report  Download / Print article PDF ##### ShareCopied to clipboard ##### Share##### Facebook##### Linkedin##### X##### Copy LinkCopied to clipboard ##### Share##### Facebook##### Linkedin##### X##### Copy LinkThe threat from commercial cyber proliferation==============================================Report informing readers about the threat to UK industry and society from commercial cyber tools and services. Invalid DateTime  ##### In this report1. [NCSC Assessment](#section_1)2. [How likely is a ‘realistic possibility’?](#section_2)3. [Key judgements](#section_3)4. [What is the commercial cyber proliferation threat?](#section_4)5. [SPYWARE: Hacking-as-a-Service companies](#section_5)6. [BESPOKE SERVICES: Hackers-for-hire](#section_6)7. [THE COMMERCIAL ZERO-DAY EXPLOIT MARKETPLACE](#section_7)8. [COMMODITISATION OF TOOLS](#section_8)9. [Looking ahead](#section_9)10. [Glossary](#section_10)### UK Cyber Policy commentThe UK’s [National Cyber Strategy](https://www.gov.uk/government/publications/national-cyber-strategy-2022/national-cyber-security-strategy-2022) commits us to being a ‘leading responsible and democratic cyber power, able to protect and promote our interests in and through cyberspace in support of national goals’. As such, tackling commercial cyber proliferation and ensuring all cyber capabilities are developed, sold and used in a way that is legal, responsible and proportionate is a policy priority for the UK.At the Summit for Democracy on 29-30 March the UK committed to a number of initiatives to reaffirm our support for a free, open, peaceful and secure cyberspace and to encourage responsible cyber behaviour by others, including [a Joint Statement on Efforts to Counter the Proliferation and Misuse of Commercial Spyware](https://www.gov.uk/government/news/efforts-to-counter-the-proliferation-and-misuse-of-commercial-spyware-joint-statement). Any policy response must address all areas of this market, and industry and civil society participation is essential. This is an international problem that requires an international solution, and the UK intends to work closely with partners to ensure the future development, sale and use of commercial cyber capabilities contributes to a cyberspace that is safe and prosperous for everyone. *** ** * ** ***NCSC Assessment—————NCSC Assessment (NCSC-A) is the authoritative voice on cyber threat to the UK. We fuse all-source information — classified intelligence, industry knowledge, academic material and open source — to provide independent key judgements that inform policy decision making and improve UK cyber security. We work closely with government, industry and international partners for expert input into our assessments.NCSC-A is part of the Professional Heads of Intelligence Assessment (PHIA). PHIA leads the development of the profession through analytical tradecraft, professional standards, and building and sustaining a cross-government community.This report was produced for CYBERUK 2023 and uses formal probabilistic language (see yardstick) from NCSC-A product to inform readers about the threat to UK industry and society from commercial cyber tools and services. *** ** * ** ***How likely is a ‘realistic possibility’?—————————————-### Professional Head of Intelligence Assesment (PHIA) Probability YardstickNCSC Assessment uses the PHIA probability yardstick every time we make an assessment, judgement, or prediction. The terms used correspond to the likelihood ranges below.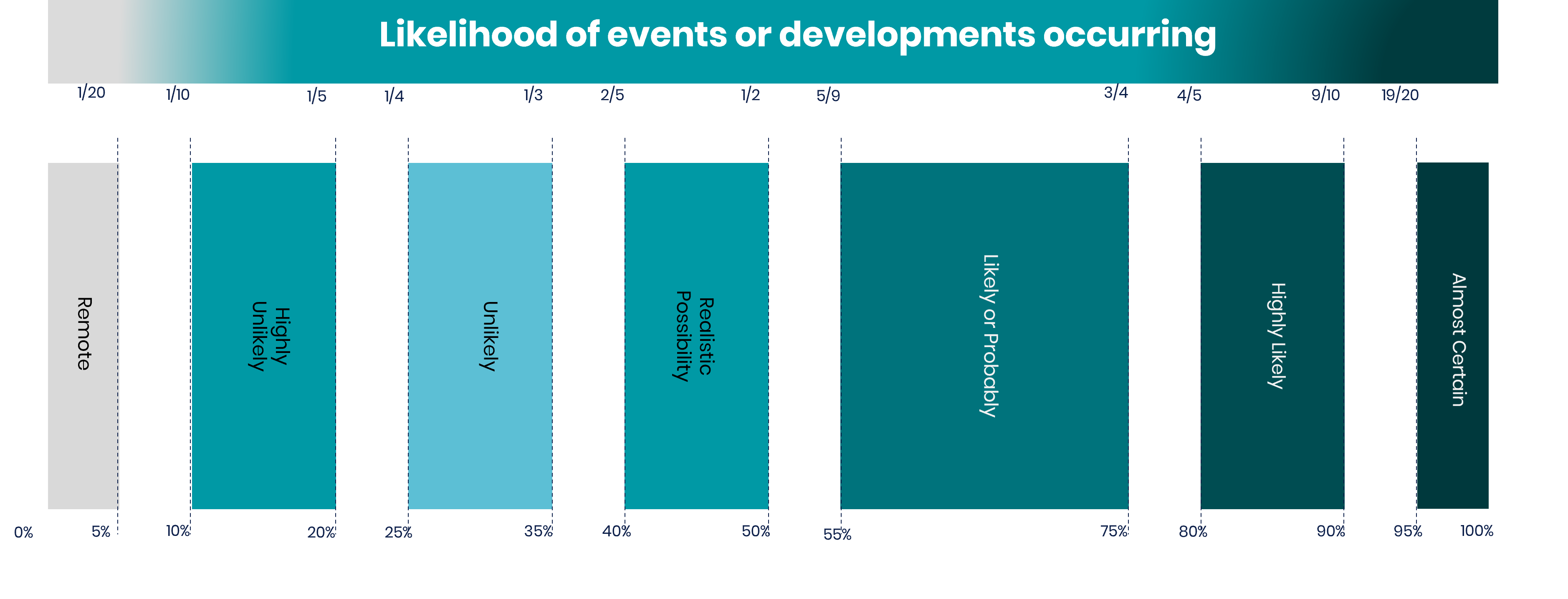 *** ** * ** ***Key judgements————–1.  Commercial cyber tools and services lower the barrier to entry to state and non-state actors in obtaining cost-effective capability and intelligence they would not otherwise be able to develop or acquire themselves. This commercial proliferation will almost certainly be transformational on the cyber landscape.2.  The sophistication of some commercial intrusion cyber products and services can almost certainly rival the equivalent capabilities of some state-linked Advanced Persistent Threat (APT) groups.3.  Commercial spyware has been almost certainly used by some states in the targeting of journalists, human rights activists, political dissidents and opponents and foreign government officials at scale.4.  Commercial ‘hackers-for-hire’ pose a potential corporate espionage threat against organisations and individuals with privileged or valuable confidential information, across multiple sectors.5.  Hackers-for-hire raise the likelihood of unpredictable targeting or unintentional escalation through attempts to compromise a wider range of targets.6.  The proliferation of commercial cyber capability will result in an expanding number of elements for cyber defence to detect and mitigate , and a similarly expanding number and type of victims. *** ** * ** ***What is the commercial cyber proliferation threat?————————————————–The commercial proliferation of cyber tools and services **lowers the barrier to entry to state and non-state actors in obtaining capability and intelligence** that they would not otherwise be able to develop or acquire.The **sophistication of some commercial intrusion cyber products and services can almost certainly rival the equivalent capabilities of some state-linked Advanced Persistent Threat (APT) groups.** The bulk of the commercial cyber sector is highly likely focused on satisfying domestic state demand from law enforcement and government agencies. However, over the last decade, a growing number of enterprises have emerged offering a range of products and services to global customers. They include off-the-shelf capability (Hacking-as-a-Service), bespoke hacking services (hackers-for-hire), and the sale of enabling capabilities such as zero-day exploits and tool frameworks. *** ** * ** ***SPYWARE: Hacking-as-a-Service companies—————————————Over the last ten years, at least 80 countries have purchased commercial cyber intrusion software, or spyware. For dozens of states without a skills base, **the commercial sector is almost certainly transformational**, allowing cost-effective access to capability that would otherwise take decades to develop.While products vary in capability and application, commercially available spyware for mobile devices can offer the ability to read messages, listen to audio calls, obtain photos, locate the device and remotely operate the camera and microphone. Some states are likely to procure multiple commercial cyber tools to meet their requirements. Devices can be compromised in a number of ways, including phishing, but also ‘zero-click’ attacks which do not require user interaction, making it more difficult for victims to mitigate.While these tools have been used by states against law enforcement targets, **spyware has almost certainly been used by some states in the targeting of journalists, human rights activists, political dissidents and opponents and foreign government officials.** This is almost certainly happening at scale, with thousands of individuals targeted each year. While current products focus on mobile devices and intelligence gathering, as the sector grows and demand increases, products and services will likely diversify to meet demand. *** ** * ** ***BESPOKE SERVICES: Hackers-for-hire———————————-Hacker-for-hire groups carry out cyber activity for paying clients. As well as providing information of traditional espionage value to states, hackers-for-hire are also reportedly used for legal disputes, intellectual property theft, insider trading, and the theft of other private data. Hackers-for-hire differ in skill and capability, ranging from low-level cyber crime activity to technically complex and effective network compromises that may go undetected. Some groups operate in criminal circles, some portray themselves as commercial companies, and others operate anonymously. Hacker-for-hire groups that focus on stealing information use phishing and other social engineering attacks, exploits against publicly reported vulnerabilities in computer networks, and sometimes zero-day attacks to compromise victims. The greatest threat comes from higher-end, hacker-for-hire groups, whose abilities and impact are similar to those of capable state actors. **Hackers-for-hire pose a potential corporate espionage threat against organisations and individuals with privileged or valuable confidential information in multiple sectors.**While less-skilled and cyber criminal hackers-for-hire almost certainly carry out Denial of Service (DoS) attacks for a fee to temporarily disrupt a target website or server on a customer’s behalf, additional law enforcement attention probably deters higher skilled hackers-for-hire from conducting destructive or disruptive operations. However, a growing market and the extra financial incentive raise the likelihood of hackers-for-hire accepting this type of tasking over the next five years. **Hackers-for-hire also raise the likelihood of unpredictable targeting or unintentional escalation through attempts to compromise a wider range of targets** , particularly those seeking valuable information to sell on, as opposed to ‘working to order’. It is likely that potentially significant financial rewards incentivise state employees or contractors with cyber skills to become hackers-for-hire, risking the proliferation of cyber techniques from state to non-state actors. *** ** * ** ***THE COMMERCIAL ZERO-DAY EXPLOIT MARKETPLACE——————————————-Historically, underground criminal markets have facilitated the exploit trade. Since the early 2000s, a lucrative market for zero-day exploits has emerged in the commercial space. The large sums of money involved for critical zero-day exploits for commonly used systems and processes mean opportunities for profit are significant and have driven commercialisation.Critical zero-day exploits and vulnerabilities are almost certainly transformational to actors with the skills to make use of them. **States, or commercial cyber intrusion companies providing products to states, are the dominant customers of the commercial zero-day market and are highly likely to remain so for the next five years**. The growth of the commercial sector facilitating this trade has likely increased the number of states able to access critical zero-day capability, directly or indirectly.Some well-funded cyber crime groups have highly likely purchased lower priced zero-day exploits for less well-used systems from underground exploit marketplaces. However, purchasing high-cost, critical zero-day capability from the commercial marketplace is unlikely to appeal to most cyber crime groups. Financial motivation makes it more likely that they prioritise lower-cost exploits developed from disclosed zero-day vulnerabilities, albeit as early as possible after disclosure to maximise the number of unpatched systems they can target. *** ** * ** ***COMMODITISATION OF TOOLS————————Customisable tool frameworks are developed by cyber security software developers to emulate threat activity to enable penetration testing of networks. They are usually sold under licence, but some are also publicly available or available in versions where the licence has been removed. These frameworks are being used or repurposed by state and non-state actors; highly likely enabling a cost-effective uplift in cyber capability. It is highly likely that their constant evolution and **the ability of actors to customise and repurpose these frameworks means widespread misuse of these frameworks will almost certainly continue** over the next five years.State and non-state actors also have access to capability developed and sold for cyber crime. In recent years, cyber crime marketplaces have grown and become increasingly professionalised, in part driven by demand from ransomware actors. One example is Malware-as-a-Service (MaaS), which is a service that provides use of malware, eliminating the need to create and develop the software as well as reducing the knowledge threshold required to operate the malware. Offering these services as a package is attractive to less skilled cyber criminals and as such has almost certainly expanded the number of victims. *** ** * ** ***Looking ahead————-Over the next five years: * Increased demand, coupled with a permissive operating environment, will almost certainly result in an expansion of the global commercial cyber intrusion sector, driving an increased threat to a wide range of sectors.* It is almost certain there will be further high-profile exposures of victims against whom commercial cyber tools or hack er-for-hire operations have been deployed.* Oversight of the commercial intrusion cyber sector will almost certainly lack international consensus, be difficult to enforce and subject to political and commercial influence.* However, it is likely that many commercial cyber companies will be incentivised to vet and limit their customer bases, should effective oversight and international norms on development and sale of commercial cyber capability emerge. *** ** * ** ***Glossary——–Show all ### Cyber proliferationShow **Cyber proliferation** refers to the intentional or unintentional transfer of cyber capabilities between actors for network or device exploitation or attack purposes. ### Cyber intrusion companiesShow **Cyber intrusion companies** refer to any commercial company that offers products or services for network or device exploitation or attack, rather than cyber security purposes. These might include sellers of vulnerabilities and exploits, companies developing and selling cyber surveillance products or companies offering hacker -for-hire services. ### Hacking-as-a-Service companiesShow **Hacking-as-a-Service companies** describes the provision of ‘off-the-shelf’ cyber intrusion products such as mobile spyware, and supporting services, by a commercial entity, usually to nation state law enforcement and intelligence services. The customers usually manage the victim targeting and resulting intelligence; the commercial entity provides the capability and often the supporting infrastructure as a service under a licence. ### Hackers-for-hireShow **Hackers-for-hire** are unaffiliated individuals or groups of actors that are hired by states, entities or even individuals to conduct cyber operations to meet customer requirements. They use their own tools and techniques and are aware of, and in some cases may select, who they are targeting. ### Commercial Tool FrameworksShow **Commercial Tool Frameworks** (also known as Offensive Security Tools) are developed in the cyber security sector to provide customisable tool frameworks to facilitate and manage the intrusion of client networks to aid penetration testing of systems. ### VulnerabilityShow A **vulnerability** is a weakness, or flaw, in a system or process. An attacker may seek to exploit a vulnerability to gain access to a system. The code developed to do this is known as an **exploit** . A **zero-day** exploit exploits a vulnerability where there are no security fixes yet available. A zero-day vulnerability becomes an**n-day** vulnerability once a security fix (patch) has been issued by the vendor. Exploitation of an n-day vulnerability relies on finding systems that have not been updated. ### MalwareShow **Malware** is derived from ‘malicious software’, and includes viruses, trojans, worms or any code or content used for illicit purposes against computer systems, networks or devices. Topics——[Cyber threat](https://www.ncsc.gov.uk/section/advice-guidance/all-topics?topics=Cyber threat)[Vulnerabilities](https://www.ncsc.gov.uk/section/advice-guidance/all-topics?topics=Vulnerabilities)|  | Back to top |  | Download / Print article PDF || ##### Share|| Copied to clipboard || ##### Share|| || ##### Facebook|| || ##### Linkedin|| || ##### X|| || ##### Copy Link|| Copied to clipboard || ##### Share|| || ##### Facebook|| || ##### Linkedin|| || ##### X|| || ##### Copy Link|| * || ##### Published|| * 19 April 2023| *|| ##### Written For|| * [Cyber security professionals](/section/advice-guidance/cyber-security-professionals)| * [Large organisations](/section/advice-guidance/large-organisations)| * [Public sector](/section/advice-guidance/public-sector)| * [Small -& medium sized organisations](/section/advice-guidance/small-medium-sized-organisations)| * || ##### Published|| * 19 April 2023| *|| ##### Written For|| * [Cyber security professionals](/section/advice-guidance/cyber-security-professionals)| * [Large organisations](/section/advice-guidance/large-organisations)| * [Public sector](/section/advice-guidance/public-sector)* [Small -& medium sized organisations](/section/advice-guidance/small-medium-sized-organisations)  Back to top
Related Tags:
NAICS: 923 – Administration Of Human Resource Programs
NAICS: 92 – Public Administration
NAICS: 926 – Administration Of Economic Programs
NAICS: 928 – National Security And International Affairs
NAICS: 924 – Administration Of Environmental Quality Programs
Blog: NCSC Reports
Guidance and Blog-post
Phishing
Software Discovery: Security Software Discovery
Software Discovery
Associated Indicators:


