guidance  Download / Print article PDF ##### ShareCopied to clipboard ##### Share##### Facebook##### Linkedin##### X##### Copy LinkCopied to clipboard ##### Share##### Facebook##### Linkedin##### X##### Copy LinkTakedown: removing malicious content to protect your brand==========================================================How to protect your brand from being exploited online. Invalid DateTime  ##### in this guidance1. [What is the risk?](#section_1)2. [What is ‘takedown?](#section_2)3. [What can you do right now?](#section_3)4. [Using a takedown provider](#section_4)5. [Some questions to ask your organisation](#section_5)As a brand owner, whether for a small business or a large multinational organisation, you will want to do as much as possible to protect it. This guidance introduces some methods you can use to protect your online brand, and by extension, your customers or users. ### Note:This guidance does not cover takedowns related to copyright infringement (such as Digital Millennium Copyright Act under US law). *** ** * ** ***What is the risk?—————–If you own or manage a brand there is a risk that your brand could be exploited online. This can include false representations of your products or services, fake endorsements, and using your brand in [phishing](/guidance/phishing) or malware to make fake campaigns look (and sound) credible.The better-known your brand is, the more likely someone will try to exploit it. This misuse can appear across many platforms including online adverts, social media accounts, email, SMS and phone calls.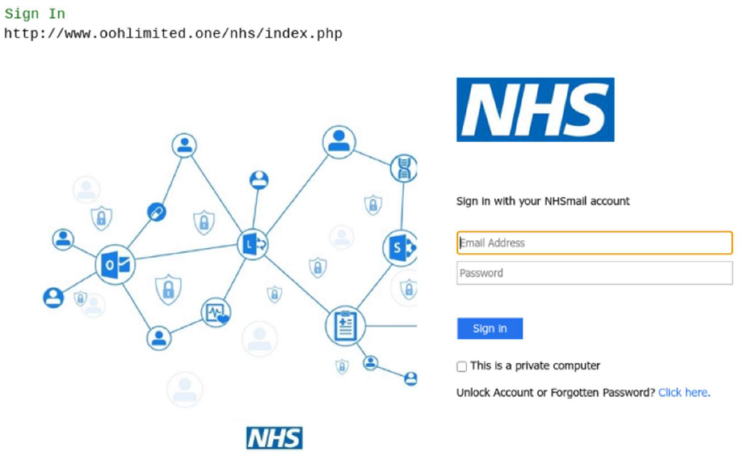*Fig 1: Example of a phishing website that cloned NHSmail to steal NHS credentials* *** ** * ** ***What is ‘takedown?——————In this context, **takedown** is the removal of malicious content such as phishing sites. This is achieved by issuing a notification to the hoster of the malicious content, or in the case of a phishing domain (that is, where a registered domain has been set up to enable fraud), contacting a domain registrar to request its suspension.If the request for removal is accepted, the recipient will remove it from the internet. In the majority of cases, a takedown notification does **not** rely on legal compulsion, as it merely flags pertinent information or provides evidence of an issue that may breach the terms and conditions of the hosting platform. *** ** * ** ***What can you do right now?————————–Anyone can contact hosting companies and domain registrars if their services are being abused, requesting that the service be withdrawn by removing either the domain name or the web hosting service.All reputable registrars and hosting companies have terms and conditions that forbid sending phishing emails or distributing malware. If you can prove that one of their customers has done this, then the hosting company/registrar will remove the service. In some cases, they may need to check if the website that’s in breach of conditions was itself hacked, for example to deliver the malware.If you want to contact a hosting company or domain registrar, you should:1. Identify the domain name registrar for the domain. Use the search term ‘**online whois**’ to find tools that can help with this.2. Once you have identified the registrar for the domain, search for the name of the registrar and the word ‘**abuse**’ to find out how to report abuse.3. Identify the IP address of the website or service. Use the search term ‘**website to ip**’ to find tools that can help with this.4. Use the search term ‘**ip whois online**’ and use a tool to identify who owns the IP address that is being exploited.5. Either use the abuse contact information in the data returned in step 4, or search for the IP owner organisation and the word ‘**abuse**’.In order to support your case you should ensure that you have evidence such as:* phishing forms: a screenshot which shows the content and the full location (URL) of the page, along with a record of when you took the screenshot (as shown in *fig 1* above)* phishing emails purporting to be from you or representing your brand; ensure it’s a complete copy of the mail, including all email headers which will show originating IP addressesTakedown requests could take anything between hours to days or even weeks. Some less reputable suppliers may simply ignore requests. *** ** * ** ***Using a takedown provider————————-Alternatively, you can use a takedown provider who has experience dealing with hosters/registrars and carries out many of the above services on your behalf. When choosing a provider, there are several factors to take into consideration to ensure you receive the service that is right for you. Price should **not** be the only deciding factor. You should also consider:* How do they manage takedown requests?* Do they have established relationships with hosting providers and registrars around the world?* Do they have a track record? Have they published any customer testimonials?* How do they discover attacks (other than ones reported by you the brand owner)? This helps to understand how they are monitoring online platforms to look for examples of abuse proactively instead of responding reactively.* How easy is it to report attacks to them? Where do they look? What sources of data do they use?* How quickly do they process a reported attack, validate it and send notifications?* What outcomes can you expect from them? What are the average or median times for takedown with their service? Can the service scale if required?* Is it possible to review statistics and outcomes relating to the takedowns?* What is their specialisation? For example, some providers may specialise in social media, advertising analysis, phishing, or malware. Or do they claim to do all of it?* Beyond the scope of content removal, what other mitigations do they offer? Blocking or other additional countermeasures?* Many takedown notifications are not legally compelling. Does the provider provide legal compulsion in any of their takedown categories, if required?* Do you need a more robust legal response? Does your takedown provider provide notifications with legal compulsion? *** ** * ** ***Some questions to ask your organisation—————————————The NCSC recommend that you plan if/when to engage with a takedown provider before there’s an incident. This will include knowing who to contact, and will allow you to deal with other firefighting activities around protecting your brand. You should establish:* What is the potential business impact if nothing is done (for example loss of revenue, or reputational damage).* What level of risk are you willing to accept?* Do you know the scale of the problem?* Do you have an abuse channel/mechanism to receive reports from customers or the public? A simple example could be a page on your website including contact details to receive reports so you can review them or where you can publish an ‘abuse@’ address. What do you currently do with these reports? Could you forward them to your takedown provider?* Do you encourage forwarding of emails from users and screenshots of suspicious activities.
Finally, if you’re managing a UK government service or brand, you should know that the NCSC runs [a takedown service for HMG](/information/takedown-service). URLs associated with HMG-themed phishing attacks, which are often targeted at UK based users, are removed. Topics——[Authentication](https://www.ncsc.gov.uk/section/advice-guidance/all-topics?topics=Authentication)[Mitigation](https://www.ncsc.gov.uk/section/advice-guidance/all-topics?topics=Mitigation)[Phishing](https://www.ncsc.gov.uk/section/advice-guidance/all-topics?topics=Phishing)|  | Back to top |  | Download / Print article PDF || ##### Share|| Copied to clipboard || ##### Share|| || ##### Facebook|| || ##### Linkedin|| || ##### X|| || ##### Copy Link|| Copied to clipboard || ##### Share|| || ##### Facebook|| || ##### Linkedin|| || ##### X|| || ##### Copy Link|| * || ##### Published|| * 21 September 2022| *|| ##### Reviewed|| * 21 September 2022| *|| ##### Version|| * 1.0| *|| ##### Written For|| * [Cyber security professionals](/section/advice-guidance/cyber-security-professionals)| * [Large organisations](/section/advice-guidance/large-organisations)| * [Public sector](/section/advice-guidance/public-sector)| * || ##### Published|| * 21 September 2022| *|| ##### Reviewed|| * 21 September 2022| *|| ##### Version|| * 1.0| *|| ##### Written For|| * [Cyber security professionals](/section/advice-guidance/cyber-security-professionals)| * [Large organisations](/section/advice-guidance/large-organisations)* [Public sector](/section/advice-guidance/public-sector)  Back to top
Related Tags:
NAICS: 92 – Public Administration
NAICS: 922 – Justice
Public Order
Safety Activities
Blog: NCSC Reports
Guidance and Blog-post
Phishing
Impair Defenses: Disable or Modify Tools
Impair Defenses
Software Discovery: Security Software Discovery
Software Discovery
System Time Discovery
Associated Indicators:


