Researchers explore the [vulnerability](https://cybersecuritynews.com/vulnerability-management-tools/) of air-gapped networks to malicious attacks. Despite their physical isolation, these networks can be compromised through covert channels, such as electromagnetic emissions.The attack model involves malware manipulating RAM to generate radio signals that can be encoded with sensitive information and exfiltrated from a distance. It presents the design and implementation of a transmitter and receiver capable of transmitting and receiving these signals.Experimental results demonstrate the feasibility of the attack, highlighting the need for robust countermeasures to protect air-gapped networks from such[threats.](https://cybersecuritynews.com/cyber-threat-intelligence/) 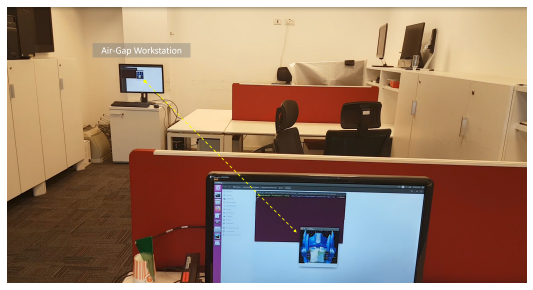 Attack demonstrationThe study presents a novel covert channel based on electromagnetic emissions from the RAM bus. The transmitter modulates [memory](https://cybersecuritynews.com/decoded-peaklight-memory-malware/)access patterns to encode data, which is then demodulated by the receiver.Utilizing Manchester encoding for faster transmission ensures clock synchronization and error detection, which increases bandwidth requirements.The transmitter employs the MOVNTI instruction to maintain RAM bus activity and uses a preamble sequence for synchronization. The demodulator frames the received data based on an alternating bit sequence.A comparison between Manchester encoding and OOK modulation concluded that Manchester encoding is more suitable for this covert channel due to its synchronization and error detection benefits.**`Are You From SOC/DFIR Teams? – Try Advanced Malware and Phishing Analysis With ANY.RUN – `[14 day free trial](https://app.any.run/?utm_source=csn_sep&utm_medium=article&utm_campaign=modern-malware-discord-telegram&utm_content=register&utm_term=050924#register)**  . Ettus B210 Universal Software Radio Peripheral (USRP)The evaluation of the RAMBO covert channel demonstrates its effectiveness in exfiltrating data through [electromagnetic emissions](https://cybersecuritynews.com/hdmi-cables-steal-passwords/) from DDR RAM. Despite varying distances and bit rates, the channel maintained a high signal-to-noise ratio and low bit error rates.Low SNR levels limited high-speed transmissions. Faraday shielding and virtualization were shown to be effective countermeasures, but they are not widely deployable.The DDR RAM clock frequency influences the covert channel’s frequency range and can be affected by spread spectrum clocking. Overall, the RAMBO covert channel presents a significant security risk, requiring careful consideration of countermeasures. 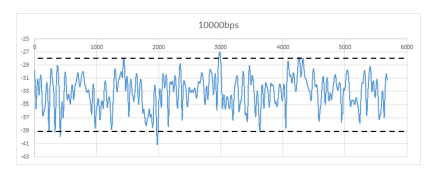 The transmission with 10000 bps.Several countermeasures can be employed to mitigate the RAMBO attack. Physical separation using zone restrictions and Faraday enclosures can prevent information leakage.Host-based intrusion detection systems and hypervisor-level monitoring can detect suspicious memory access patterns. External spectrum analyzers and radio jammers can identify and disrupt covert radio transmissions.Internal memory jamming can interfere with the covert channel and may also impact legitimate operations. While these countermeasures offer varying levels of protection, a combination of approaches is often necessary to effectively defend against the RAMBO attack.The [paper](https://arxiv.org/pdf/2409.02292) demonstrated a novel air gap covert channel attack that exploits memory operations in isolated computers to exfiltrate sensitive data. By manipulating memory-related instructions, attackers can encode and modulate information on electromagnetic waves emitted from the memory buses.A nearby receiver equipped with a software-defined radio can then intercept, demodulate, and decode the transmitted data, which enables attackers to leak various types of information, including keystrokes, files, images, and biometric data, at a rate of hundreds of bits per second.**`What Does MITRE ATT&CK Expose About Your Enterprise Security? – `[Watch Free Webinar!](https://go.cynet.com/what-does-mitre-expose?utm_source=cyber_security_news&utm_medium=sponsored_article&utm_campaign=Q3-sponsored-content&utm_content=gamechanger)**The post [RAMBO Attack Steals Data From Air-gapped Systems](https://cybersecuritynews.com/rambo-attack-air-gapped-systems/) appeared first on [Cyber Security News](https://cybersecuritynews.com).
Related Tags:
NAICS: 335 – Electrical Equipment
Appliance
Component Manufacturing
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 92 – Public Administration
NAICS: 339 – Miscellaneous Manufacturing
NAICS: 922 – Justice
Public Order
Safety Activities
NAICS: 33 – Manufacturing – Metal
Electronics And Other
Blog: Cybersecurity News
Phishing
Associated Indicators:


