  Menu* [Tools](https://unit42.paloaltonetworks.com/tools/)* [ATOMs](https://unit42.paloaltonetworks.com/atoms/)* [Security Consulting](https://www.paloaltonetworks.com/unit42)* [About Us](https://unit42.paloaltonetworks.com/about-unit-42/)* [**Under Attack?**](https://start.paloaltonetworks.com/contact-unit42.html) * [Threat Research Center](https://unit42.paloaltonetworks.com ‘Threat Research’)* [Threat Actor Groups](https://unit42.paloaltonetworks.com/category/threat-actor-groups/ ‘Threat Actor Groups’)* [Malware](https://unit42.paloaltonetworks.com/category/malware/ ‘Malware’) [Malware](https://unit42.paloaltonetworks.com/category/malware/)Chinese APT Abuses VSCode to Target Government in Asia====================================================== 9 min read Related Products Advanced DNS SecurityAdvanced URL FilteringAdvanced WildFireCloud-Delivered Security ServicesCode to Cloud PlatformCortexCortex XDRCortex XSIAMPrisma CloudPrisma Cloud Compute *  By: * [Tom Fakterman](https://unit42.paloaltonetworks.com/author/tom-fakterman/)*  Published:6 September, 2024 at 3:00 PM PDT*  Categories: * [Malware](https://unit42.paloaltonetworks.com/category/malware/) * [Threat Actor Groups](https://unit42.paloaltonetworks.com/category/threat-actor-groups/)*  Tags: * [Advanced Persistent Threat](https://unit42.paloaltonetworks.com/tag/advanced-persistent-threat/) * [China](https://unit42.paloaltonetworks.com/tag/china/) * [DLL Sideloading](https://unit42.paloaltonetworks.com/tag/dll-sideloading/) * [Dropbox](https://unit42.paloaltonetworks.com/tag/dropbox/) * [Espionage](https://unit42.paloaltonetworks.com/tag/espionage/) * [Government](https://unit42.paloaltonetworks.com/tag/government/) * [Microsoft Visual Studio](https://unit42.paloaltonetworks.com/tag/microsoft-visual-studio/) * [Mimikatz](https://unit42.paloaltonetworks.com/tag/mimikatz/) * [ShadowPad](https://unit42.paloaltonetworks.com/tag/shadowpad/) * [TA416](https://unit42.paloaltonetworks.com/tag/ta416/) * [ToneShell](https://unit42.paloaltonetworks.com/tag/toneshell/) * [VSCode](https://unit42.paloaltonetworks.com/tag/vscode/)* * Share* * * * * * * Executive Summary—————–Unit 42 researchers recently found that Stately Taurus abused the popular Visual Studio Code software in espionage operations targeting government entities in Southeast Asia. Stately Taurus is a Chinese advanced persistent threat (APT) group that carries out cyberespionage attacks.This threat actor used Visual Studio Code’s embedded reverse shell feature to gain a foothold in target networks. This is a relatively new technique that [a security researcher discovered](https://medium.com/@truvis.thornton/visual-studio-code-embedded-reverse-shell-and-how-to-block-create-sentinel-detection-and-add-e864ebafaf6d) in 2023. According to our telemetry, this is the first time a threat actor used it in the wild.We assess that this campaign is a direct continuation of a [previously reported campaign](https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/)that we attributed with moderate-high confidence to Stately Taurus. We come to this conclusion based on consideration of the TTPs, timeline and victimology targeting government entities in Southeast Asia.We will also discuss a connection between the Stately Taurus activity and a second cluster of activity occurring simultaneously in the same targeted environment that leveraged the ShadowPad backdoor.Palo Alto Networks customers receive better protection against threats discussed in this article through the following products and services, which we detail further in the Conclusion section:* [Advanced WildFire](https://www.paloaltonetworks.com/blog/prisma-cloud/prisma-cloud-and-wildfire-integration/)* [Advanced URL Filtering](https://www.paloaltonetworks.com/network-security/advanced-url-filtering)* [Advanced DNS Security](https://www.paloaltonetworks.com/network-security/dns-security)* [Cortex XDR](https://www.paloaltonetworks.com/cortex/cortex-xdr)* [Cortex XSIAM](https://docs-cortex.paloaltonetworks.com/p/XSIAM)* [Prisma Cloud Compute](https://www.paloaltonetworks.com/resources/datasheets/prisma-cloud-compute-edition-aag)If you think you might have been compromised or have an urgent matter, contact the [Unit 42 Incident Response team](https://start.paloaltonetworks.com/contact-unit42.html).**Related Unit 42 Topics** [**China**](https://unit42.paloaltonetworks.com/tag/china/), **[DLL Sideloading](https://unit42.paloaltonetworks.com/tag/dll-sideloading/)**The Rare Use of Visual Studio Code Abuse—————————————-One of the novel techniques Stately Taurus used to bypass security protections leverages Visual Studio Code’s embedded reverse shell feature to execute arbitrary code and deliver additional payloads. Truvis Thornton described this technique in a [Medium post](https://medium.com/@truvis.thornton/visual-studio-code-embedded-reverse-shell-and-how-to-block-create-sentinel-detection-and-add-e864ebafaf6d)in September 2023, but this is the first time we’ve observed threat actors abusing this technique in the wild.To abuse Visual Studio Code for malicious purposes, an attacker can use the portable version of code.exe (the executable file for Visual Studio Code), or an already installed version of the software. By running the command code.exe tunnel, an attacker receives a link that requires them to log into GitHub with their own account.After logging in, the attacker is redirected to a Visual Studio Code web environment that is connected to the compromised machine. They are then permitted to execute commands and scripts, and to create new files on the infected machine.Stately Taurus used this technique to deliver malware to infected environments, perform reconnaissance and exfiltrate sensitive data. To establish constant access to the reverse shell, the attacker created persistence for a script named startcode.bat using a scheduled task that is responsible for starting the shell.Figure 1 shows the process tree for code.exe abuse in Cortex XDR.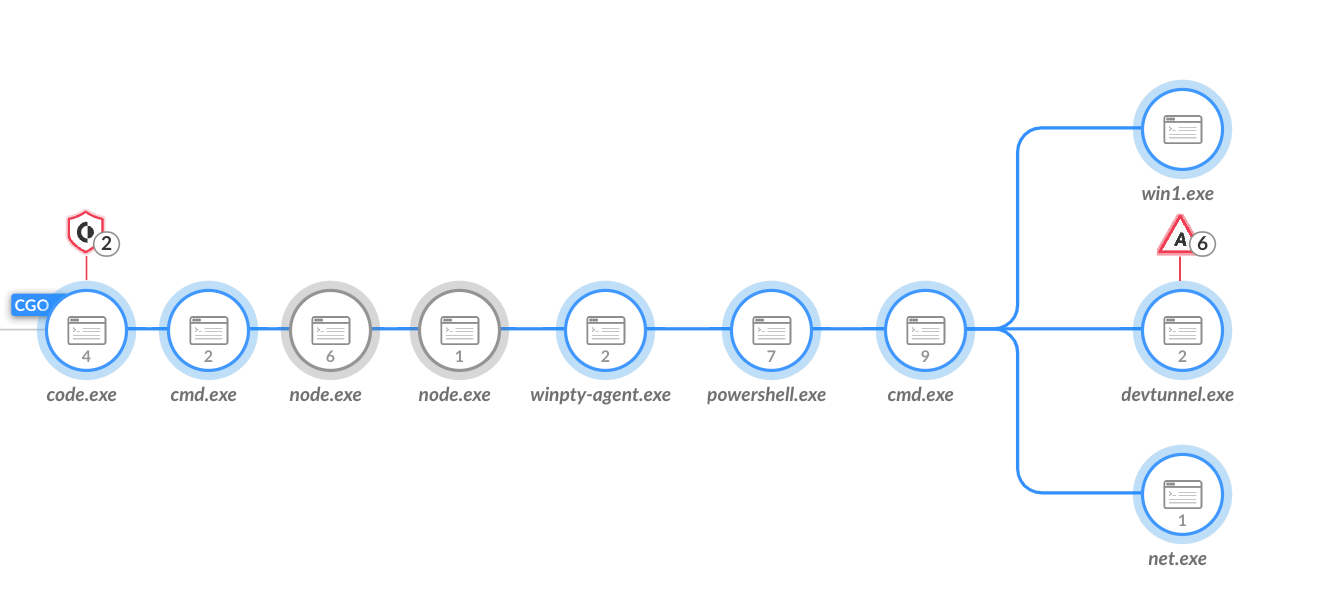 Figure 1. Process tree of the code.exe abuse in Cortex XDR.The Connection to Stately Taurus——————————–In September 2023, we discussed a campaign that was [attributed to Stately Taurus](https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/), which leveraged the [ToneShell](https://malpedia.caad.fkie.fraunhofer.de/details/win.toneshell) backdoor as one of its main tools. During this campaign, Stately Taurus used ToneShell to archive files for exfiltration, protecting the RAR archives with a unique password.The password was 13 characters long, using upper and lower case letters as well as digits. By tracking this unique password in our telemetry, we were able to find additional Stately Taurus activity in the same targeted environment.We concluded that this campaign is a continuation of the Stately Taurus activity we reported in this campaign due to the following factors:* The use of the same unique password* Additional TTPs* Timeline* Victimology targeting governmental entities in Southeast AsiaFigure 2 presents the connections between the components of Stately Taurus.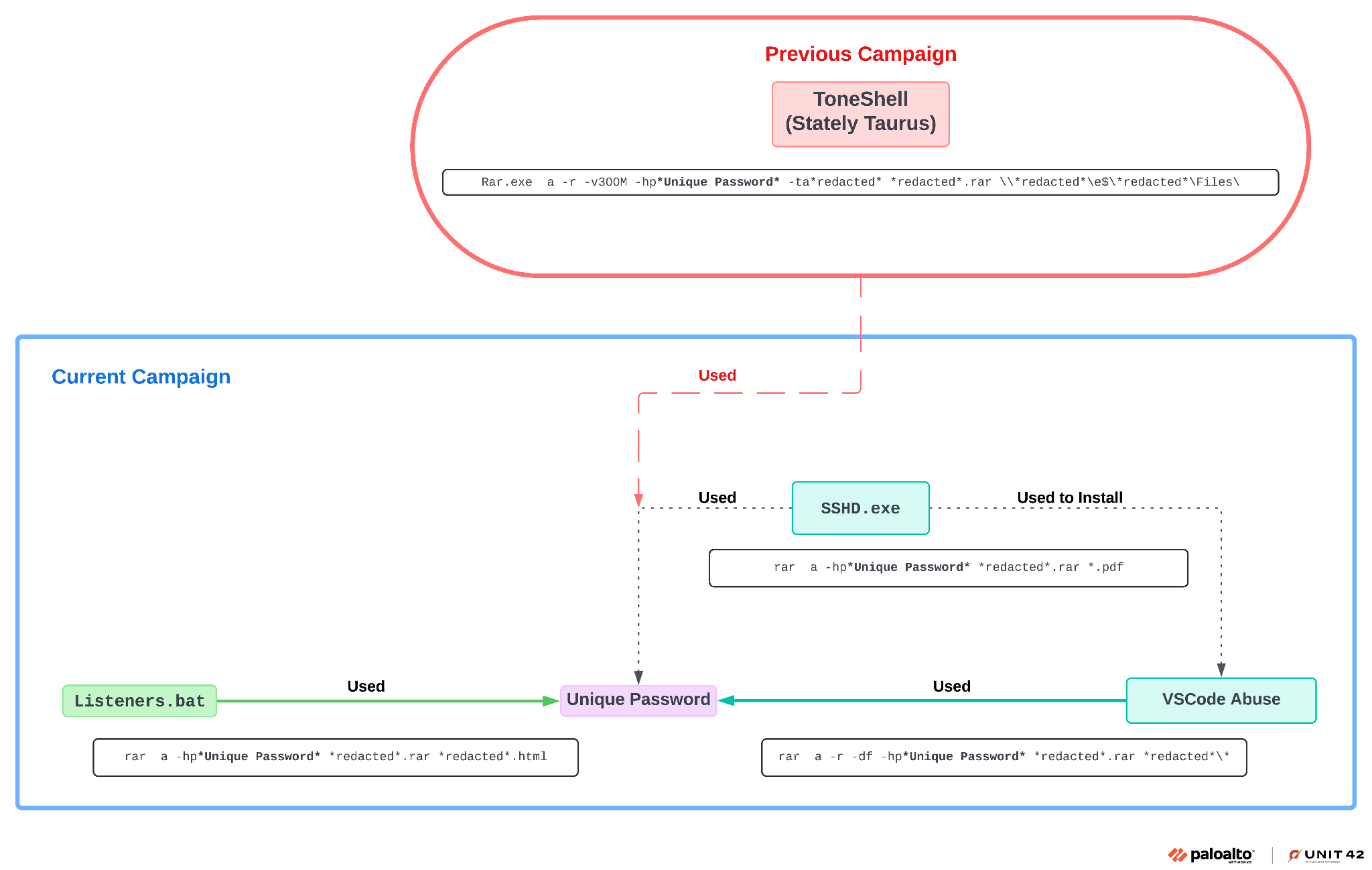 Figure 2. Connections between different components of the campaign and the unique Stately Taurus password.[Stately Taurus](https://unit42.paloaltonetworks.com/threat-actor-groups-tracked-by-palo-alto-networks-unit-42/#:~:text=Stately%20Taurus%20is%20a%20China%2Dbased%20cyberespionage%20threat%20actor%20that%20was%20first%20observed%20in%202017%2C%20but%20they%20may%20have%20been%20conducting%20operations%20since%20at%20least%202012) (aka Mustang Panda, BRONZE PRESIDENT, RedDelta, Luminous Moth, Earth Preta and Camaro Dragon) has been operating since at least 2012. Stately Taurus is a Chinese APT group that routinely conducts cyberespionage campaigns targeting [government entities](https://www.darkreading.com/endpoint-security/group-tied-to-china-s-mustang-panda-targets-european-governments-with-smugx), as well as [religious and other nongovernmental](https://www.recordedfuture.com/blog/reddelta-targets-catholic-organizations) organizations across [Europe](https://www.darkreading.com/endpoint-security/group-tied-to-china-s-mustang-panda-targets-european-governments-with-smugx) and [Asia](https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/#post-130090-_z4kcskcif3h6).Additional TTPs Related to the Stately Taurus Cluster—————————————————–* **Sshd.exe**: The attacker used [OpenSSH](https://learn.microsoft.com/en-us/windows-server/administration/openssh/openssh_server_configuration) (sshd.exe) to execute commands, transfer files and spread across the environment as shown in Figure 3. OpenSSH allows the user to connect to a remote machine via SSH.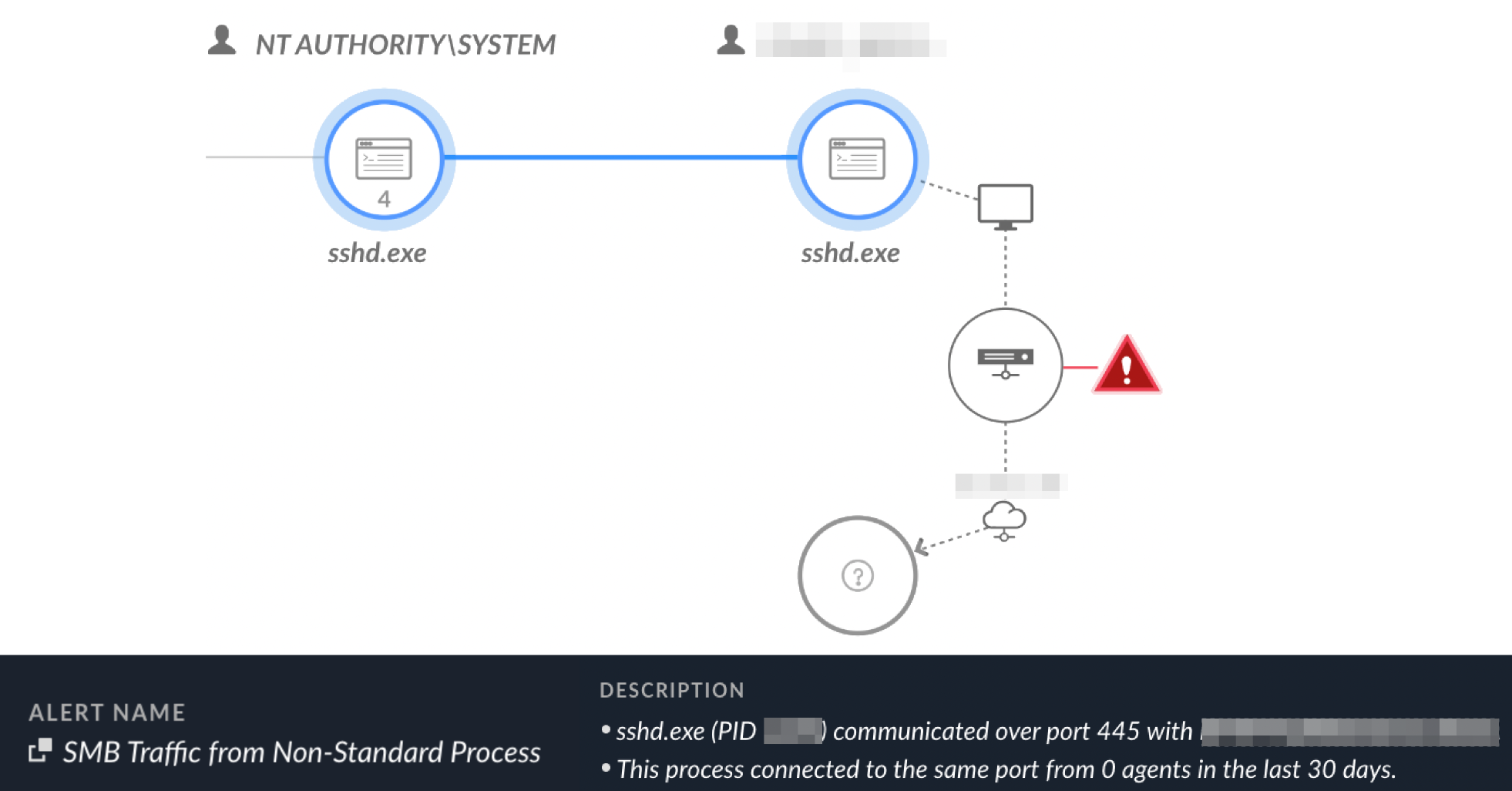 Figure 3. Sshd.exe used for lateral movement shown in Cortex XDR.* **SharpNBTScan:** The attackers used [SharpNBTScan](https://github.com/BronzeTicket/SharpNBTScan) (renamed as win1.exe) to perform scanning in the environment* **Listeners.bat** : On some occasions the attackers used a batch file named Listeners.bat to archive files for exfiltration### ExfiltrationAs part of this operation, Stately Taurus attempted to exfiltrate sensitive information from different machines. The attacker executed rar.exe remotely via [SMB](https://en.wikipedia.org/wiki/Server_Message_Block). Next, they tried to iterate and archive all drives from A-Z on remote machines, as shown in Figure 4.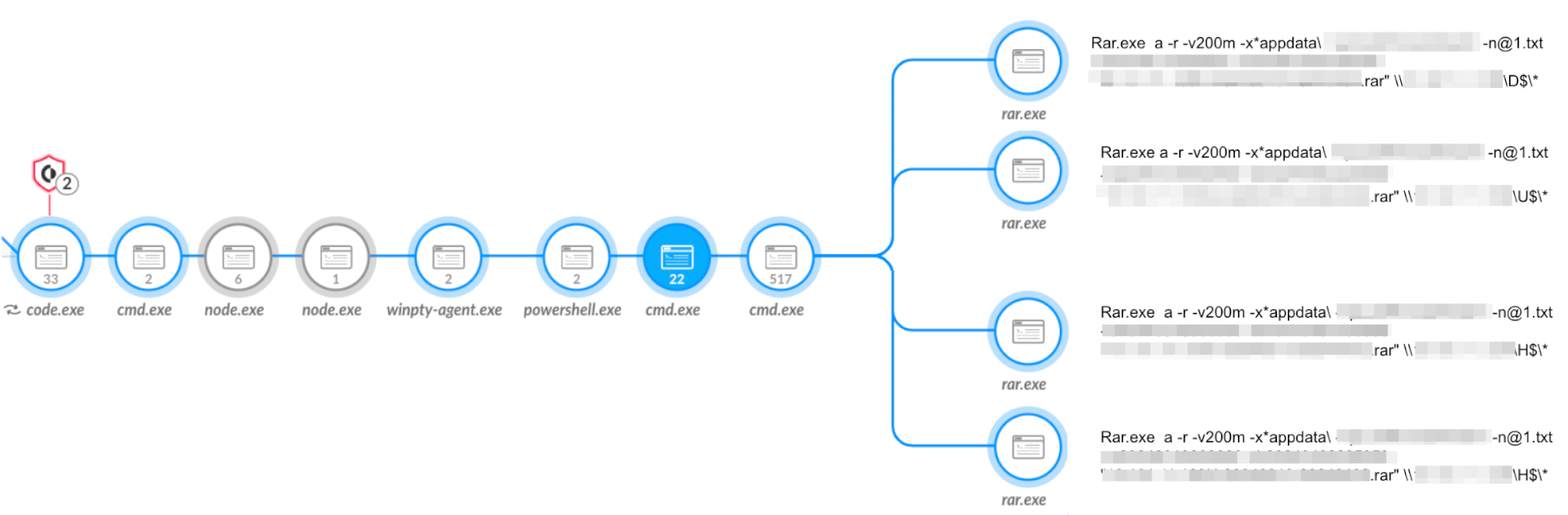 Figure 4. Attacker uses code.exe to archive folders from remote machines shown in Cortex XDR.To exfiltrate the archived files, the attacker used [curl](https://en.wikipedia.org/wiki/Server_Message_Block) to upload the files to Dropbox, which is a legitimate file hosting service. The attacker used this service to blend in and exfiltrate the data without drawing too much attention.Stately Taurus used the same technique previously, as described in [our previous article](https://unit42.paloaltonetworks.com/stately-taurus-attacks-se-asian-government/). Figure 5 below shows the command line the attacker used for exfiltration. Figure 5. Data exfiltration using Dropbox.The Connection to a ShadowPad Activity————————————–While investigating the Stately Taurus cluster, we observed another cluster of activity in the same environment, occurring simultaneously and at times even on the same endpoints. This cluster of activity used the [ShadowPad backdoor](https://malpedia.caad.fkie.fraunhofer.de/details/win.shadowpad) as its main tool, from which attackers launched other activity. ShadowPad is modular malware that has been in use by multiple Chinese threat actors [since at least 2017](https://attack.mitre.org/software/S0596/).The connection between these two clusters includes the following overlap:* Following the origins of Listeners.bat (used in the Stately Taurus cluster) on an infected machine, we observed that the same network session that wrote Listeners.bat, wrote additional files and malware including the ShadowPad backdoor.* Listeners.bat also used the same unique password that the ToneShell backdoor from the Stately Taurus cluster used. Figure 6 depicts this connection.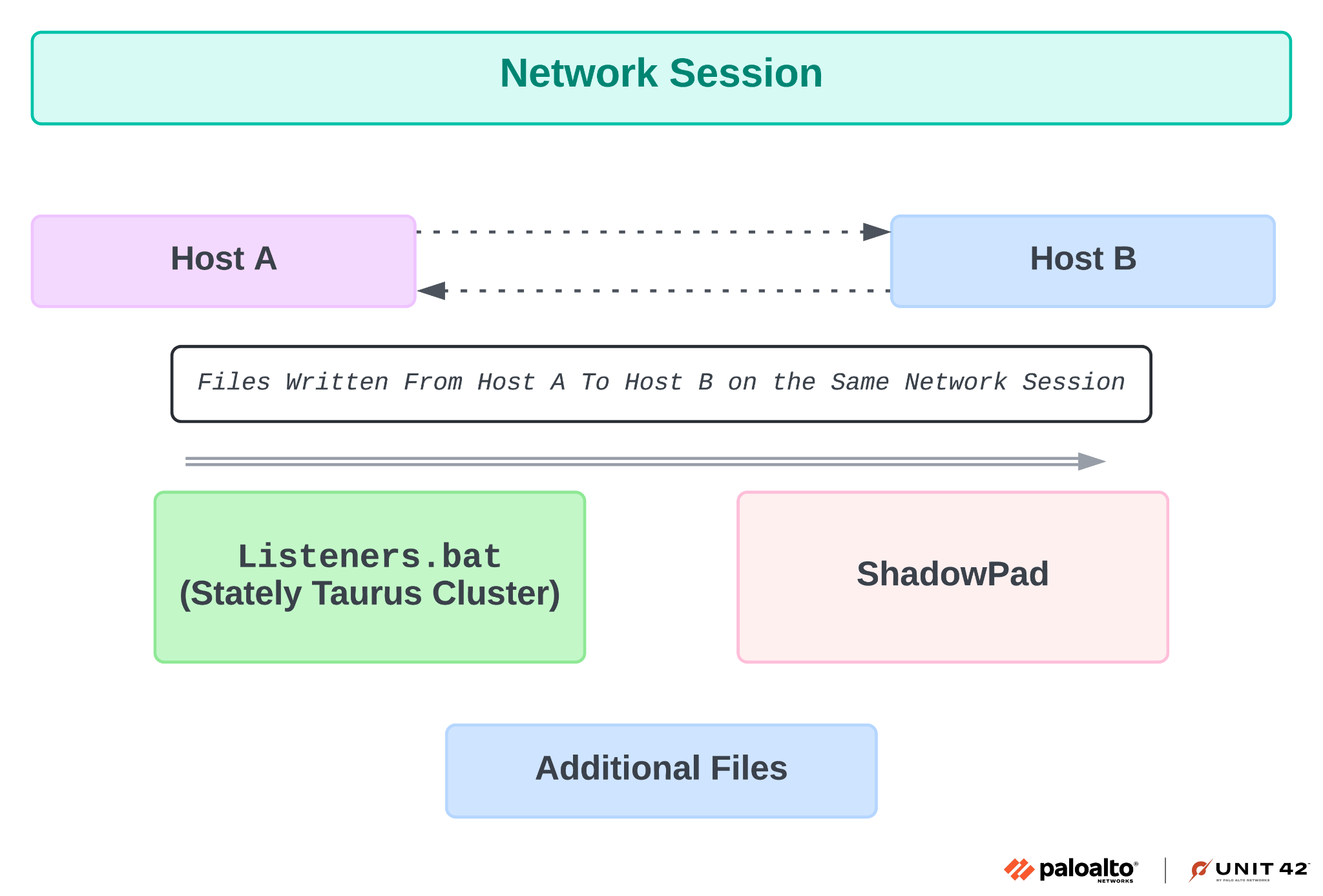 Figure 6. The observed connection between Listener.bat of Stately Taurus and ShadowPad.As of mid-August 2024, it is unclear whether these two clusters originated from the same threat actor. The fact that the two files originated from the same network session might indicate a connection between the ShadowPad activity to the VSCode activity linked to Stately Taurus.There could also be other possible scenarios to explain this connection. For example, it could be a joint effort between two Chinese APT groups or perhaps two different groups piggybacking on each other’s access.### The ShadowPad ActivityOne of the main tools used in this cluster is the [ShadowPad backdoor](https://malpedia.caad.fkie.fraunhofer.de/details/win.shadowpad).In the cluster described in this section, the attacker abused the legitimate process imecmnt.exe via DLL sideloading to load the ShadowPad module (imjp14k.dll). Imecmnt.exe is a [Microsoft Office Input Method Editor (IME)](https://learn.microsoft.com/en-us/windows/apps/design/input/input-method-editors) component.To keep ShadowPad running on victim machines, the attacker created persistence via a service. These service names are listed in the [Indicators of Compromise](#post-136600-_ydqdbjg0dngh) section below.Figure 7 shows how ShadowPad (imecmnt.exe renamed as update.exe to appear less suspicious) spawns and injects code into wmplayer.exe, which in turn spawns and injects code into dllhost.exe.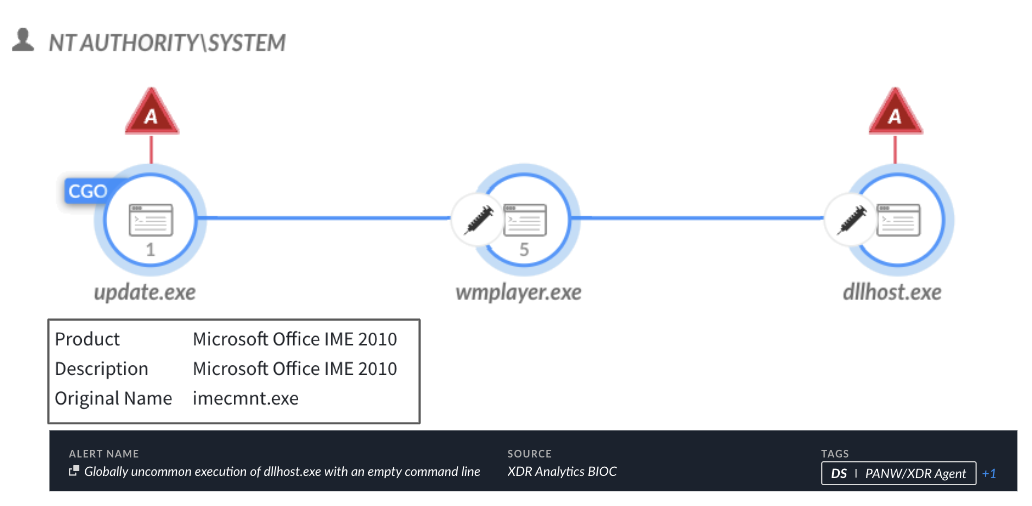 Figure 7. ShadowPad infection in Cortex XDR.Further TTPs related to the ShadowPad activity can be found in the Appendix section of the blog.Conclusion———-In this follow-up post, we shared new TTPs the Stately Taurus APT group used in an espionage campaign that targeted government entities in Southeast Asia. One of the most noteworthy techniques that we observed in this campaign is the abuse of Visual Studio Code for executing malicious code and gaining a foothold in the infected environment. According to our telemetry, this is the first time attackers have used this technique in the wild.In addition, we examined a connection we encountered between the Stately Taurus activity cluster and another cluster that used the ShadowPad backdoor in the same environment. As of mid-August 2024, the connection between these two clusters remains uncertain.Based on the forensic evidence and timeline, one could conclude that these two clusters originated from the same threat actor (Stately Taurus). However, there could be other possible explanations that can account for this connection, such as a collaborative effort between two Chinese APT threat actors.We encourage organizations to leverage our findings to inform the deployment of protective measures to defend against this threat group.**Protections and Mitigations**——————————-For Palo Alto Networks customers, our products and services provide the following coverage associated with this group:* [Advanced WildFire](https://www.paloaltonetworks.com/products/secure-the-network/wildfire) cloud-delivered malware analysis service accurately identifies the known samples as malicious.* [Advanced URL Filtering](https://www.paloaltonetworks.com/network-security/advanced-url-filtering) and [Advanced DNS Security](https://www.paloaltonetworks.com/network-security/dns-security) identify IP addresses associated with this group as malicious.* [Cortex XDR](https://www.paloaltonetworks.com/cortex/cortex-xdr?_gl=1*13pmp8e*_ga*NzQyNjM2NzkuMTY2NjY3OTczNw..*_ga_KS2MELEEFC*MTY2OTczNjA2MS4zMS4wLjE2Njk3MzYwNjEuNjAuMC4w) and [XSIAM](https://docs-cortex.paloaltonetworks.com/p/XSIAM) are designed to: * Prevent the execution of known malicious malware and prevent the execution of unknown malware using [Behavioral Threat Protection](https://www.paloaltonetworks.com/resources/guides/cortex-xdr-endpoint-protection-solution-guide) as well as machine learning based on the Local Analysis module. * Protect against credential gathering tools and techniques using the new Credential Gathering Protection available from Cortex XDR 3.4. * Protect from threat actors dropping and executing commands from web shells using Anti-Webshell Protection, newly released in Cortex XDR 3.4. * Protect against exploitation of different vulnerabilities including ProxyShell and ProxyLogon using the Anti-Exploitation modules as well as Behavioral Threat Protection. *
Related Tags:
NAICS: 922 – Justice
Public Order
Safety Activities
POISONPLUG.SHADOW
ShadowPad
Mustang Panda
TA416
BRONZE PRESIDENT
RedDelta
TA0010 – Exfiltration
TA0043 – Reconnaissance
Associated Indicators:


