog.sucuri.net/2017/05/personal-security-guide-online-accounts.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2020/03/pci-compliance-penetration-testing-and-the-sucuri-waf.html) [PCI Compliance, Penetration Testing, and the Sucuri WAF](https://blog.sucuri.net/2020/03/pci-compliance-penetration-testing-and-the-sucuri-waf.html)—————————————————————————————————————————————————–* Marc Kranat* March 6, 2020 Our support team is often asked, ‘Can we test our site through the Sucuri Web Application Firewall?’ The answer is always yes, with a caveat…. [Read the Post](https://blog.sucuri.net/2020/03/pci-compliance-penetration-testing-and-the-sucuri-waf.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2019/08/largest-ddos-attack.html) [The Largest DDoS Attacks -& What You Can Learn From Them](https://blog.sucuri.net/2019/08/largest-ddos-attack.html)——————————————————————————————————————–* Pilar Garcia* August 21, 2019 A DDoS (Distributed Denial of Service) is an attack that focuses on making the website unavailable to its legitimate users. DDoS attacks can produce service interruptions,… [Read the Post](https://blog.sucuri.net/2019/08/largest-ddos-attack.html)[Backdoors: The Hidden Threat Lurking in Your Website](https://blog.sucuri.net/2025/01/backdoors-the-hidden-threat-lurking-in-your-website.html)————————————————————————————————————————————————* Kyle Knight* January 17, 2025 Website backdoors are a silent yet deadly threat to website security. These stealthy mechanisms bypass standard authentication, providing attackers with persistent, unauthorized access to a… [Read the Post](https://blog.sucuri.net/2025/01/backdoors-the-hidden-threat-lurking-in-your-website.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2020/05/unauthenticated-stored-cross-site-scripting-in-wp-product-review.html) [Unauthenticated Stored Cross Site Scripting in WP Product Review](https://blog.sucuri.net/2020/05/unauthenticated-stored-cross-site-scripting-in-wp-product-review.html)————————————————————————————————————————————————————————-* John Castro* May 14, 2020 During a routine research audit for our Sucuri Firewall, we discovered an Unauthenticated Persistent Cross-Site Scripting (XSS) affecting 40,000+ users of the WP Product Review… [Read the Post](https://blog.sucuri.net/2020/05/unauthenticated-stored-cross-site-scripting-in-wp-product-review.html)
Related Tags:
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 52 – Finance And Insurance
NAICS: 522 – Credit Intermediation And Related Activities
Denis
Blog: Sucuri
Phishing: Spearphishing Link
Phishing
Software Discovery: Security Software Discovery
Software Discovery
Associated Indicators:


