Threat actors increasingly use Scalable Vector Graphics (SVG) attachments to display phishing forms or deploy malware while evading detection.Most images on the web are JPG or PNG files, which are made of grids of tiny squares called pixels. Each pixel has a specific color value, and together, these pixels form the entire image.SVG, or Scalable Vector Graphics, displays images differently, as instead of using pixels, the images are created through lines, shapes, and text described in textual mathematical formulas in the code.For example, the following text will create a rectangle, a circle, a link, and some text: Hello, SVG! When opened in a browser, the file will generate the graphics described by the text above.  **Generated SVG image** *Source: BleepingComputer*As these are vector images, they automatically resize without losing any loss to image quality or the shape, making them ideal for use in browser applications that may have different resolutions.Using SVG attachments to evade detection—————————————-The use of SVG attachments in phishing campaigns is nothing new, with BleepingComputer reporting about their usage in previous [Qbot malware campaigns](https://www.bleepingcomputer.com/news/security/attackers-use-svg-files-to-smuggle-qbot-malware-onto-windows-systems/) and as a way to [hide malicious scripts](https://www.bleepingcomputer.com/news/security/new-blank-image-attack-hides-phishing-scripts-in-svg-files/).However, threat actors are increasingly using SVG files in their phishing campaigns according to security researcher [MalwareHunterTeam](https://x.com/malwrhunterteam), who shared recent samples -[[1](https://x.com/malwrhunterteam/status/1857407160528842891), [2](https://x.com/malwrhunterteam/status/1857518555442430184)-] with BleepingComputer.These samples, and others seen by BleepingComputer, illustrate how versatile SVG attachments can be as they not only allow you to display graphics but can also be used to display HTML, using the – element, and execute JavaScript when the graphic is loaded.This allows threat actors to create SVG attachments that not only display images but also create phishing forms to steal credentials.As shown below, a recent SVG attachment -[[VirusTotal](https://www.virustotal.com/gui/file/ae08802026984b53438e1b3b2f2aa21839c165fae88493bfb8f31c4d064b7068)-] displays a fake Excel spreadsheet with a built-in login form, that when submitted, sends the data to the threat actors. 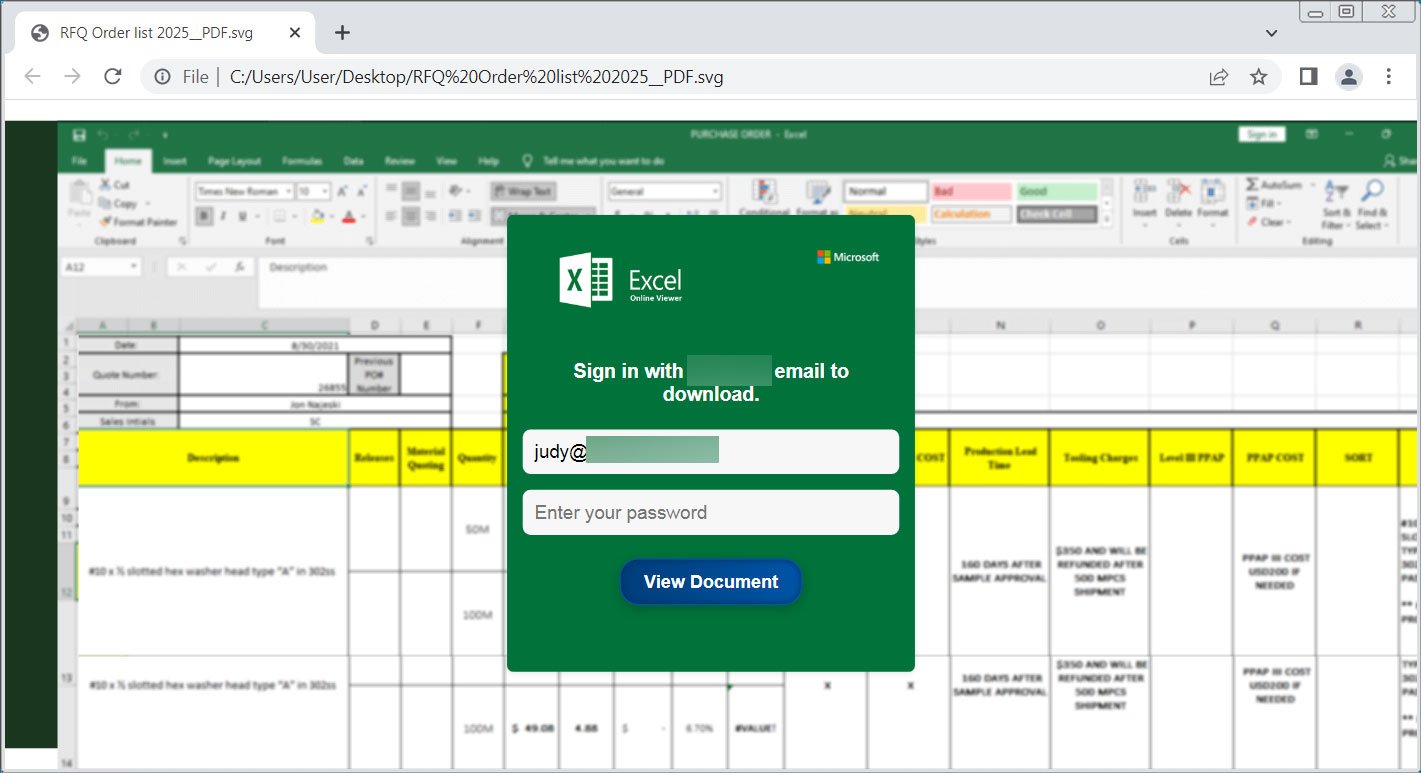 **SVG attachment showing a phishing form** *Source: BleepingComputer*Other SVG attachments used in a recent campaign -[[VirusTotal](https://www.virustotal.com/gui/file/0e857464f66465ad0308d8f779b2448a0a4575556e2cffee2e574ce99ddf18ad)-] pretend to be official documents or requests for more information, prompting you to click the download button, which then downloads malware from a remote site. 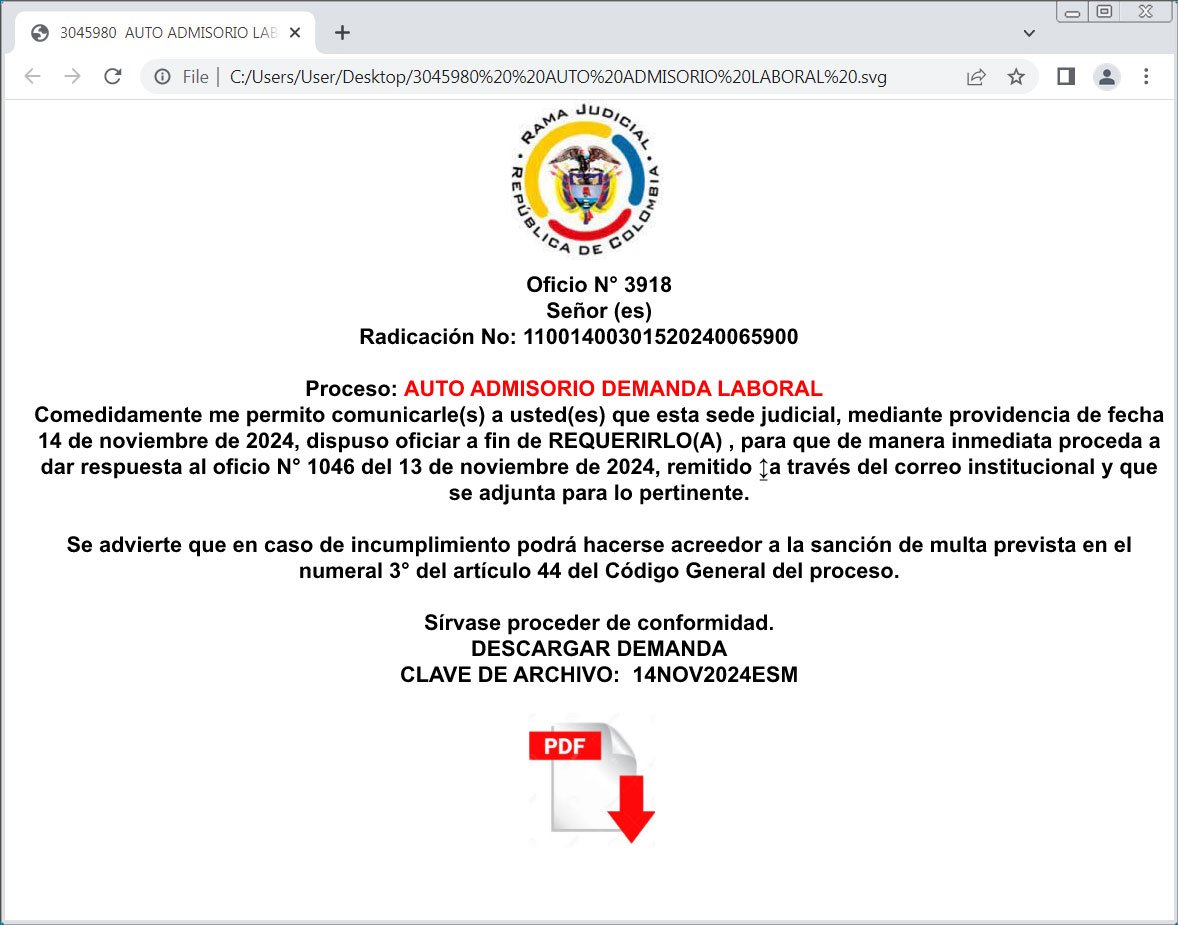 **SVG attachment used to distribute malware** *Source: BleepingComputer*Other campaigns utilize SVG attachments and embedded JavaScript to automatically redirect browsers to sites hosting phishing forms when the image is opened.The problem is that since these files are mostly just textual representations of images, they tend not to be detected by security software that often. From samples seen by BleepingComputer and uploaded to VirusTotal, at the most, they have one or two detections by security software.With that said, receiving an SVG attachment is not common for legitimate emails, and should immediately be treated with suspicion.Unless you are a developer and expect to receive these types of attachments, it is safer to delete any emails containing them. ### Related Articles:[Bumblebee malware returns after recent law enforcement disruption](https://www.bleepingcomputer.com/news/security/bumblebee-malware-returns-after-recent-law-enforcement-disruption/)[ESET partner breached to send data wipers to Israeli orgs](https://www.bleepingcomputer.com/news/security/eset-partner-breached-to-send-data-wipers-to-israeli-orgs/)[Clever ‘GitHub Scanner’ campaign abusing repos to push malware](https://www.bleepingcomputer.com/news/security/clever-github-scanner-campaign-abusing-repos-to-push-malware/)[Botnet exploits GeoVision zero-day to install Mirai malware](https://www.bleepingcomputer.com/news/security/botnet-exploits-geovision-zero-day-to-install-mirai-malware/)[Fraud network uses 4,700 fake shopping sites to steal credit cards](https://www.bleepingcomputer.com/news/security/fraud-network-uses-4-700-fake-shopping-sites-to-steal-credit-cards/)
Related Tags:
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
NAICS: 51 – Information
NAICS: 928 – National Security And International Affairs
Bumblebee
Pinkslipbot
Blog: BleepingComputer
Associated Indicators:


