
Author: Tekno Phreak
-
Longtime Tenable CEO, NetWitness Head Amit Yoran Dies at 54
[Governance -& Risk Management](https://www.govinfosecurity.com/governance-risk-management-c-93) , [IT Risk Management](https://www.govinfosecurity.com/risk-management-c-431) , [Vulnerability Assessment -& Penetration Testing (VA/PT)](https://www.govinfosecurity.com/vulnerability-assessment-penetration-testing-vapt-c-433)Longtime Tenable CEO, NetWitness Head Amit…
-
New FireScam Android data-theft malware poses as Telegram Premium app
A new Android malware named ‘FireScam’ is being distributed as a premium version of the Telegram app via phishing websites…
-
Google Chrome is making it easier to share specific parts of long PDFs
Google is adding the Text Fragment feature to its PDF reader to make it easier to share specific parts of…
-
Nuclei flaw lets malicious templates bypass signature verification
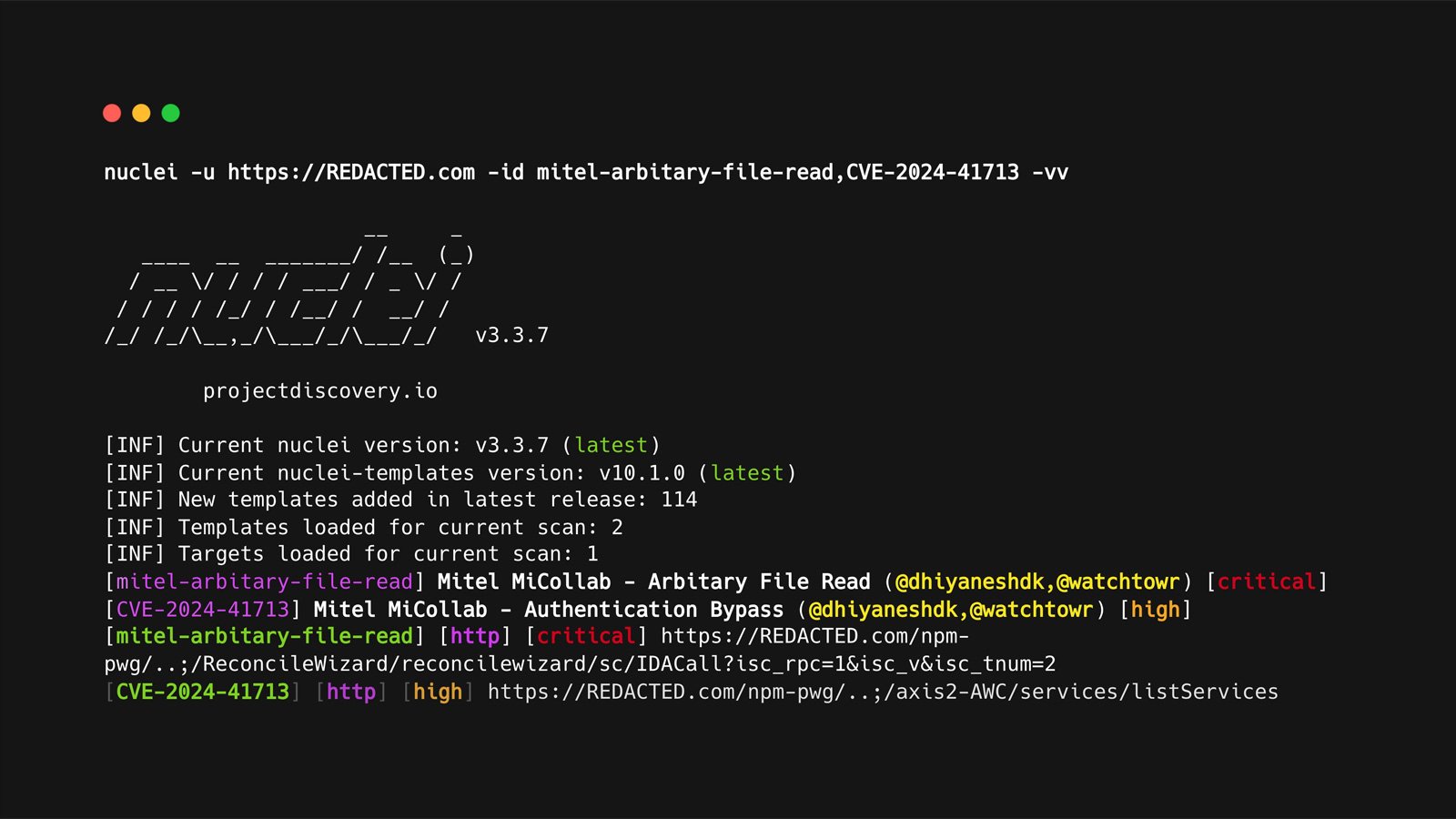A now-fixed vulnerability in the open-source vulnerability scanner Nuclei could potentially allow attackers to bypass signature verification while sneaking malicious…
-
US Treasury Department sanctioned Chinese cybersecurity firm linked to Flax Typhoon APT
The U.S. Treasury Department sanctioned Chinese cybersecurity firm Integrity Tech for its involvement in attacks attributed to the Flax Typhoon…
-
Malicious npm packages target Ethereum developers
Malicious npm packages target Ethereum developers, impersonating Hardhat plugins to steal private keys and sensitive data.————————————————————————————————————————–[Hardhat](https://hardhat.org/), by the [Nomic Foundation](https://nomic.foundation/),…
-
2025-01-04: Four days of scans and probes and web traffic hitting my web server
2025-01-04 (SATURDAY): FOUR DAYS OF SCANS AND PROBES AND WEB TRAFFIC HITTING MY WEB SERVER——————————————————————————————NOTES:* Zip files are password-protected. Of…
-
Beware of phishing attacks by APTC01 (Poison Ivy)
APT-C-01, known as Poison Ivy, is a persistent threat group targeting defense, government, technology, and education sectors since 2007. They…
-
Memory-Based Attacks: How Fileless Malware Operates Without Leaving A Trace
Threat actors are always developing new and more effective approaches to system breaches in the perpetually shifting field of cybersecurity.From…
-
Hacked on Christmas, DEphoto starts notifying customers, only to be attacked again
The threat actor known as 0mid16B contacted DataBreaches this morning to alert this site to a breach involving a U.K.…

