A massive Magniber ransomware campaign is underway, encrypting home users’ devices worldwide and demanding thousand-dollar ransoms to receive a decryptor.Magniber [launched in 2017](https://www.bleepingcomputer.com/news/security/goodbye-cerber-hello-magniber-ransomware/) as a successor to the Cerber ransomware operation when it was spotted being distributed by the Magnitude exploit kit.Since then, the ransomware operation has seen bursts of activity over the years, with the threat actors utilizing various methods to distribute Magniber and encrypt devices. These tactics include using [Windows zero-days](https://www.bleepingcomputer.com/news/security/microsoft-fixes-windows-zero-day-exploited-in-ransomware-attacks/), [fake Windows and browser updates](https://www.bleepingcomputer.com/news/security/magniber-ransomware-using-signed-appx-files-to-infect-systems/), and [trojanized software cracks and key generators](https://www.bleepingcomputer.com/news/security/fake-windows-10-updates-infect-you-with-magniber-ransomware/).Unlike the larger ransomware operations, Magniber has primarily targeted individual users who download malicious software and execute it on their home or small business systems.In 2018, AhnLab [released a decryptor](https://www.bleepingcomputer.com/news/security/decrypters-for-some-versions-of-magniber-ransomware-released/) for the Magniber ransomware. However, it no longer works as the threat actors fixed the bug allowing free file decryption.Ongoing Magniber campaign————————-Since July 20, BleepingComputer has seen a surge in Magniber ransomware victims [seeking help in our forums](https://www.bleepingcomputer.com/forums/t/771427/magniber-2022-2024-ransomware-random-5-9-character-ext-support-topic/?p=5387149).Ransomware identification site ID-Ransomware has also seen a surge, with almost 720 submissions to the site since July 20, 2024.While it unclear how victims are being infected, BleepingComputer has been told by a few victims that their device was encrypted after running software cracks or key generators, which is a method the threat actors used in the past.Once launched, the ransomware encrypts files on the device and appends a random 5-9 character extension, like .oaxysw or .oymtk, to encrypted file names.The ransomware will also create a ransom note named READ_ME.htm, which contains information about what happened to a person’s files and a unique URL to the threat actor’s Tor ransom site. 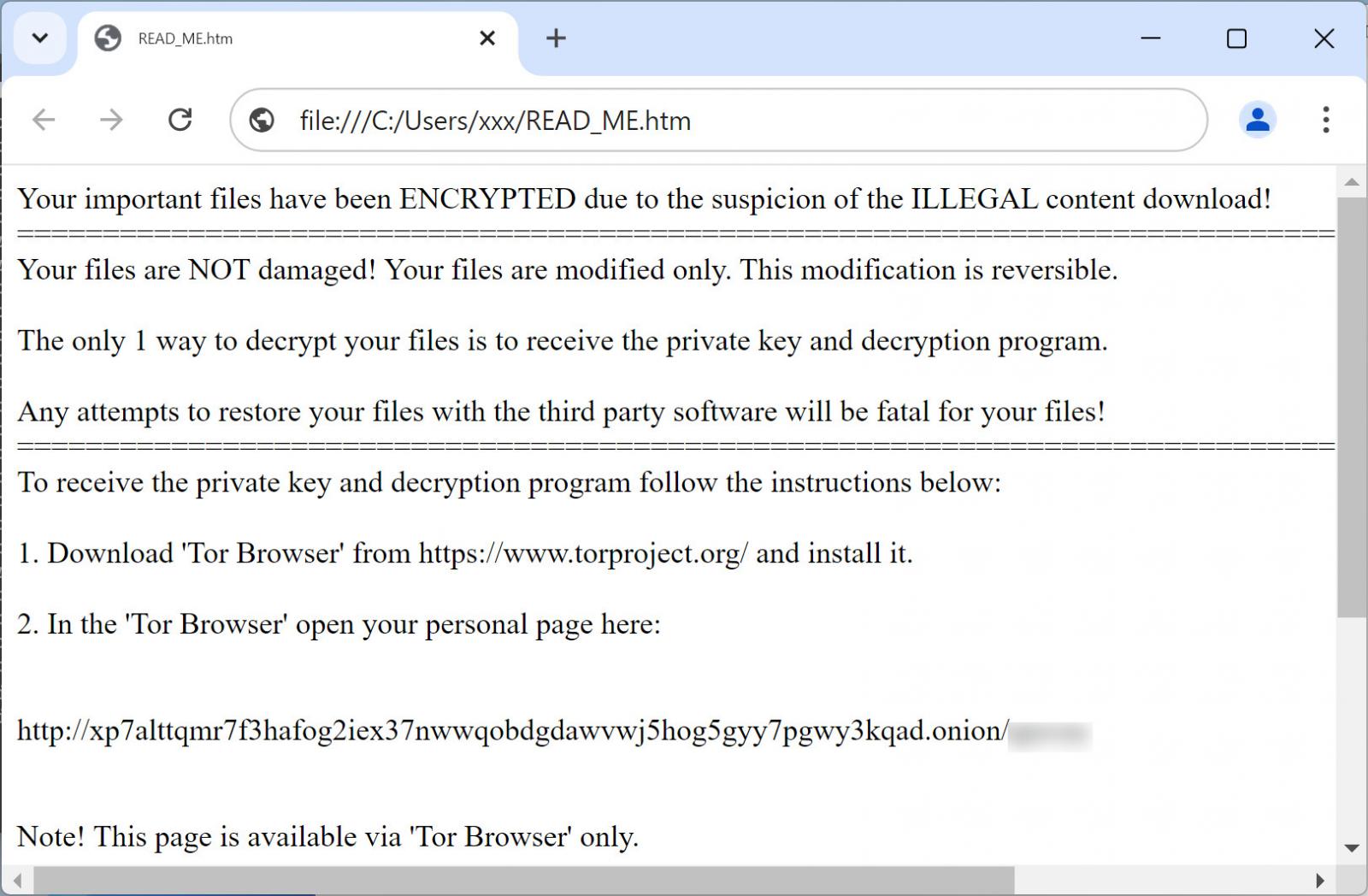 **Magniber ransom note** *Source: BleepingComputer*As Magniber typically targets consumers, the ransom demands start at $1,000 and then increase to $5,000 if a Bitcoin payment is not made within three days. 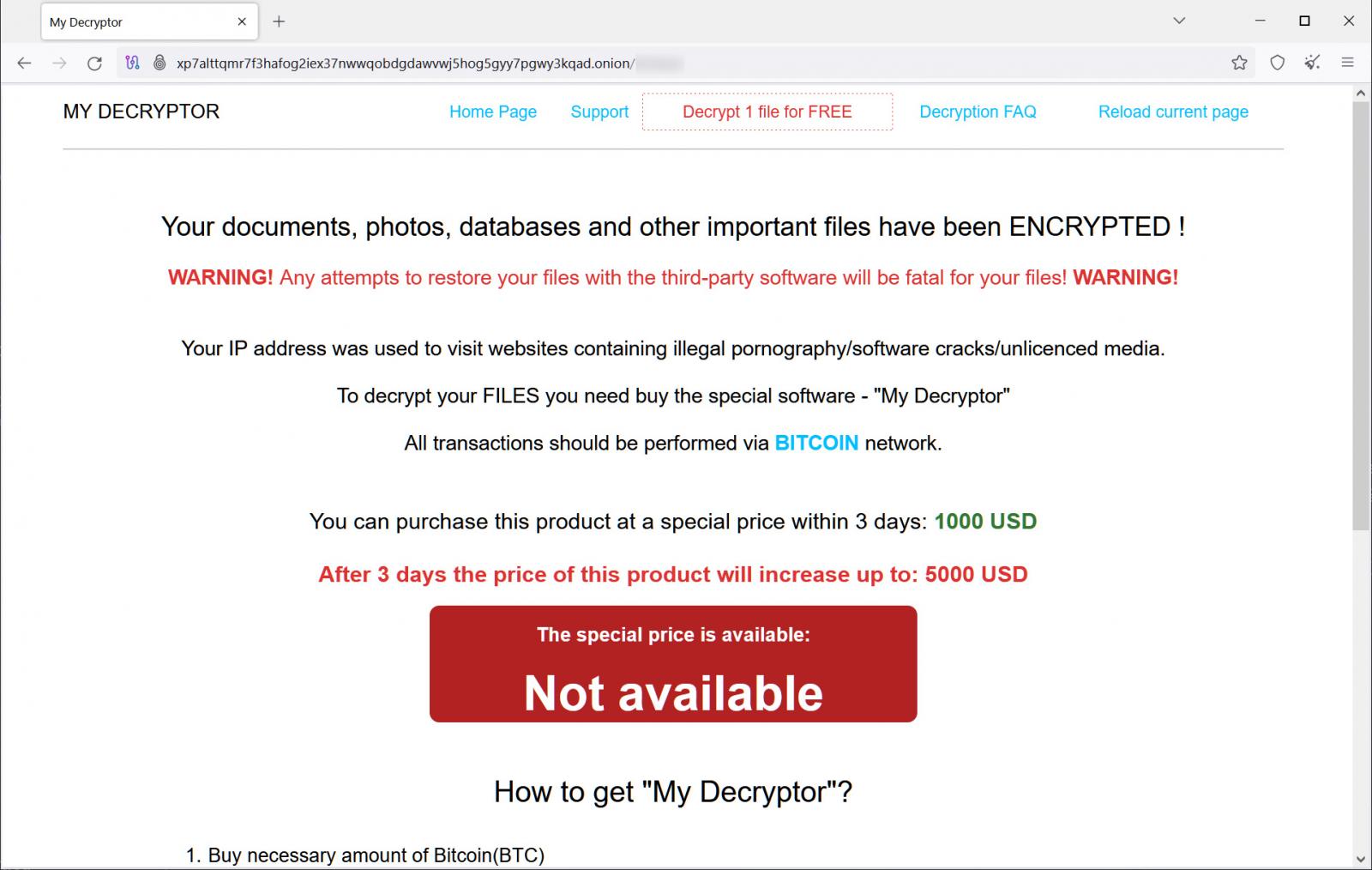 **Magniber payment site** *Source: BleepingComputer*Unfortunately, there is no way to decrypt files encrypted by the current versions of Magniber for free.
It is strongly advised to avoid software cracks and key generators as it’s not only illegal but also a common method used to distribute malware and ransomware.For those impacted by the ransomware, you can use our dedicated [Magniber support topic](https://www.bleepingcomputer.com/forums/t/771427/magniber-2022-2024-ransomware-random-5-9-character-ext-support-topic/) to receive help or receive answers to questions. ### Related Articles:[OneBlood’s virtual machines encrypted in ransomware attack](https://www.bleepingcomputer.com/news/security/onebloods-virtual-machines-encrypted-in-ransomware-attack/)[Dark Angels ransomware receives record-breaking $75 million ransom](https://www.bleepingcomputer.com/news/security/dark-angels-ransomware-receives-record-breaking-75-million-ransom/)[CISA warns of VMware ESXi bug exploited in ransomware attacks](https://www.bleepingcomputer.com/news/security/cisa-warns-of-vmware-esxi-bug-exploited-in-ransomware-attacks/)[Black Basta ransomware switches to more evasive custom malware](https://www.bleepingcomputer.com/news/security/black-basta-ransomware-switches-to-more-evasive-custom-malware/)[Columbus investigates whether data was stolen in ransomware attack](https://www.bleepingcomputer.com/news/security/columbus-investigates-whether-data-was-stolen-in-ransomware-attack/)
Related Tags:
NAICS: 923 – Administration Of Human Resource Programs
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 62 – Health Care And Social Assistance
NAICS: 336 – Transportation Equipment Manufacturing
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 622 – Hospitals
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 92 – Public Administration
Associated Indicators:


