Share with your network! April 11, 2025 Tim Bedard *The modern workplace has expanded beyond email. Attackers now exploit collaboration tools, supplier relationships and human trust to bypass defenses and compromise accounts. This five-part blog series raises awareness around these shifting attack tactics. And it introduces our holistic approach to protecting users.*In Part 1, we examined [how one determined attacker thrives](/us/blog/email-and-cloud-threats/relentless-cybercriminal-workplace-attacks ‘The Expanding Attack Surface: How One Determined Attacker Thrives in Today’s Evolving Digital Workplace’) in today’s evolving digital workplace. Now in Part 2, we take a closer look at why platforms like Microsoft Teams, Slack and Zoom are the new front line for cyberattacks—and what you can do to protect them.### The new cyber battleground: messaging and collaboration platformsOrganizations today rely on messaging and collaboration tools to boost productivity and connect distributed teams. However, as quickly as businesses adopt these platforms, cybercriminals are finding new ways to exploit them. Threats are no longer confined to email. Attackers now target these tools with [phishing](/us/threat-reference/phishing ‘Phishing’), [malware](/us/threat-reference/malware ‘Malware’) and account takeovers. So, why are they attacking these digital channels? It’s simple—this is a new vector to target your people.To keep pace with evolving threats, organizations must secure all platforms with the same level of protection that they use for email.*Attackers are relentless, and their focus is clear—people.*### How attackers exploit these platforms, and why they’re so vulnerableSurprisingly, most messaging and collaboration platforms don’t have native security capabilities to detect and block malicious URLs via phishing and other attacks. This leaves businesses exposed when employees use various platforms:* **Messaging apps,**like Messenger, WhatsApp and Snapchat* **Collaboration tools,**like Microsoft Teams, Slack and Zoom* **Social media,** like LinkedIn, Instagram, Facebook and XAs a result, cybercriminals exploit these platforms, using them to launch sophisticated attacks. They do this by taking advantage of common employee behaviors:* **Trust in internal platforms**. Employees often assume that messages sent in collaboration tools are legitimate because they appear to come from colleagues. Attackers use this trust to impersonate executives or IT teams.* **Pressure of instant communication.** Unlike email, messaging apps encourage quick responses. This makes it more likely for employees to act without verifying links or requests. Attackers take advantage of this urgency to pressure users into sharing credentials, making payments or clicking malicious links.### Example of an attack on Microsoft TeamsWhat follows is a recent, real-world example of how attackers are targeting people via Microsoft Teams.#### Step 1: The distraction—subscription email bombingIt starts with chaos. A subscription email bombing attack overwhelms the user’s inbox with thousands of bogus emails, creating confusion and distraction.#### Step 2: The deception—fake IT supportAmid the chaos, a [bad actor strikes](/us/threat-reference/threat-actor ‘Threat Actor’). Posing as IT support, they send a message with an urgent request, along with a malicious URL to ‘fix’ the issue.Here is an example of what a bad actor’s message might say:’Your account security has been compromised. Click here to verify your credentials immediately so that I can fix your email bombing issue.’#### Step 3: The click—credentials stolenBecause the user believes that the IT support message is a legitimate request, they click the link and enter their credentials—unknowingly handing them over to the attacker.#### Step 4: The breach—full access gainedNow, the attacker has full access—not just to the user’s account but to the entire organization. This puts critical data and systems at risk.### Secure your messaging and collaboration applicationsWe’ve seen a real-world example of how attackers are exploiting Microsoft Teams. Now let’s explore how you can secure your messaging and collaboration applications with Proofpoint Collab Protection.Proofpoint Collab Protection extends phishing protection against malicious URLs that are delivered via any messaging, collaboration or social media platform. Powered by our industry-leading threat Intelligence platform Proofpoint Nexus,^®^ Collab Protection inspects the reputation of URLs in real time. Plus, it blocks malicious URLs at click-time. This approach ensures that your users are protected anywhere, anytime from advanced phishing attacks.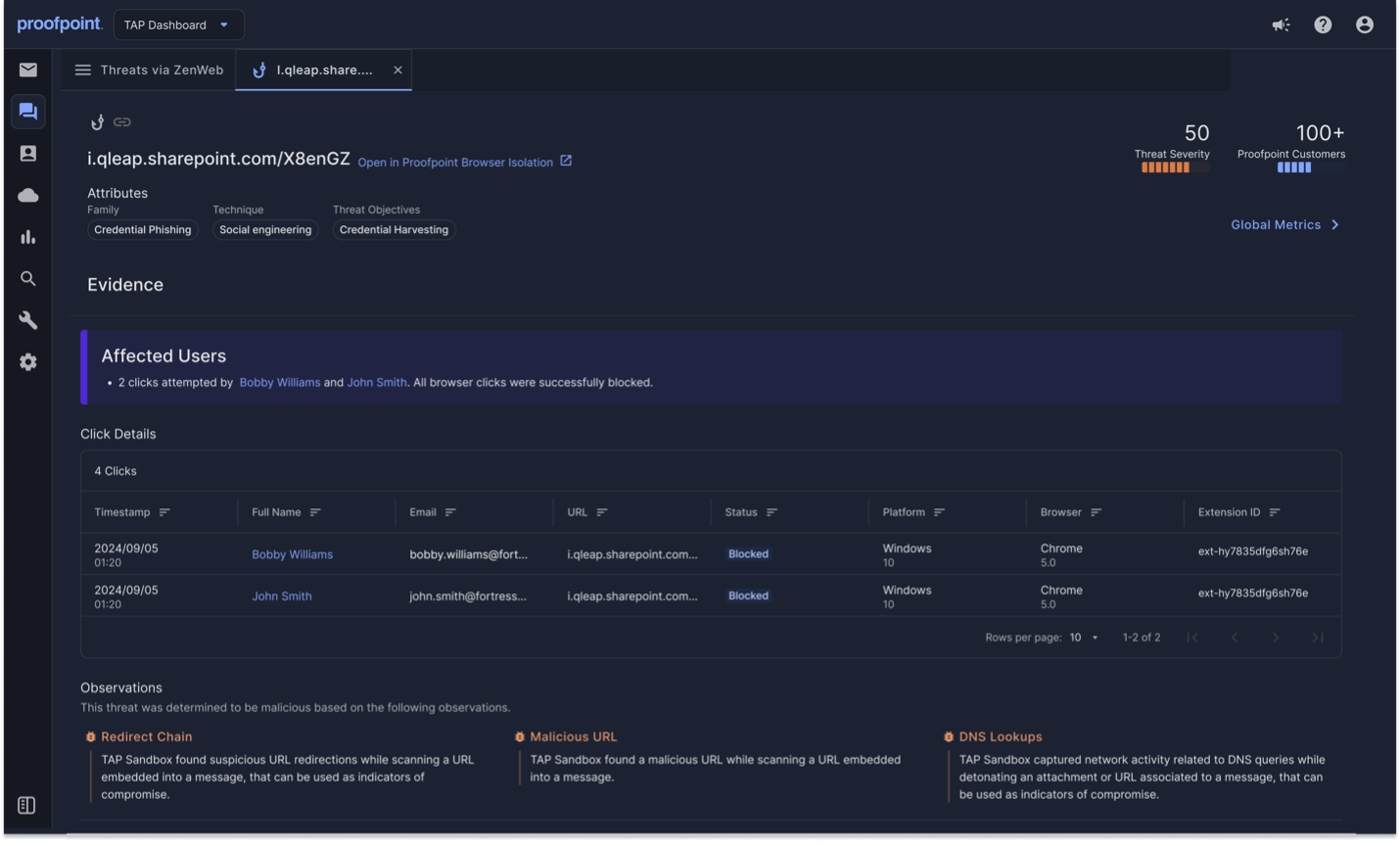*Proofpoint Collab Protection phishing threat forensics.*#### Protect people from malicious URLsHere’s how it works. When an employee clicks on a suspicious link that’s shared in a messaging or collaboration app, Collab Protection automatically evaluates how safe the link is. It does this by checking the URL’s reputation in real time. If the URL is deemed malicious, it automatically blocks access to the URL. This prevents the user from interacting with harmful websites or content. It doesn’t matter if URLs are accessed on a desktop or mobile device.#### Gain multichannel phishing threat visibilityCollab Protection provides comprehensive, real-time insights. When an employee clicks on a suspicious link that’s shared through a messaging or collaboration app, it automatically identifies the user who clicked on the URL. What’s more, it pinpoints the device that the URL came from (desktop or mobile) and whether the malicious link was successfully blocked.Collab Protection unifies security insights from email, messaging and collaboration apps. With multichannel threat visibility, security and IT teams can track and respond to phishing threats faster across multiple digital channels, including email, Microsoft Teams, Slack, Zoom and even text messages.Having explored how Proofpoint Collab Protection can secure your messaging and collaboration applications, let’s now look at some recommended best practices for enhancing the security of these platforms.### Recommended best practices for securing your messaging and collaboration platformsAs the attack surface widens, so do your gaps in security. Here are some best practices to help fortify your messaging and collaboration platforms in a fragmented digital world:* **Phishing protection that extends beyond email.**Phishing doesn’t stop at email—so why should your protection? To keep your people safe, you need security to work everywhere that they work. Look for protection that delivers real-time URL reputation inspection so that you can block malicious links at click-time, no matter where they appear—email, messaging or collaboration apps. Don’t just protect email—protect every channel that attackers exploit.* **Enhanced threat intelligence and telemetry.** You can prevent potential [breaches](/us/threat-reference/data-breach ‘Data Breach’) by proactively detecting **phishing threats and** identifying and blocking malicious URLs **before they are clicked** . Make sure your protection includes **continuous global updates so that it can** adapt in real time to evolving attack tactics. This ensures that your organization stays ahead of emerging threats. Also, a solution that classifies**threats accurately** minimizes false positives. This allows security teams to focus on real risks without being unnecessarily disrupted.* **Broad coverage for messaging and collaboration tools.** You want**universal protection** with an **application-agnostic deployment approach. This will ensure that** all your messaging and collaboration platforms are secured on Day One. R**eal-time phishing threat prevention** should work seamlessly across applications and devices, eliminating security gaps without complex integrations. This approach ensures **faster deployment, lower IT overhead** and comprehensive threat defense without disrupting your people’s productivity.* **Multichannel threat visibility.** Phishing attacks don’t stay in one place—neither should your visibility. When you have enhanced phishing threat activity reporting across all digital channels, you gain a clear, real-time view of the attacks that are targeting your organization. This accelerates threat investigation, helping you respond faster and more effectively. By staying ahead of phishing threats wherever they appear, you can reduce risks and better protect your people and business.* **Anywhere, anytime protection.** Phishing threats don’t wait for office hours and neither should your [collaboration protection](/us/products/collab-protection ‘Collab Protection’). Real-time phishing threat protection ensures that your people stay secure whether they’re in the office, at home or on the go. Seamless security across desktop and mobile devices ensures that no matter where they work, they’re protected from evolving threats—anywhere, anytime.### Protect your people with human-centric securityAs digital workspaces expand, attackers continue to target people. While email remains the primary threat vector, cybercriminals are exploiting new channels like messaging collaboration platforms, cloud apps and file-sharing services. This has created a fragmented security landscape with disconnected point products, resulting in higher operational costs and increasing security gaps. This is where Proofpoint can help.Proofpoint Prime Threat Protection provides a single, comprehensive solution to defend against all human-centric threats, both current and emerging. It combines a wide range of security protections to help you maximize threat prevention. It features:* **Accurate threat detection**—Helps prevent the widest variety of threats* **AI-powered account protection**—Defends against account takeovers and compromised supplier accounts* **Risk-based targeted training**—Guides users to make safer choices when faced with threats* **Phishing protection across platforms**—Blocks malicious links from multiple platforms* I**mpersonation protection**—Protects your brand reputation from being abused* **Human risk management**—Identifies high-risk users and automates adaptive security controlsWith Proofpoint Prime, you can better protect your people and business by reducing alert fatigue with highly accurate threat detection, improved efficiency through detailed risk insights and automated security workflows. Combined with pre-built integrations and shared threat intelligence, your security and IT teams can accelerate deployments while reducing costs by eliminating fragmented point solutions across your organization.Learn more about [Proofpoint Prime](/us/products/threat-protection ‘Threat Protection’).### **Stay tuned to learn more**In our next blog, we’ll explore the risks of [impersonation](/us/threat-reference/impersonation-attack ‘Email Impersonation Attacks’) and [domain spoofing](/us/threat-reference/domain-spoofing ‘Domain Spoofing’)—and how to protect against these threats.
Related Tags:
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Impersonation
Blog: Proof Point
Compromise Accounts
Phishing: Spearphishing Link
Associated Indicators:


