 *Image: Midjourney*A new ransomware-as-a-service (RaaS) operation named Cicada3301 has already listed 19 victims on its extortion portal, as it quickly attacked companies worldwide.The new cybercrime operation is named after the mysterious 2012-2014 online/real-world game that involved elaborate cryptographic puzzles and used the same logo for promotion on cybercrime forums. However, it is unlikely there’s a connection between the two.The Cicada3301 RaaS first began promoting the operation and recruiting affiliates on June 29, 2024, in a forum post to the ransomware and cybercrime forum known as RAMP.However, BleepingComputer is aware of Cicada attacks as early as June 6, indicating that the gang was operating independently before attempting to recruit affiliates. 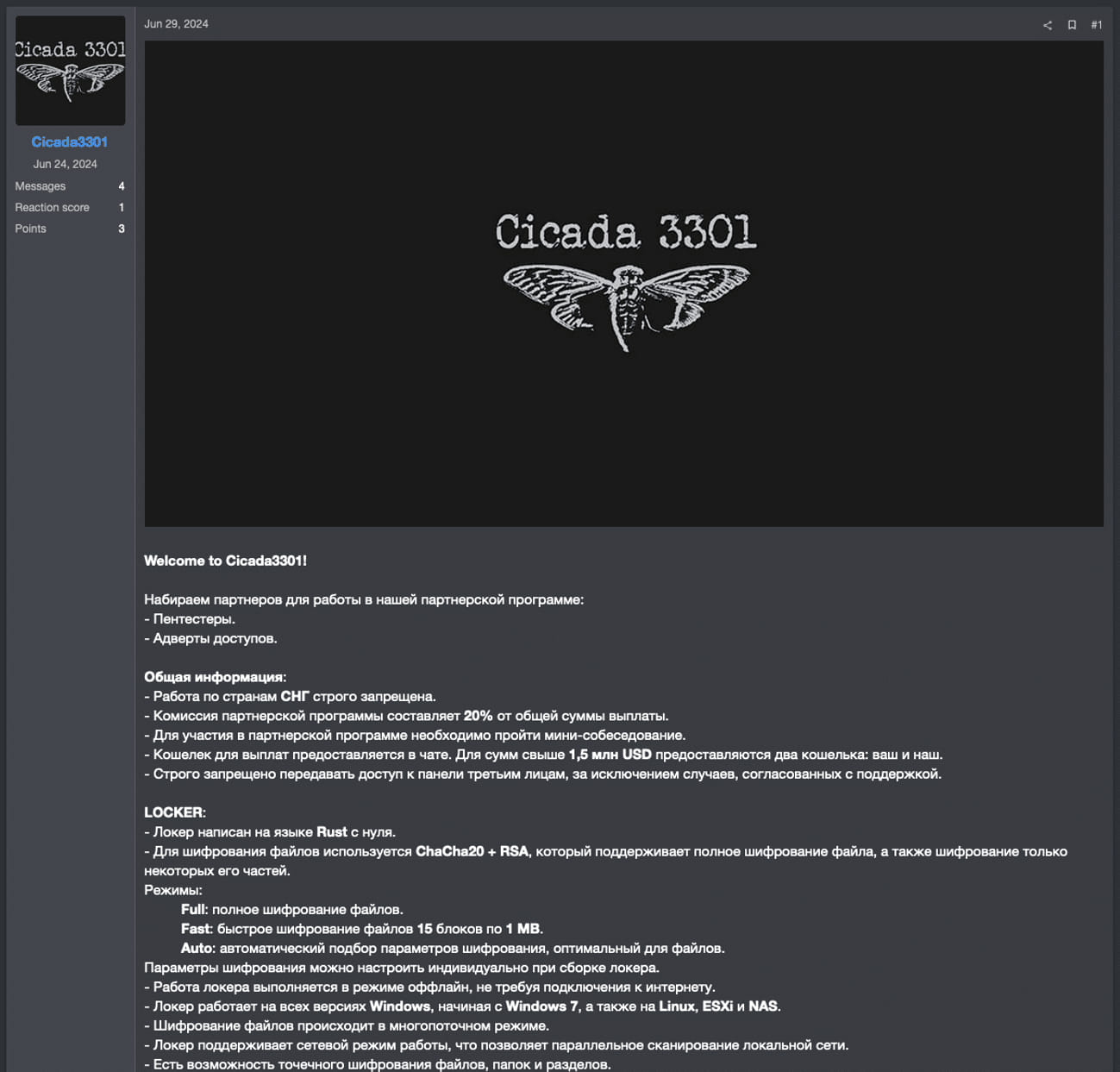 **Cicada3301 ransomware operator seeking affiliates on RAMP forums** *Source: Truesec*Like other ransomware operations, Cicada3301 conducts double-extortion tactics where they breach corporate networks, steal data, and then encrypt devices. The encryption key and threats to leak stolen data are then used as leverage to scare victims into paying a ransom.The threat actors operate a data leak site that is used as part of their double-extortion scheme.  **Cicada3301 extortion portal** *Source: BleepingComputer*An [analysis of the new malware by Truesec](https://www.truesec.com/hub/blog/dissecting-the-cicada) revealed significant overlaps between Cicada3301 and ALPHV/BlackCat, indicating a possible rebrand or a fork created by former ALPHV’s core team members.This is based on the fact that:* Both are written in Rust.* Both Use the ChaCha20 algorithm for encryption.* Both employ identical VM shutdown and snapshot-wiping commands.* Both use the same user interface command parameters, the same file naming convention, and the same ransom note decryption method.* Both use intermittent encryption on larger files.For context, ALPHV performed an [exit scam in early March 2024](https://www.bleepingcomputer.com/news/security/blackcat-ransomware-shuts-down-in-exit-scam-blames-the-feds/) involving fake claims about an FBI takedown operation after they stole a massive $22 million payment from Change Healthcare from one of their affiliates.Truesec has also found indications that the Cicada3301 ransomware operation may partner with or utilize the Brutus botnet for initial access to corporate networks. That botnet was previously associated with [global-scale VPN brute-forcing](https://www.bleepingcomputer.com/news/security/cisco-warns-of-password-spraying-attacks-targeting-vpn-services/) activities targeting Cisco, Fortinet, Palo Alto, and SonicWall appliances.It’s worth noting that the Brutus activity was first spotted two weeks after ALPHV shut down operations, so the link between the two groups still stands in terms of timelines.Yet another threat to VMware ESXi———————————Cicada3301 is a Rust-based ransomware operation with both Windows and Linux/VMware ESXi encryptors. As part of Truesec’s report, the researchers analyzed the VMWare ESXi Linux encryptor for the ransomware operation.Like [BlackCat](http://Access-token%20feature%20makes%20negotiations%20secret) and other ransomware families, such as RansomHub, a special key must be entered as a command line argument to launch the encryptor. This key is used to decrypt an encrypted JSON blob that contains the configuration that the encryptor will use when encrypting a device.Truesec says that the encryptor checks for the validity of the key by using it to decrypt the ransom note and, if successful, continues with the rest of the encryption operation.Its main function (linux_enc) uses the ChaCha20 stream cipher for file encryption and then encrypts the symmetric key used in the process with an RSA key. The encryption keys are generated randomly using the ‘OsRng’ function.Cicada3301 targets specific file extensions matching documents and media files and checks their size to determine where to apply intermittent encryption (->100MB) and where to encrypt the entire file contents (- /dev/null 2>&1; for i in `vim-cmd vmsvc/getallvms| awk -‘{print$1}-‘`;do vim-cmd vmsvc/snapshot.removeall $i & done > /dev/null 2>&1Cicada3301’s activities and rate of success indicate an experienced actor who knows what they’re doing, further supporting the hypothesis of an ALPHV reboot or at least utilizing affiliates with prior ransomware experience.The new ransomware’s focus on ESXi environments highlights its strategic design to maximize damage in enterprise environments that many threat actors now target for lucrative profits.By combining file encryption with the ability to disrupt VM operations and remove recovery options, Cicada3301 ensures a high-impact attack that affects entire networks and infrastructures, maximizing the pressure placed on victims. ### Related Articles:[New Eldorado ransomware targets Windows, VMware ESXi VMs](https://www.bleepingcomputer.com/news/security/new-eldorado-ransomware-targets-windows-vmware-esxi-vms/)[OneBlood’s virtual machines encrypted in ransomware attack](https://www.bleepingcomputer.com/news/security/onebloods-virtual-machines-encrypted-in-ransomware-attack/)[CISA warns of VMware ESXi bug exploited in ransomware attacks](https://www.bleepingcomputer.com/news/security/cisa-warns-of-vmware-esxi-bug-exploited-in-ransomware-attacks/)[Microsoft: Ransomware gangs exploit VMware ESXi auth bypass in attacks](https://www.bleepingcomputer.com/news/microsoft/microsoft-ransomware-gangs-exploit-vmware-esxi-auth-bypass-in-attacks/)[New Play ransomware Linux version targets VMware ESXi VMs](https://www.bleepingcomputer.com/news/security/new-play-ransomware-linux-version-targets-vmware-esxi-vms/)
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 52 – Finance And Insurance
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
NAICS: 922 – Justice
Public Order
Safety Activities
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 522 – Credit Intermediation And Related Activities
Associated Indicators:


