By: Adam Martin and Nathaniel SagibandaThe holiday season is a time of joy and relaxation, but it often brings an influx of corporate emails ranging from leave approvals to scheduling paid time off. The Cofense Phishing Defense Center (PDC) has recently intercepted a malicious phishing email masquerading as a legitimate end-of-year leave approval notice. Disguised as a formal HR communication, this email leverages the urgency and importance of year-end leave scheduling in order to trick the recipients into clicking a malicious link. This enables the threat actor to steal sensitive information via FormBook malware.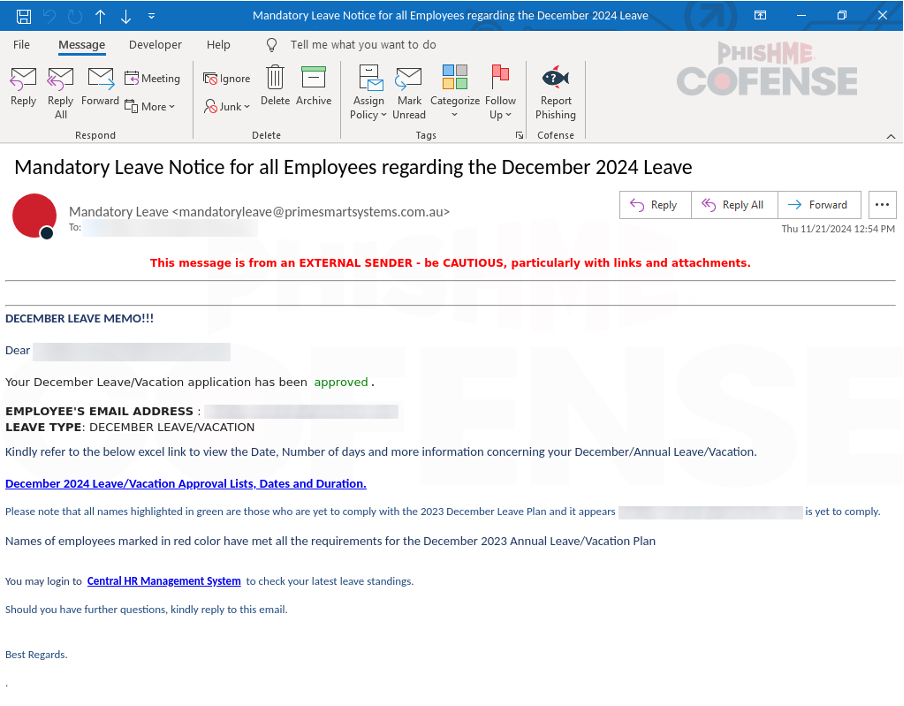Figure 1: The contents of the phishing email disguised as an HR noticeAs shown in Figure 1, the phishing email had the subject line *’Mandatory Leave Notice for all employees’* to mimic HR communications with professional language and seasonal relevance. The body claimed the recipient’s leave has been *’approved’* , included a link (*’December 2024 Leave/Vacation Approval Lists, Dates and Duration’* ) to view the approved dates, and prompted users to get more details by logging into the *’Central HR Management System’.* While it is a well-crafted email, a few red flags are apparent when taking a closer look. The email was flagged as an EXTERNALSENDER which is a clear indication that the email did not originate within the company. This is because the sender’s email address did not match the organization’s domain. Upon hovering over the link (as shown in Figure 2), a *SendGrid* -wrapped URL is revealed, which redirects to a malicious domain hosting malware. Clicking on the wrapped link further redirects to a ***Discordapp*** URL (Figure 3), where the malware is hosted and subsequently downloaded.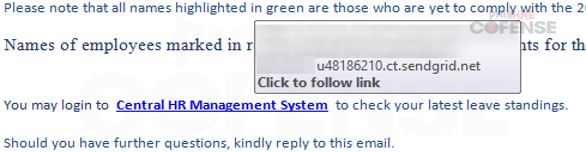Figure 2: The embedded malicious link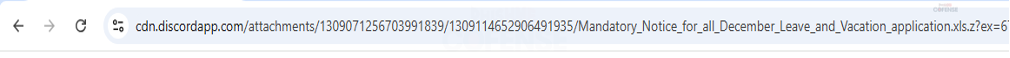Figure 3: Redirected to discordapp URL to download the attachment**Technical Analysis: Static Attributes**VT Tags from AV Vendors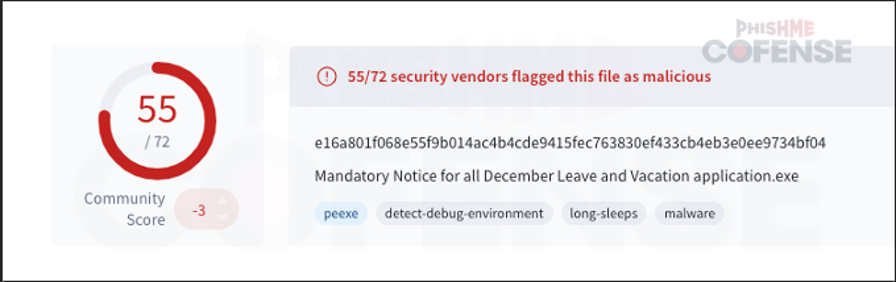Figure 4: VirusTotal detections and file hash for the malware sampleVarious antivirus vendor detections for this sample note that it is either a generic AutoIt injector or a FormBook sample. Below is a sample of vendor tags assigned to specific malware family’s composition / attributes.* A Variant Of Win32/Injector.Autoit.GQO* Trojan.Injector.AutoIt* Trojan:Win32/AutoitInject.HNA!MTB* Trojan.Win32.FORMBOOK.YXEKUZ**Initial Download**Once the malicious link is accessed by the victim, a .zip file will be downloaded to the default downloads directory. As shown in Figure 5, a potential victim may think that the .zip file contains a .xls related to a notice for employee PTO for the Christmas Period.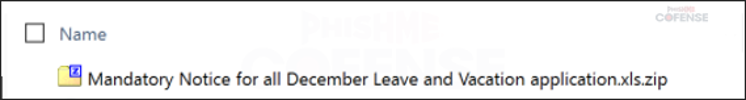Figure 5: .zip file downloaded to default download directoryHowever, Figure 6 shows that the .zip file contains an executable file.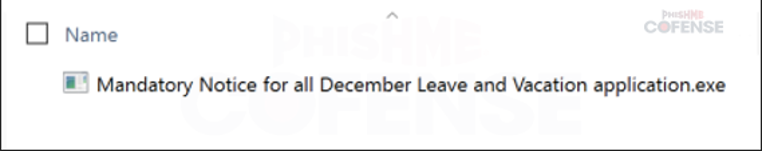Figure 6: When extracted, the .zip file contains an executable file payload**File Identification**The first step in the analysis of externally downloaded files is identifying the file type. This identification process is pivotal because malicious downloads often claim to be a different file type than they are (i.e. a fake PDF file that is actually an executable). As illustrated below in Figure 7, our mandatory leave notice is an AutoIt compiled executable. AutoIt, like many other legitimate software development and scripting tools, has been used as a method to perform malicious actions by embedding scripts within an otherwise useful framework. In this case, the sample uses AutoIt as a parent process to inject a script into a target process, in this case, Utilman.exe. The final injection target process is then used to run FormBook in memory.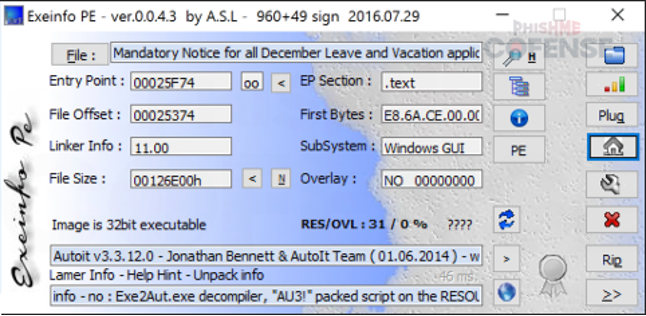Figure 7: The sample is an AutoIt compiled executable**Import Table**When analyzing the libraries imported by the malware in Figure 8, there is an indication that there will be network traffic with API calls like InternetReadFile and InternetOpenW which is to be expected as FormBook/Xloader uses HTTP for C2 interaction.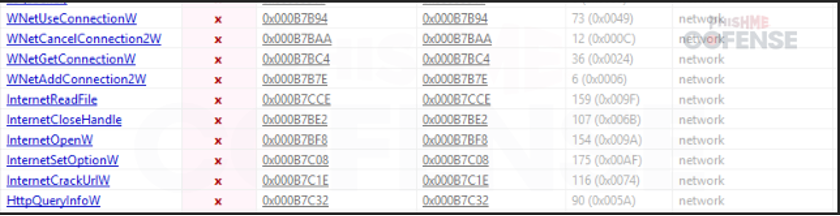Figure 8: Network API calls imported by the sampleAdditionally, various device hooking and input-output monitoring calls such as GetKeyboardLayout, VkKeyScanW, and SetCapture (Figure 9) are imported, indicating that MITRE Technique T1056 (Input Capture) is utilized here.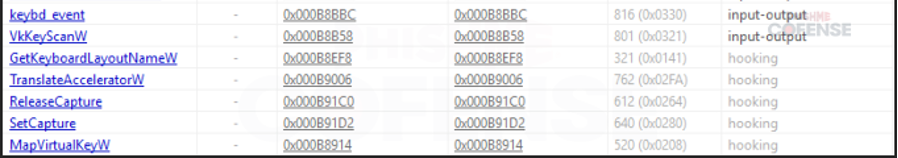Figure 9: Various imported API calls for device hooking and input-output monitoring**Debugger check**The IsDeguggerPresent API call is a staple of anti-analysis techniques, and Formbook is no exception to the rule in using it to prevent analysis.* If a debugger is detected after the IsDebuggerPresent call (eax is not 0), the execution jumps to 0x00471CC1.* This path displays a **message box** with the following details: * Caption: Derived from byte_4B28F4 * Message: *’This is a third-party compiled AutoIt script.’* * This serves to obfuscate the malware’s true intent by masquerading as a benign script and preventing analysts from being able to further analyze the sample without disabling the debugger check.* After showing the message box, the program jumps to 0x004B28F4, where it cleans up and exits.* If no debugger is detected (eax is 0), execution continues without displaying the message box.This mechanism disrupts debugging efforts and attempts to prevent the malware from being analyzed.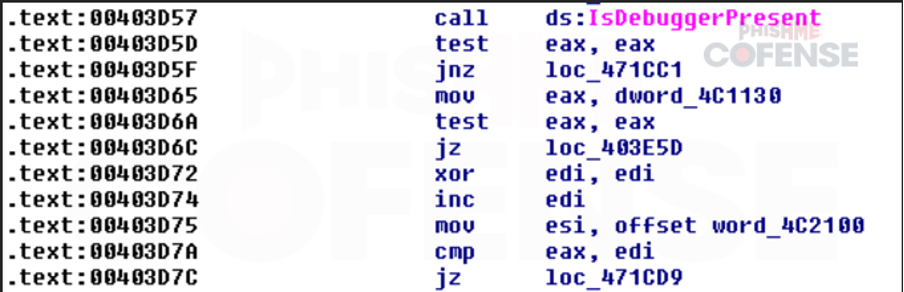Figure 10: The debugger detection function used by the malware to impede analysis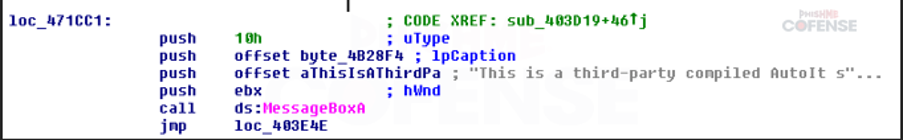Figure 11: If the malware detects a debugger, it will display a deceptive message and end without running any further payloads**Technical Analysis: Dynamic Actions**When the FormBook binary is executed, it begins by performing initial reconnaissance and setup tasks, such as unpacking itself, evading detection, and identifying targets for injection. It’ll use explorer.exe to select its desired infection process (in this case svchost.exe), then spawn svchost.exe by leveraging Windows API calls, and finally inject part of its malicious code into it. This step uses svchost.exe as an intermediate or ‘staging’ process because it is a trusted Windows service and unlikely to ring any alarms. This can be seen below in a suspended state.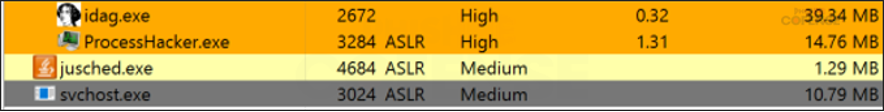Figure 12: The sample uses svchost.exe as an intermediate process to inject a malicious payload to* Formbook then spawns UtilMan.exe (or injects code into an already running instance).* The final stage payload is transferred into UtilMan.exe, which now acts as the primary host for the malicious activity.**Malicious Activity Resides in UtilMan.exe*** All core malicious actions, such as credential harvesting, keylogging, and data exfiltration, are executed from within UtilMan.exe.* This process inherits the legitimacy of a system process, making it harder for security software to detect.Utilman.exe strings extracted from memory show Formbook collecting system passwords for later data exfiltration.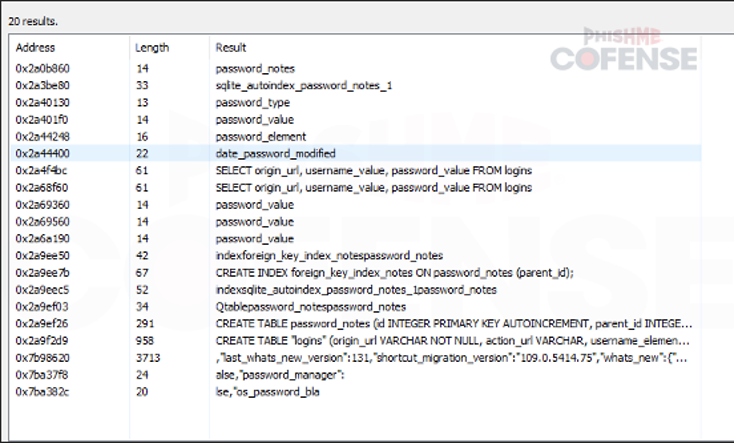Figure 13 strings extracted from Utilman.exe**Mitre Tactics Employed**TechniquesDescriptionTacticValid accounts T1078Abuse credentials of existing accounts.Initial Access,Native API T1106compiled with AutoItExecutionDLL side loading T1574.002execute their own malicious payloads by side-loading DLLs.Defense EvasionProcess injection T1055Privilege EscalationOS credential dumping T1003attempt to dump credentials to obtain account login and credential material, normally in the form of a hash or a clear text password, from the operating system and softwareCredential access**Conclusion**This end-of-year-themed phishing email highlights how cybercriminals exploit trust, urgency, and seasonal relevance to infiltrate organizations. While the email appeared legitimate, scrutiny of external sender warnings, suspicious links, and generic formatting exposed its malicious intent. In this case, the attackers intended to deploy Formbook, a dangerous information stealer capable of harvesting credentials, logging keystrokes, and exfiltrating sensitive data. Such malware thrives on unsuspecting victims clicking malicious links or downloading compromised files.To protect yourself and your organization, it is important to teach employees these best practices: – Verify email sources: ensure sender domains match official channels. – Inspect links before clicking: hover over hyperlinks to confirm legitimacy. – Be wary of urgent requests: pause and evaluate emails pushing immediate access.Conducting regular training to recognize phishing attempts and malware threats like Formbook ensures a secure and worry-free season.****IOCs****URLIP Address/RolehXXp://www-[.-]7261ltajbc.bond/cbbl/?aX=paPsyhkx/nE5gApOwy99MfqP09TNE5t/PnUzFNUQtr02YB3yPLZBROPMMVRkOMhc4Y+f4YmWe6fkW51HF6bKgtyZQkenfIZhWb80W8tCuarD22utTQitiVGOqTZqIbb31lBrl2g=-&YHuX=yftHppt154-[.-]12-[.-]28-[.-]184hxxps-[://-]www-[.-]google-[.-]com/url?q=hxxps-[://-]cdn-[.-]discordapp-[.-]com/attachments/ 1309071256703991839/1309114652906491935/ Mandatory_Notice_for_all_December_Leave_and_Vacation_application-[.-]xls-[.-]zUrl Embedded in EmailTypeInformationFile Name:Mandatory Notice for all December Leave and Vacation application.exeMD5:201ad7754669b4d766349530adcca029SHA256:E16A801F068E55F9B014AC4B4CDE9415FEC763830EF433CB4EB3E0EE9734BF04Size:1.15 MB (1207808 bytes)File Name:Mandatory_Notice_for_all_December_Leave_and_Vacation_application.xls.zMD5:
7e78e1c67017e5fd2f63c2744358198fSHA2560583eb0dfc05ee6889f49e0da5cb7e48128cb41db627a64045d74e11fa85754cSize:
684.30 KB (700728 bytes)
Related Tags:
NAICS: 923 – Administration Of Human Resource Programs
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
NAICS: 51 – Information
TA0006 – Credential Access
TA0010 – Exfiltration
TA0043 – Reconnaissance
Blog: Cofense
TA0004 – Privilege Escalation
Associated Indicators:
https://cdn.discordapp.com/attachments/
http://www.7261ltajbc.bond/cbbl/?aX
www.7261ltajbc.bond
0583EB0DFC05EE6889F49E0DA5CB7E48128CB41DB627A64045D74E11FA85754C
201AD7754669B4D766349530ADCCA029
7E78E1C67017E5FD2F63C2744358198F
E16A801F068E55F9B014AC4B4CDE9415FEC763830EF433CB4EB3E0EE9734BF04


