 [Tara Seals](/author/tara-seals), Managing Editor, NewsJune 6, 2025 7 Min Read  Source: ACORN 1 via Alamy Stock Photo [](https://www.linkedin.com/sharing/share-offsite/?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](http://www.facebook.com/sharer/sharer.php?u=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](http://www.twitter.com/intent/tweet?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](https://www.reddit.com/submit?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing&title=Cutting-Edge%20ClickFix%20Tactics%20Snowball%2C%20Pushing%20Phishing%20Forward)[](mailto:?subject=Cutting-Edge ClickFix Tactics Snowball, Pushing Phishing Forward&body=I%20thought%20the%20following%20from%20Dark%20Reading%20might%20interest%20you.%0D%0A%0D%0A%20Cutting-Edge%20ClickFix%20Tactics%20Snowball%2C%20Pushing%20Phishing%20Forward%0D%0Ahttps%3A%2F%2Fwww.darkreading.com%2Fremote-workforce%2Fcutting-edge-clickfix-snowball-phishing) ClickFix campaigns are gaining steam according to various security researchers, with recent campaigns spotted across the globe from a wide swath of cyberattackers. The increasingly popular tactic represents a significant new evolution for social engineering, researchers say — and enterprises need to take note.ClickFix activity has been snowballing: [Darktrace said](https://www.darktrace.com/blog/unpacking-clickfix-darktraces-detection-of-a-prolific-social-engineering-tactic) yesterday that it recently identified multiple ClickFix attacks across customer environments in Europe, the Middle East, and Africa (EMEA), and in the United States; while SlashNext, in a separate [report](https://slashnext.com/blog/decoding-clickfix-lessons-from-the-latest-browser-based-phish/), detailed an unusual version of the attack vector that impersonates Cloudflare Turnstile, which is the Web protection company’s CAPTCHA-like Turing test. Also this week, Cofense [outlined](https://cofense.com/blog/clickfix-campaign-spoofs-booking-com-for-malware-delivery) a campaign that spoofed Booking.com CAPTCHAs, targeting hotel chains with remote access Trojans (RATs) and infostealers. ClickFix first came to light as an attack method last year when Proofpoint researchers observed [compromised websites serving overlay error messages to visitors](https://www.darkreading.com/remote-workforce/cut-paste-tactics-import-malware). The message claimed that a faulty browser update was causing problems, and asked the victim to open ‘Windows PowerShell (Admin)’ (which will open a User Account Control (UAC) prompt) and then right-click to paste code that supposedly ‘fixed’ the problem — hence the attack name. Instead of a fix, though, users were unwittingly installing malware — in that case, it was the Vidar stealer. Related:[Questions Swirl Around ConnectWise Flaw Used in Attacks](/remote-workforce/questions-swirl-connectwise-flaw-attacks)
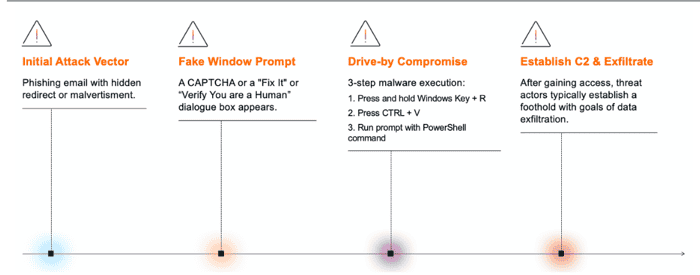The standard ClickFix infection routine takes place in the browser. Source: Darktrace Loading…==========Since April 2024, untold variations of the social engineering tactic have come to light, ultimately delivering a range of malicious binaries, from RATs and backdoors to cryptominers and ransomware. The lures vary, too, with threat actors asking watering-hole targets to, say, [update their browser plug-ins](https://www.darkreading.com/endpoint-security/swarms-fake-wordpress-plug-ins-infect-sites-infostealers) (thus delivering credential-harvesters); or in the case of [North Korea’s Lazarus APT](https://www.darkreading.com/cyberattacks-data-breaches/lazarus-apt-clickfix-bandwagon-attacks), luring job-seekers to fake interview sites. There, victims were asked to enable their cameras for the interviews, only to receive a supposed ‘error message’ and a prompt to click to ‘fix’ it — which resulted in the download of either the FrostyFerret password stealer or the GolangGhost backdoor. ‘The goals of ClickFix campaigns vary depending on the attacker,’ says Nathaniel Jones, vice president of security and AI strategy at Darktrace. ‘The aim might be to infect as many systems as possible to build out a network of proxies to use later. Some attackers are trying to exfiltrate credentials or domain controller files and then sell to other threat actors for initial access. So there isn’t one type of victim or one objective — the tactic is flexible and being used in different ways.’ Related:[Chrome Drops Trust for Chunghwa, Netlock Certificates](/remote-workforce/chrome-drops-trust-chunghwa-netlock-certificates)ClickFix Gains Broad Threat Actor Appeal—————————————-This Swiss Army knife approach to saddling victims with malware is one reason for cyberattackers to love ClickFix — but they’re also enamored by its stealth. For instance, Darktrace’s analysis showed that after a victim clicked to fix whatever the purported issue was, a malicious PowerShell command was executed in pretty much every case it investigated.’As our defenses have evolved and we have gotten better at blocking phishing email attachments that launch malicious code, the threat actors have evolved their techniques to find more creative ways to manipulate users into executing code,’ says James Maude, field chief technology officer at BeyondTrust. ‘In this case, using a combination of social engineering and [living-off-the-land binaries (LoLBins)](https://www.darkreading.com/cyberattacks-data-breaches/leveraging-behavioral-analysis-to-catch-living-off-the-land-attacks), which makes it difficult to defend against — the user simply launches PowerShell commands rather than a malicious binary that might be detected by an endpoint detection and response (EDR) solution.’ Darktrace pinned down other stealth tactics, too. After executing the PowerShell command, threat actors initiate external communication with their command-and-control (C2) servers and download a numerically named file.Related:[LummaC2 Fractures as Acreed Malware Becomes Top Dog](/remote-workforce/lummac2-fractures-acreed-malware-top-dog)’Numeric files like this are often intentionally nondescript and associated with malware,’ the Darktrace report said. ‘Further investigation into the file revealed that it contained additional malicious code designed to further exploit remote services and gather device information.’After that, the attackers ultimately executed yet more malicious code, exfiltrated data, and scanned for additional internal system information, the researchers noted — but only after being thoroughly nested inside victims’ networks.’This is a widespread campaign,’ according to Darktrace’s Jones. ‘We’ve seen ClickFix used across different regions and industries, and it’s becoming more frequent. We’re seeing a wide range of threat actors — including nation-state groups — incorporating it into their operations because of its efficacy. Because it is easy to execute and adapt, we expect to see more of it going forward.’An Evolution of Social Engineering———————————-ClickFix is effective primarily because it tricks targets into performing seemingly harmless, everyday actions that they’re unlikely to question, because they’re so used to seeing messages and notifications.As a perfect example, SlashNext researchers found that ClickFix attackers have cloned the Cloudflare Turnstile CAPCHA-like interface. They observed malicious and compromised sites serving up the message, ‘Checking if the site connection is secure — Verify you are human’ — just like a real Cloudflare page would. If targets click the fake Turnstile checkbox, a prompt appears asking them to cut and paste a bit of code and hit Enter, which deploys a hidden PowerShell command that kicks off a malware installation.
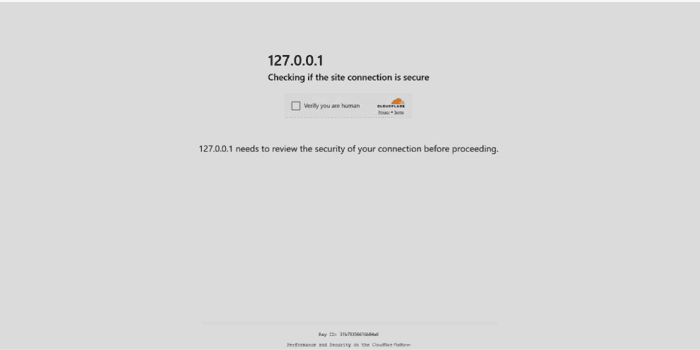The fake Cloudflare page shown at the start of the attack. Source: SlashNextSimilarly, Cofense reported a fake CAPTCHA that pops up after victims click on a bogus Booking.com link. After users ‘verify,’ they’re sent a one-time code to plug in, which is actually a PowerShell command that leads to malware deployment. The approach, and ClickFix in general, represents a significant innovation in the world of phishing, according to Jones, because unlike an email asking someone to click on a typosquatted link that can be easily checked, the entire attack takes place inside the browser.’ClickFix is notable because it shows how social engineering is evolving to rely more on trusted, everyday user behavior,’ he explains. ‘Attackers are getting users to do the work for them instead of exploiting software directly. They’re using websites people trust — like Google Chrome or Facebook.’And while it’s an innovative spoof, SlashNext uncovered a bigger takeaway when investigating the Turnstile clone itself: It’s a custom ClickFix implementation being sold as a commodity in the form of a ready-to-deploy module in underground forums. That signals a new wrinkle for the phishing kit economy that could lead to all manner of innovative, ‘Frankenstein’ attack chains that users won’t immediately see as suspicious.’Instead of [full kits](https://www.darkreading.com/remote-workforce/phishing-kit-darcula-gets-major-ai-upgrade), we’re now seeing specialized payloads sold as standalone modules,’ says Daniel Kelley, security researcher at SlashNext. ‘That makes attacks more flexible and lowers the skill requirement for threat actors. The packaging shows where phishing infrastructure is headed — toward more modular, scalable delivery.’He adds, ‘What we found was a packaged payload being sold for future use. That suggests it’s likely to be adopted by multiple actors over time.’All of this means that businesses need to evolve their phishing defense beyond email filters and standard employee education, according to Kelley.’The compromise happens after the click, not before,’ he explains. ‘Businesses should treat phishing as a multistage process and focus on what happens in the browser, not just what lands in the inbox.’ Some specific recommendations include: * Use[phishing-resistant multifactor authentication](https://www.cybersecuritydive.com/news/cisa-phishing-resistant-mfa/635763/), such as hardware keys* Monitor and restrict redirect behavior and suspicious script execution* Track domain abuse, especially involving your brand or login portals* Educate users on real-world phishing flows, not just basic link hygiene* Deploy independent layers of security across endpoints, networks, and the cloud.* Network segmentation can help limit movement if an attacker gets in* Identity and access controls should be in place to reduce exposure* Implement logging to track unusual behavior* Have an incident response plan, because when these attacks do succeed, the response time mattersIt’s also key for defenders to understand the worst-case scenario for these attacks, according to BeyondTrust’s Maude.’Generally, the goal of these phishing campaigns is to perform credential harvesting to gain further access to accounts and identities that will enable privileged access to other systems, so having a [robust identity security posture](https://www.techtarget.com/searchsecurity/feature/identity-new-perimeter-enterprise-security) based on the principle of least privilege is essential,’ he says. ‘It is also important to understand the blast radius in the event of compromise. Just because the phishing started on the endpoint doesn’t mean it is contained there, and active browser sessions or stored credentials may have enabled them to pivot into the cloud and SaaS apps. This is why it is important to take an identity-centric view of breaches and gain visibility over all the systems a user can access.’ [](https://www.linkedin.com/sharing/share-offsite/?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](http://www.facebook.com/sharer/sharer.php?u=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](http://www.twitter.com/intent/tweet?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing)[](https://www.reddit.com/submit?url=https://www.darkreading.com/remote-workforce/cutting-edge-clickfix-snowball-phishing&title=Cutting-Edge%20ClickFix%20Tactics%20Snowball%2C%20Pushing%20Phishing%20Forward)[](mailto:?subject=Cutting-Edge ClickFix Tactics Snowball, Pushing Phishing Forward&body=I%20thought%20the%20following%20from%20Dark%20Reading%20might%20interest%20you.%0D%0A%0D%0A%20Cutting-Edge%20ClickFix%20Tactics%20Snowball%2C%20Pushing%20Phishing%20Forward%0D%0Ahttps%3A%2F%2Fwww.darkreading.com%2Fremote-workforce%2Fcutting-edge-clickfix-snowball-phishing) About the Author—————- [Tara Seals](/author/tara-seals) Managing Editor, News, Dark Reading Tara Seals has 20+ years of experience as a journalist, analyst and editor in the cybersecurity, communications and technology space. Prior to Dark Reading, Tara was Editor in Chief at Threatpost, and prior to that, the North American news lead for Infosecurity Magazine. She also spent 13 years working for Informa (formerly Virgo Publishing), as executive editor and editor-in-chief at publications focused on both the service provider and the enterprise arenas. A Texas native, she holds a B.A. from Columbia University, lives in Western Massachusetts with her family and is on a never-ending quest for good Mexican food in the Northeast. [See more from Tara Seals](/author/tara-seals) Keep up with the latest cybersecurity threats, newly discovered vulnerabilities, data breach information, and emerging trends. Delivered daily or weekly right to your email inbox. [Subscribe](https://dr-resources.darkreading.com/c/pubRD.mpl?secure=1&sr=pp&_t=pp:&qf=w_defa3135&ch=drwebbutton) More Insights Webinars* [DevSecOps Achievement Unlocked](https://dr-resources.darkreading.com/c/pubRD.mpl?secure=1&sr=pp&_t=pp:&qf=w_palo315&ch=SBX&cid=_upcoming_webinars_8.500001559&_mc=_upcoming_webinars_8.500001559)Jun 19, 2025[More Webinars](/resources?types=Webinar) Events* [-[Virtual Event-] Strategic Security for the Modern Enterprise](https://ve.informaengage.com/virtual-events/strategic-security-for-the-modern-enterprise/?ch=sbx&cid=_session_16.500334&_mc=_session_16.500334)Jun 26, 2025* [-[Virtual Event-] Anatomy of a Data Breach](https://ve.informaengage.com/virtual-events/an-anatomy-of-a-data-breach-and-what-to-do-if-it-happens-to-you/?ch=sbx&cid=_session_16.500333&_mc=_session_16.500333)Jun 18, 2025* [-[Conference-] Black Hat USA – August 2-7 – Learn More](https://www.blackhat.com/us-25/?_mc=we_bhas25_drcuration&cid=_session_16.500330)Aug 2, 2025[More Events](/events)You May Also Like*** ** * ** ***[Remote WorkforceCritical Ivanti vTM Bug Allows Unauthorized Admin Access](https://www.darkreading.com/remote-workforce/critical-ivanti-vtm-bug-unauthorized-admin-access) [Remote WorkforcePolyfill.io Supply Chain Attack Smacks Down 100K+ Websites](https://www.darkreading.com/remote-workforce/polyfillio-supply-chain-attack-smacks-down-100k-websites) [Remote Workforce’ONNX’ MFA Bypass Targets Microsoft 365 Accounts](https://www.darkreading.com/remote-workforce/onnx-microsoft-365-accounts-mfa-bypass) [Remote WorkforceCut -& Paste Tactics Import Malware to Unwitting Victims](https://www.darkreading.com/remote-workforce/cut-paste-tactics-import-malware)
Related Tags:
NAICS: 54 – Professional
Scientific
Technical Services
NAICS: 517 – Telecommunications
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 52 – Finance And Insurance
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 522 – Credit Intermediation And Related Activities
NAICS: 51 – Information
ConnectWise
ScreenConnect
Associated Indicators:


