* [Cyber Risk](/cyber-risk)* [Cyberattacks -& Data Breaches](/cyberattacks-data-breaches)[
Cybersecurity In-Depth: Digging into data about the latest attacks, threats, and trends using charts and tables.](/program/the-edge) SEC Disclosures Up, But Not Enough Details Provided SEC Disclosures Up, But Not Enough Details Provided=======================================================================================================While companies have responded to the new SEC rules by disclosing incidents promptly, many of the reports don’t meet the SEC’s ‘material’ standard.  [Fahmida Y. Rashid](/author/fahmida-y-rashid), Managing Editor, FeaturesDecember 26, 2024 3 Min Read 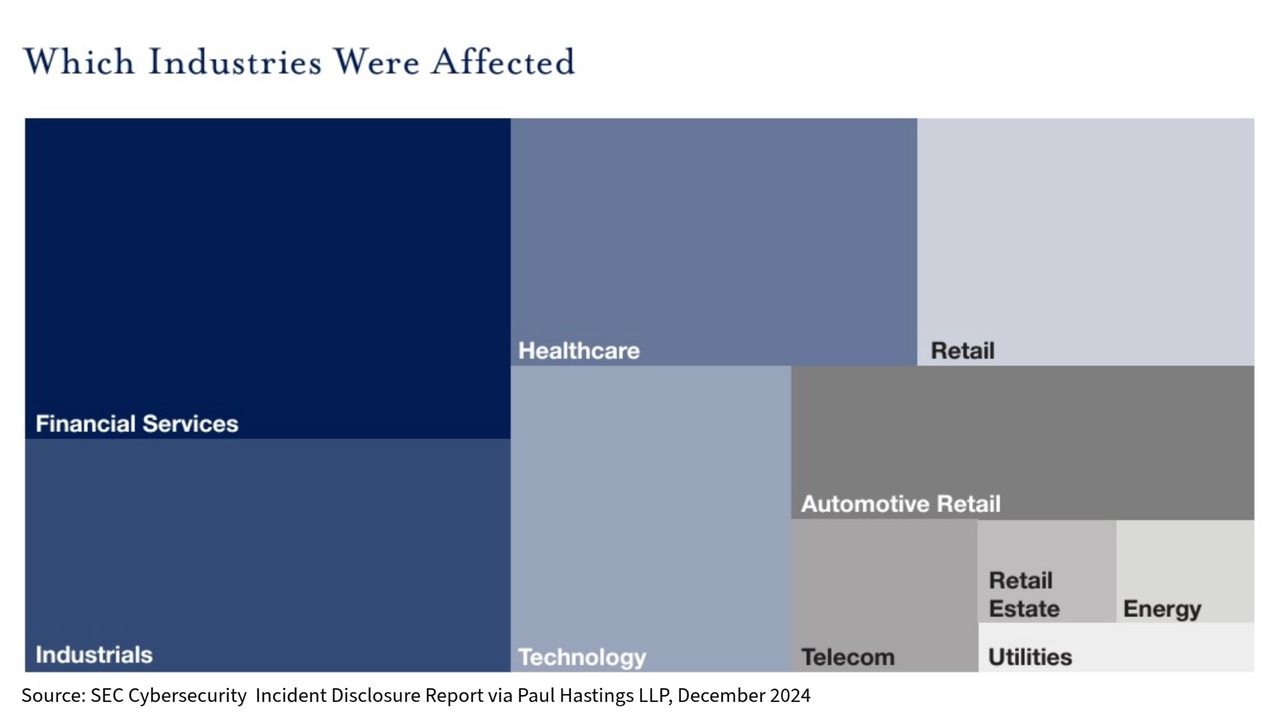 Source: Paul Hastings, LLP [](https://www.linkedin.com/sharing/share-offsite/?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](http://www.facebook.com/sharer/sharer.php?u=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](http://www.twitter.com/intent/tweet?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](https://www.reddit.com/submit?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details&title=SEC%20Disclosures%20Up%2C%20But%20Not%20Enough%20Details%20Provided)[](/cdn-cgi/l/email-protection#84bbf7f1e6eee1e7f0b9d7c1c7a4c0edf7e7e8ebf7f1f6e1f7a4d1f4a8a4c6f1f0a4caebf0a4c1eaebf1e3eca4c0e1f0e5ede8f7a4d4f6ebf2ede0e1e0a2e5e9f4bfe6ebe0fdb9cda1b6b4f0ecebf1e3ecf0a1b6b4f0ece1a1b6b4e2ebe8e8ebf3edeae3a1b6b4e2f6ebe9a1b6b4c0e5f6efa1b6b4d6e1e5e0edeae3a1b6b4e9ede3ecf0a1b6b4edeaf0e1f6e1f7f0a1b6b4fdebf1aaa1b4c0a1b4c5a1b4c0a1b4c5a1b6b4d7c1c7a1b6b4c0edf7e7e8ebf7f1f6e1f7a1b6b4d1f4a1b6c7a1b6b4c6f1f0a1b6b4caebf0a1b6b4c1eaebf1e3eca1b6b4c0e1f0e5ede8f7a1b6b4d4f6ebf2ede0e1e0a1b4c0a1b4c5ecf0f0f4f7a1b7c5a1b6c2a1b6c2f3f3f3aae0e5f6eff6e1e5e0edeae3aae7ebe9a1b6c2e7fde6e1f6a9f6edf7efa1b6c2f7e1e7a9e0edf7e7e8ebf7f1f6e1f7a9f1f4a9e6f1f0a9eaebf0a9e1eaebf1e3eca9e0e1f0e5ede8f7) The new cybersecurity disclosure rules introduced by the US Securities and Exchange Commission (SEC) last year have resulted in a significant increase of incident reports from public companies, but most of the reports do not include the material impact of those incidents, according to a law firm specializing in finance and M-&A activity.[Analysis by Paul Hastings LLP](https://www.paulhastings.com/insights/ph-privacy/sec-cybersecurity-incident-disclosure-report) found cybersecurity incident reports have increased by 60% since the disclosure rule went into effect in 2023. The SEC regulation requires public companies to disclose material cybersecurity incidents within four business days of determining materiality. Material, in this instance, means that the incident can impact someone’s decision on whether to invest in the company. Determining materiality involves considering the immediate fallout and any longer-term effects on a company’s operations, customer relationships, financial impact, reputational or brand perception, and the potential for litigation or regulatory action.As the chart above shows, the impact of the regulation spans numerous industries. While the financial services sector accounted for the largest number of disclosure reports, industrials and healthcare were also heavily impacted. Automotive retail and retail entities were also hit by cyberattacks and had to report those incidents.Less than 10% of the disclosures detailed the material impacts of the incidents, suggesting that companies are having difficulty balancing detailed reporting with protecting the details of internal operations. The report included examples of what was considered material, such as Basset Furniture Industries noting that business operations are materially impacted until recovery efforts are completed, or First American Financial disclosing adjusted earning per share for the fourth quarter financial results and quantifying the losses in the company’s SEC filings.Some companies (13%) opted to provide a press release or a reference to a blog post to provide more details about the incident.Third-Party Breach Impact————————-One in four incidents in the report were third-party breaches. Companies are struggling to figure out whether to disclose third-party breaches, especially if other victims have disclosed the incidents. The automotive retail sector was affected primarily by the ransomware attack on [automotive software provider CDK Global](https://www.darkreading.com/application-security/thousands-of-car-dealerships-stalled-out-after-software-provider-cyber-incident) in June. The company paid a $25 million ransom. CDK’s parent company, Brookfield Business Partners, said in its July disclosure that the company did not ‘expect this incident to have a material impact.’ Many of the smaller automotive companies claimed material impact as a result of CDK’s incident.The SEC recently announced enforcement settlements with four SolarWinds customers for allegedly making misleading disclosures related to how they were impacted by the cyberattack. Two of the four publicly disclosed the incidents but did not disclose all material facts known at the time, such as the name of the threat actor, nature of information stolen, and number of accounts accessed. The other two did not disclose the incidents, and the SEC said they should have disclosed the impact.Speed or More Details?———————-More than three-quarters (78%) of disclosures were made within eight days of discovery of the incident. The SEC specified that the deadline to disclose is not four business days after discovering the incident but rather when materiality has been determined, but most companies opted to act quickly. A third (32%) filed within four days of discovery. This suggests that companies are reporting quickly to avoid being fined by the SEC for delayed disclosure but too quickly because they have not yet determined the full implications of the incident. This may be why 42% of the companies wound up filing multiple reports for the same incident, each time providing more details, such as quantifiable loss, impact to customer personal data, and notification to individuals and regulators.’Companies should continue to evaluate disclosure controls and engage in tabletop exercises to practice the decision-making required to makes such materiality decisions in the event of a cyber incident,’ the report’s authors said. [](https://www.linkedin.com/sharing/share-offsite/?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](http://www.facebook.com/sharer/sharer.php?u=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](http://www.twitter.com/intent/tweet?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details)[](https://www.reddit.com/submit?url=https://www.darkreading.com/cyber-risk/sec-disclosures-up-but-not-enough-details&title=SEC%20Disclosures%20Up%2C%20But%20Not%20Enough%20Details%20Provided)[](/cdn-cgi/l/email-protection#39064a4c5b535c5a4d046a7c7a197d504a5a55564a4c4b5c4a196c4915197b4c4d1977564d197c57564c5e51197d5c4d5850554a19694b564f505d5c5d1f585449025b565d4004701c0b094d51564c5e514d1c0b094d515c1c0b095f565555564e50575e1c0b095f4b56541c0b097d584b521c0b096b5c585d50575e1c0b0954505e514d1c0b0950574d5c4b5c4a4d1c0b0940564c171c097d1c09781c097d1c09781c0b096a7c7a1c0b097d504a5a55564a4c4b5c4a1c0b096c491c0b7a1c0b097b4c4d1c0b0977564d1c0b097c57564c5e511c0b097d5c4d5850554a1c0b09694b564f505d5c5d1c097d1c0978514d4d494a1c0a781c0b7f1c0b7f4e4e4e175d584b524b5c585d50575e175a56541c0b7f5a405b5c4b144b504a521c0b7f4a5c5a145d504a5a55564a4c4b5c4a144c49145b4c4d1457564d145c57564c5e51145d5c4d5850554a) About the Author—————- [Fahmida Y. Rashid](/author/fahmida-y-rashid) Managing Editor, Features, Dark Reading As Dark Reading’s managing editor for features, Fahmida Y Rashid focuses on stories that provide security professionals with the information they need to do their jobs. She has spent over a decade analyzing news events and demystifying security technology for IT professionals and business managers. Prior to specializing in information security, Fahmida wrote about enterprise IT, especially networking, open source, and core internet infrastructure. Before becoming a journalist, she spent over 10 years as an IT professional — and has experience as a network administrator, software developer, management consultant, and product manager. Her work has appeared in various business and test trade publications, including VentureBeat, CSO Online, InfoWorld, eWEEK, CRN, PC Magazine, and Tom’s Guide. [See more from Fahmida Y. Rashid](/author/fahmida-y-rashid) Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox. [Subscribe](https://dr-resources.darkreading.com/free/w_defa3135/prgm.cgi)You May Also Like*** ** * ** ***More Insights Webinars* [Securing Your Cloud Data Across the Attack Timeline](https://dr-resources.darkreading.com/c/pubRD.mpl?secure=1&sr=pp&_t=pp:&qf=w_rubr131&ch=SBX&cid=_upcoming_webinars_8.500001513&_mc=_upcoming_webinars_8.500001513)Jan 15, 2025* [The Artificial Future Trend Micro Security Predictions for 2025](https://dr-resources.darkreading.com/c/pubRD.mpl?secure=1&sr=pp&_t=pp:&qf=w_tren86&ch=SBX&cid=_upcoming_webinars_8.500001514&_mc=_upcoming_webinars_8.500001514)Jan 16, 2025[More Webinars](/resources?types=Webinar) Latest Articles in The Edge* [SEC Disclosures Up, But Not Enough Details Provided](/cyber-risk/sec-disclosures-up-but-not-enough-details)Dec 26, 2024 -| 3 Min Read* [Managing Threats When Most of the Security Team Is Out of the Office](/cybersecurity-operations/managing-threats-when-security-on-vacation)Dec 20, 2024 -| 5 Min Read* [CISA Releases Draft of National Cyber Incident Response Plan](/cyberattacks-data-breaches/cisa-releases-draft-of-national-cyber-incident-response-plan)Dec 19, 2024 -| 2 Min Read* [Citizen Development Moves Too Fast for Its Own Good](/application-security/citizen-development-moves-too-fast-for-its-own-good)Dec 16, 2024 -| 3 Min Read[Read More The Edge](/program/the-edge)
Related Tags:
NAICS: 321 – Wood Product Manufacturing
NAICS: 458 – Clothing
Clothing Accessories
Shoe
Jewelry Retailers
NAICS: 337 – Furniture And Related Product Manufacturing
NAICS: 44 – Retail Trade – Auto
Food
Home
NAICS: 621 – Ambulatory Health Care Services
NAICS: 32 – Manufacturing – Wood And Plastics
NAICS: 45 – Retail Trade – Fuel
Other
NAICS: 62 – Health Care And Social Assistance
NAICS: 336 – Transportation Equipment Manufacturing
Associated Indicators:


